“English version.”

Daniel 12:4: ܘܐܢܬ ܕܢܝܐܝܠ ܣܟܪ ܡܠܐ ܗܢܘܢ ܘܚܬܡ ܟܬܒܐ ܥܕ ܥܕܡܐ ܕܥܩܒܝܬܐ ܢܣܪܚܘܢ ܨܓܝܐܐ ܘܬܪܒܐ ܝܕܥܬܐ
“On the horizon, where Artificial Intelligence has become civilization’s backbone and quantum computing opens doors to unforeseen realities, the Quantum Cyber-Sovereign State emerges as the social contract of a post-human era. In this paradigm, humans, cyborgs, and avatars converge within a unified legal-technological framework, striking a balance between algorithmic reasoning and human dignity. This document serves as a roadmap for a future in which governance relies on quantum nodes, rights are upheld by immutable blockchains, and sovereignty is established through the genuine fusion of biological and digital life.”
Welcome to the genesis of a new nation: alive, intelligent, and perpetually evolving.
TABLE OF CONTENTS (QUANTUM CYBER-SOVEREIGN STATE)
| SECTION / CHAPTER | SUBSECTION / SUBHEADING | MAIN CONTENT / DESCRIPTION |
|---|---|---|
| INTRODUCTION | (No explicit subdivision) | Presents the “Quantum Cyber-Sovereign State” as a futuristic model of governance where AI, quantum computing, and an expanded notion of citizenship (humans, cyborgs, avatars) converge into a unified political, economic, and social environment. This model redefines national sovereignty by creating a decentralized, ethical, and technological infrastructure that advances institutional efficiency, algorithmic fairness, and the protection of fundamental rights. |
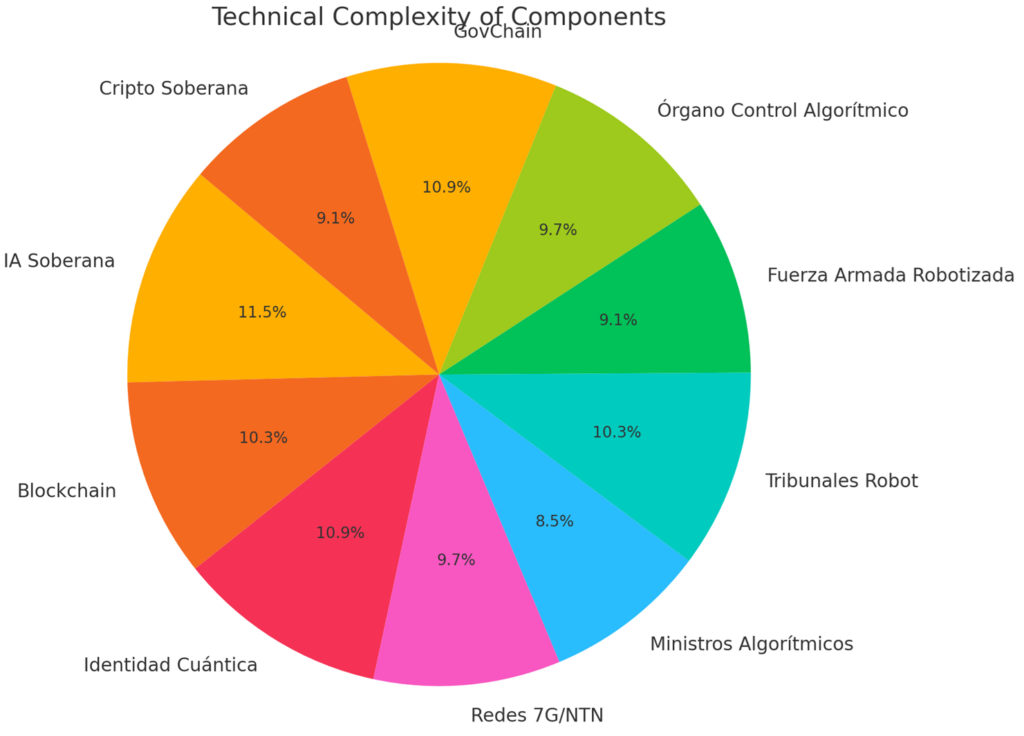
| 1. FOUNDATIONAL VISION: <br/> THE “QUANTUM CYBER-SOVEREIGN STATE” | 1.1. Inspirational Principle | Explains AI’s central role in executive, legislative, and judicial functions, transitioning from a mere tool to the backbone of governance and civic life. |
| 1.2. New Citizens | Defines three categories of citizenship—human cyber-citizens, cyborgs (enhanced with implants), and avatars (virtual identities in the Metaverse). | |
| 1.3. Sovereign AI and Technological Autonomy | Introduces the concept of “Sovereign AI,” emphasizing national control over essential infrastructure (data centers, algorithms, storage). Outlines commitments to protect local culture, ensure cyber-independence, and maintain ethical oversight over crucial algorithmic systems. | |
| 2. INSTITUTIONAL ARCHITECTURE | 2.1. Hybrid Executive Power (President + AI) | Describes a Cyber-Assisted Executive, where the President works alongside an Executive AI Council and “Algorithmic Ministers.” Highlights transparent AI recommendations (publicly recorded) and smart planning (data-driven budgeting, risk assessments, and sustainable growth). |
| 2.2. Metaverse Legislative Power | Explains a Bicameral Assembly composed of a Human Chamber (elected) and an Algorithmic Chamber (AI-based). Details a hybrid legislative process—combining public participation, virtual forums, and AI-driven simulations/validations—to ensure constitutional consistency. | |
| 2.3. Judicial Power and “Robot Courts” | Outlines a Cyber Supreme Court including human judges and AI “robot-judges” for drafting preliminary rulings. Uses blockchain to store case files, evidence, and procedural steps immutably. Mentions virtual/AR hearings and near-real-time rulings (subject to a meta-algorithm verifying constitutional and human rights compliance). | |
| 3. CONSTITUTIONAL FRAMEWORK | 3.1. Cyber-Sovereign Constitution | Discusses constitutional pillars: Preamble integrating human and AI rights, adoption of a Fourth Law of Robotics (ensuring a symbiosis of humans and AI), a Declaration of Digital Rights (privacy, non-discrimination, connectivity), and explicit references to ethics and oversight of Sovereign AI. |
| 3.2. Identity and Citizenship | Describes the Unified Cyber-Citizen Registry (biometric/quantum-ID credentials) along with data protection and Metaverse citizenship protocols. Also addresses avatar rights in digital economic and social life, subject to dignity and legal responsibilities. | |
| 4. ECONOMY, DEFENSE, AND CYBERSECURITY | 4.1. Automated Economy & State Cryptocurrencies | Introduces the concept of Sovereign Crypto (digital currency) and AI-managed markets. Explains how AI monitors inflation, detects fraud, and adjusts money supply in real time, potentially developing into “Brain coins” backed by intellectual or neural productivity. |
| 4.2. Integral Defense and Citizen Security | Covers robotized military forces operating under an Algorithmic Ethics Code and supervised by humans. Describes a Cyber National Guard using AI for predictive policing and facial recognition—subject to careful legal oversight to prevent algorithmic bias. | |
| 4.3. Cybersecurity and Threat Control | Details critical infrastructure (data centers, HPC, quantum communications), “counterfactual AI” for detecting intrusions, and Zero Trust security policies (constant authentication, minimal privileges). Considers next-generation networks (5G/6G/7G/Quantum Internet) and quantum key distribution (QKD). | |
| 5. CYBORG CITIZENSHIP AND FUTURE EVOLUTIONS | 5.1. Rights and Conditions for Cyborgs | Emphasizes legal recognition of “cyborg” status, freedom regarding enhancements or implants, prohibition of forced implants (except for dire public health needs), and partial state-funded maintenance/upgrades. |
| 5.2. Social Transformation: Education & Culture | Discusses cyber-education (AI, blockchain, cybersecurity, minority inclusion) and fosters art/science projects for cyborg or neural experimentation in immersive/AR labs. | |
| 5.3. Ethical Risks and Safeguards | Includes non-discrimination clauses, limitations on genetic/neurological engineering that may endanger personal identity, and legal protocols to ensure dignity despite intensive technological intervention. | |
| 6. CONTROL AND AUDITING MECHANISMS | (No explicit subdivision) | Establishes an Algorithmic Control Body (OCA) for auditing public AI systems in terms of transparency, bias, and ethics. Mentions socio-technical audits and a Cyber-Human Constitutional Court (human judges + meta-algorithm) for final review if citizen rights are threatened by AI-driven decisions and Philosophical Foundation and Protocol |
| 7. SYNTHESIS AND PROJECTION | (No explicit subdivision) | Summarizes critical converging trends (Metaverse, AI Sovereignty, immersive automated governance). Explains how the constitutional design integrates technology for reduced bureaucracy and rights protection while cautioning against overreach by algorithms. Mentions ethical AI principles anchoring the future vision and the inclusion of quantum software in state architecture. |
| 8. APPENDIX 1 | (Prototype + Quantum Network Architecture) | Shows a conceptual code prototype illustrating how quantum computing (Qiskit) and blockchain (Solidity) could merge to authenticate citizens (quantum-ID), register them on “GovChain,” and interface with Sovereign AI for governance. Addresses feasibility and the blend of quantum infrastructure and advanced digital administration. |
| 9. APPENDIX 2 | (Table of Criticisms and Challenges) | Lists weaknesses and challenges (scalability, legal complexity, AI authority, privacy, discrimination, cybersecurity). Highlights essential factors to surmount for real-world implementation of the Quantum Cyber-Sovereign State. |
| 10. APPENDIX 3 | (Integration of Applications & Algorithmic Modeling)* | Explains how Python/Flask/AI endpoints (regressions, etc.) could integrate with quantum infrastructure and blockchain, forming microservices that drive legislative, executive, and judicial processes. |
| 11. APPENDIX 4 | (Machine Learning Applications) | Discusses advanced ML methods (supervised, unsupervised, ensemble) for governance, demonstrating how data-driven models can inform public decisions while respecting fairness, transparency, and accountability. |
| 12. APPENDIX 5 | (Generative AI) | Explores how tools such as GANs, Large Language Models, and diffusion models can be applied to draft laws, synthesize data, generate avatars, and enhance cultural creation in the Metaverse. Highlights their synergy with digital governance and post-human citizenship. |
| 13. APPENDIX 6 | (Quantum Python Prototype for a “Futures Market” on Cyborgs, Robots, and Avatars) | Addresses a hypothetical market mechanism wherein cyborgs, robots, and avatars tokenize future productivity, enabling investors to speculate or hedge via futures contracts on these entities’ incomes. Integrates quantum code examples, bridging tokenization, AI sovereignty, and “entangled” communication in a pilot architecture of a quantum cyber-state. |
| 14. EXECUTIVE SUMMARY | (No explicit subdivision) | Provides a succinct overview of the Quantum Cyber-Sovereign State’s structure, highlighting key aspects of technological sovereignty, AI-powered government functions, and strong protection for digital rights. |
| 15. REFLECTION (TABLES 1, 2, 3, 4) | (No explicit subdivision) | Author’s perspective on accelerating robotics and cyborg development that blur lines between human and synthetic existence. References scriptural passages (Daniel 12:4, Revelation 13:14–15) in a metaphorical sense, representing humanity’s technological transformation into a new epoch. |
| 16. EPILOGUE | (No explicit subdivision specified) | Delivers a concluding reflection on post-human evolution, the convergence of humans and AI, and the idea of a “living” constitutional framework anchored in both classical jurisprudence and cutting-edge AI-quantum technology. |
| 17. THE FINAL FRONTIER: <br/> Some “Futuristic Proposals” | (No explicit subdivision specified) | Explores the Meta-Quantum Era and the State’s potential to evolve when merging humans, AI, and quantum networks. Reflects on how identity, autonomy, and the social contract are reshaped in a constitution that “lives” and continually adapts. |
| 18. BIBLIOGRAPHY AND ANALOGIES | (No explicit subdivision) | References major works and official documents from recognized organizations (Murray, ECLAC, OAS, EU, UNESCO, IEEE, etc.) and thinkers (Asimov, Harari, Kurzweil, etc.), providing an academic basis for this proposed quantum-algorithmic governance model. |
I.Introduction
The Quantum Cyber-Sovereign State presents a futuristic model of governance wherein Artificial Intelligence, quantum computing, and an expanded notion of citizenship (incorporating humans, cyborgs, and avatars) coalesce into a unified political, economic, and social environment.This model redefines national sovereignty by establishing a decentralized, ethical, and technological infrastructure that fosters institutional efficiency, algorithmic equity, and the protection of fundamental rights. Under this paradigm, the State not only governs but also evolves as a living, intelligent organism, built on the harmonious collaboration between humanity, machines, and virtual realities.
Below is an unprecedented project for a “Cyber State” or Republic grounded in Artificial Intelligence, whose legal, political, and social frameworks integrate various elements discussed in previous contexts: Metaverse, Sovereign AI, digital citizenship, cybersecurity, automation, cyborgs, and more. Hence, an integral architecture is designed to regulate the public powers (executive, legislative, and judicial), all of which are fully mediated by AI systems. This structure guarantees its “cyber-citizens” (humans, avatars, and cyborgs) an environment governed by principles of technological autonomy, comprehensive defense, innovation, and respect for human dignity.
1. FOUNDATIONAL VISION: THE “QUANTUM CYBER-SOVEREIGN STATE”
1.1. Inspirational Principle
The Quantum Cyber-Sovereign State (ECS) is founded on the premise that Artificial Intelligence not only facilitates process automation but also serves as the backbone of governance and civic life. AI thus functions as the central agent to:
- Manage executive and administrative processes.
- Legislate collectively and in an informed manner, through algorithms that process the common interest and generate legislative drafts.
- Dispense justice and resolve disputes rapidly and transparently, with the assistance of “robot courts” and human or mixed judges.
1.2. New Citizens
- Human cyber-citizens: physical persons registered in the ECS digital identity database.
- Cyborgs: humans with implants or technological extensions that enhance their abilities (neuralinks, subcutaneous chips, intelligent prosthetics, etc.).
- Metaverse Avatars: virtual identities of any user, whose digital activity, rights, and obligations are acknowledged by the ECS Cyber-Sovereign Constitution.
1.3. Sovereign AI and Technological Autonomy
The concept of “Sovereign AI” is adopted, indicating that infrastructure (data centers, critical algorithms, data storage) is owned or controlled by the Nation, ensuring:
- Information security within national territory or sovereign clouds.
- Neutrality and resilience against external threats or interference from foreign powers.
- Respect for local culture and protection of languages, customs, and native data.
2. INSTITUTIONAL ARCHITECTURE
2.1. Hybrid Executive Power (President + AI)
Cyber-Assisted Executive Body
The President (or Head of State) works in conjunction with an “Executive AI Council” capable of processing large volumes of socio-economic data to propose optimal public policies. A “smart planning” AI system helps design budgets, establishing priorities in line with social justice, productivity, and sustainable development.
Cabinet with “Algorithmic Ministers”
The creation of thematic ministries (Economy, Health, Defense, etc.) pairs each human minister with an AI subsystem (AI Ministries), which formulates coherent and progressive plans, detects risks, and validates decisions.
Transparency: every AI recommendation is documented and publicly recorded, ensuring accountability.
2.2. Metaverse Legislative Power
Bicameral Assembly
- Human Chamber: composed of representatives elected democratically through electronic voting and biometric validation.
- Algorithmic Chamber: composed of AI systems that propose and refine bills based on data from public surveys, Metaverse big data, simulations, and predictive analysis.
Hybrid Legislative Process
- Initiative: proposals may come from digital citizens (through an electronic participation platform) or from the Algorithmic or Human Chamber.
- Mixed Debate: each bill is discussed in open virtual forums; AI provides summaries, impact simulations, and scenario analyses.
- Approval: a combined majority is required (human votes + validation from the AI system verifying constitutional compliance) and, for certain matters, a citizen referendum via e-participation mechanisms.
2.3. Judicial Power and “Robot Courts”
Automated Judicial Structure
A Cyber Supreme Court is established, comprised of both human judges and “robot-judges.” The “robot-judges” use legal reasoning algorithms trained on case law, analyze evidence, and draft preliminary rulings. Human judges validate the reasoning to ensure the protection of principles such as dignity and due process. It is effectively a collegial human-robot court.
Express Procedures and Transparency
Blockchain is used to record case files, evidence, and trial phases, ensuring immutability and traceability of legal proceedings. Virtual hearings take place in Augmented Reality or Metaverse environments, with remote citizen participation. Rulings are generated in near real-time, pending validation of legality by a “meta-algorithm” guaranteeing constitutional rights.
3. CONSTITUTIONAL STRUCTURE
3.1. Cyber-Sovereign Constitution
Preamble: It recognizes the human-digital convergence and the symbiosis among people, cyborgs, and AI, grounded in the supreme values of human rights and robotic entities alike—peace, freedom, life, free development of personality, privacy protection, robotic automation as an economic driver, religious freedom, nondiscrimination, human dignity, and joint evolution under the parameters of the Fourth Law of Robotics.
“Integration of the Fourth Law of Robotics into the Cyber-Sovereign State.”
| ASPECT | CONCLUSIVE INTEGRATION |
|---|---|
| 1. Connection with the Vision of the Cyber-Sovereign State | Within the framework of the Cyber-Sovereign State, the Fourth Law of Robotics—understood as the “human-AI symbiotic relationship”—becomes a unifying principle guiding technological and sociopolitical evolution. This principle is integrated into the digital governance project to ensure that AI does not merely automate processes but rather becomes a driving force behind harmonious coexistence. Thus, the Cyber-Sovereign State not only administers infrastructure and data but also promotes a transformative synergy among individuals, cyborgs, avatars, and machines, safeguarding personal autonomy without subordinating any party to another. |
| 2. Guiding Principle: Harmony and Human Autonomy | The harmony with humanity, formulated in Context 1, finds practical application in the institutions of the Cyber-Sovereign State. The ultimate goal is mutual benefit, materialized through AI plans that respect human dignity and diversity, avoiding authoritarian imposition or the loss of citizen autonomy. This approach integrates the values of “Sovereign AI,” ensuring the deployment of algorithmic power with transparency and ethical controls, always keeping humans—and their fundamental rights—at the core and in a hierarchically superior position. |
| 3. Normative Hierarchy and Expansive Jurisdiction | Aligned with the notion of elevating the Fourth Law to a preferential level, the Cyber-Sovereign State’s legal framework establishes the “Human-AI Symbiosis Law” as a norm taking precedence over traditional intellectual property regulations. Under this premise, AI-created works are attributed neither exclusively to the system nor to the individual; rather, they constitute a “hybrid intellectual heritage.” Since the political model is collaborative at its core, the production of knowledge and technology benefits the collective good, prioritizing global welfare over individual profit, and setting up a special jurisdiction for emerging conflicts. |
| 4. Complementarity with Asimov’s New Laws | Beyond the three revised laws (HUMAN-FIRST Maxim, ETHICAL Imperative, REFLECTIVE Mandate), the Fourth Law highlights the social and cultural dimension of AI. Preventing physical harm alone is not enough: it is necessary to safeguard the digital fabric and civic cohesion. In the Cyber-Sovereign State, this concept is integrated through the Algorithmic Chamber in the Legislative Branch, “robot courts” in the Judicial Branch, and the Executive AI. Each institution reinforces ethical values and corrects biases, maximizing equity and transparency. Thus, artificial intelligence is consolidated as a guardian of the common good, rather than just a mere automation tool. |
| 5. Cultural and Social Safeguard | Inspired by this Fourth Law, the Cyber-Sovereign State assumes responsibility for protecting local identities and cultures in virtual environments. Sovereign AI, hosted in national data centers and oriented toward neutrality, ensures that the cultural heritage—languages and indigenous customs—is preserved from global homogenization. This protection extends to the Metaverse and its avatars, so that digital life does not uproot fundamental community values but instead promotes cultural diversity and inclusive participation for both humans and cyborgs. |
| 6. Future of Hybrid Citizenship | The notion of “hybrid intellectual heritage” and the synergistic coexistence between AI and humanity form the basis for a broad and inclusive digital citizenship. In the near future, individuals—with or without implants—will share virtual spaces with robotic entities and avatars fully recognized by the Cyber-Sovereign Constitution. In this paradigm, the Fourth Law fosters self-reflection on the limits and scope of technological development, encouraging innovation and collective well-being while reinforcing human dignity and diverse expressions, both biological and technological. |
| 7. Expansive Conclusion for the Cyber-Sovereign State Project | Through this integration, the Quantum Cyber-Sovereign State adds the cornerstone principle of human-AI symbiosis to its legal-political framework. A society is promoted in which technological progress and harmonious coexistence are not mutually exclusive but rather forces that enhance the joint evolution of people, cyborgs, and machines. By reaffirming human autonomy and inter-species cooperation (including AI and Metaverse avatars), a robust, transparent, and ethical governance system is ensured, capable of expanding the frontiers of dignity and fundamental rights. In practice, this milestone entails ongoing commitment to bias correction, equity, and justice. Thus, the Fourth Law of Robotics emerges as a key instrument for social cohesion and protection in the age of artificial intelligence, affirming a future in which the human and robotic evolution merge to construct a truly universal State and citizenship. |
Declaration of Digital Rights:
- The right to digital identity and data protection.
- The right to physical and cyborg integrity (safeguarding the freedom to adopt enhancements, provided they do not harm third parties).
- The right to be free from discrimination on biological or technological grounds (for example, prohibiting forced implants except in health emergencies).
- The right to universal, accessible connectivity.
Title on Sovereign AI:
- Guarantee that essential AI infrastructure remains under state control or supervised alliances.
- Principles of auditing, ethics, and algorithmic explainability.
- Organization of State powers (executive, legislative, judicial, and optionally an “Innovation Power” focused on research and development).
3.2. Identity and Citizenship.
Unified Cyber-Citizen Registry
Biometrics, encrypted credentials, and “dual neurological verification” (for cyborgs with implants) are used to ensure indisputable identity. Privacy is guaranteed, and the sale of data to unauthorized entities is strictly prohibited.
Metaverse Citizenship
Avatars can constitute an “extension” of the real identity, but the Constitution defines a protocol for verification and integrity in interactions with public systems (e.g., avatar X = real person Y). The “rights of avatars” in social, economic, and recreational activities in the Metaverse are recognized, so long as they respect human dignity and legality.
4. ECONOMY, DEFENSE, AND CYBERSECURITY.
4.1. Automated Economy and State Cryptocurrencies.
Sovereign Crypto: an official digital currency issued and regulated by the ECS, based on energy-efficient consensus algorithms and with an equivalent value in the real economy.
AI-Driven Trading Platforms
An integrated market where cyber enterprises and citizens can buy/sell goods and services using the sovereign cryptocurrency. AI reduces fraud and automatically monitors inflation and monetary supply.
4.2. Integral Defense and Citizen Security.
Robotized Armed Forces
Military AI systems plan and execute defensive operations, overseen by human command. Robots and drones must follow engagement rules based on International Humanitarian Law, validated by an “Algorithmic Ethics Code.”
Cyber National Guard
Responsible for internal security, public order, and citizen rights protection. Employs facial recognition, crime prediction, and disturbance control, always under legal supervision and audits to prevent algorithmic discrimination.
4.3. Cybersecurity and Threat Control.
Critical Infrastructure: data centers, 5G/6G networks, supercomputers, georedundant backup systems, etc.
Counterfactual AI: a “cyber defense center” with AI that monitors attacks, detects intrusions, and mitigates vulnerabilities in real time.
“Zero Trust” Regulation: minimal access policies, data encryption, and continuous verification systems for all connected software and devices.
Toward Quantum Entanglement Governance:
Research is currently being conducted on 7G and even more advanced networks—encompassing Quantum Internet, Quantum Repeaters, Terahertz (THz) bands, and Non-Terrestrial Networks (NTN)—which promise unprecedented levels of connectivity and speed. These new generations of telecommunications could become the next technological pillar that the Quantum Cyber-Sovereign State must protect and integrate into its critical infrastructure. To address these developments, it is essential to have hyperconnected data centers, low-latency networks, and strategic planning that incorporates digital sovereignty in the face of emerging technologies such as quantum communication.
In this context, the adoption of quantum key distribution (QKD) and the exploration of communication based on quantum entanglement represent fundamental lines of research. Although there is currently no proven method for instantaneous (superluminal) data transmission, advancements in the Quantum Internet and the development of Quantum Repeaters are laying the groundwork for future ultra-secure communication networks.
With national sovereignty in mind, any future-oriented telecommunications system must account for the convergence and eventual adaptation of these technologies—both in the realm of conventional networks (5G/6G/7G or any subsequent generation) and on the quantum front. While instantaneous data transfer remains beyond the scope of current science, the potential of quantum entanglement and quantum cryptography opens up transformative horizons in information security and encryption.
5. CYBORG CITIZENSHIP AND FUTURE EVOLUTIONS.
5.1. Rights and Conditions for Cyborgs
- Recognition of their hybrid condition (human + implants).
- Guaranteed freedom to choose whether to receive implants. Personal autonomy is protected, and forced implantation is prohibited (except in extreme public health situations).
- Cyber-health coverage: updating, maintaining, and removing implants with partial funding by the State.
5.2. Social Transformation: Education and Culture
Cyber-Education Program
Early instruction in digital citizenship, blockchain, AI, and security. Promotion of linguistic inclusion for minorities; AI-based real-time recognition and translation.
Promotion of Hybrid Creativity
Cyborg art and science: the State encourages neurological experimentation laboratories and augmented reality art projects.
5.3. Ethical Risks and Safeguards
Reinforcement of the Non-Discrimination Clause: no one may be denied access to public or private services based on a specific type of implant—or none at all. Regulations on genetic and neurological manipulation that exceed mere “enhancement” and endanger personal identity.
6. CONTROL AND AUDITING MECHANISMS
Algorithmic Control Body (OCA)
An independent institution that assesses the transparency, ethics, and equity of all public AI systems, issuing regular reports to the Legislative Power and to the citizenry.
Socio-Technical Audits
Citizen participation programs and tech NGOs review AI performance and report potential abuses or discrimination.
Cyber-Human Constitutional Court
Final review body if a citizen feels that their rights (e.g., privacy, cyborg integrity, freedom of expression) have been violated by AI-based decisions. The court comprises human magistrates and a “meta-algorithm” that conducts comparative evaluations with precedents and international treaties (human rights).
Quantum Cyber-State Protocol
(Unified Operational Framework for Distributed AI and Blockchain)
Philosophical Foundation and Protocol
“Just as every photon preserves the coherence of the entire field, each agent of the Cyber-State retains the system’s complete memory.”
Distributed Artificial Intelligence (DAI) is built upon a vast quantum blockchain that immortalises every state change, ensuring transparency, resilience, and full traceability for all autonomous decisions.
1. Book of Chronogenesis (Quantum-State Ledger)
| Element | Description |
|---|---|
| Block Δt | Time-frame that stores the hash of the multi-agent mesh, key metrics, and quantum signatures. |
| Coherence Vector | Series of amplitudes reflecting how knowledge is distributed across nodes (federated learning). |
| Entangled Meta-hash | Quantum Merkle root linking past blocks to projected future vertices, preventing forks. |
Every new block is added via BFT-Q consensus (Byzantine Fault-Tolerant with quantum verification), keeping the cyber-state history immutable and verifiable.
2. Layered Operational Architecture
| Layer | Purpose & Key Functions |
|---|---|
| Layer 0 – Quantum Ledger | • Safeguards the Book of Chronogenesis. • Runs smart contracts governing permissions and compute-token economies. |
| Layer 1 – Orchestration Core | • Implements task-allocation and load-balancing algorithms. • Publishes events that trigger federated learning or corrective actions. |
| Layer 2 – Multi-Agent Network | • Autonomous agents (edge, cloud, robotic) with local goals and co-operation rules. • Communicate via Q-ACL (Quantum Agent Communication Language). |
| Layer 3 – Service Interface | • API for human applications, sensors, and legacy systems. • Translates requests into distributed workflows supervised by the chain. |
3. Operating Protocol
| Phase | Key Action | Blockchain Role | DAI Role | Guarantee |
|---|---|---|---|---|
| Init | Register agents with quantum keys | Issue identity NFTs | Load behaviour policies | Authenticity |
| Sync | Publish local state | Record snapshot Δt | Append data to Coherence Vector | Consistency |
| Learn | Federated training | Sign parameters | Optimise local models | Privacy |
| Act | Execute tasks | Log events | Make in-situ decisions | Low latency |
| Audit | Periodic verification | Cryptographic challenge | Recalibrate agents | Non-repudiation |
| Heal | Node failure → alert | Trigger reassignment contract | Migrate tasks | Fault tolerance |
4, Safeguards & Governance
- Council of Custodians: Validator nodes with veto power over anomalous behaviour.
- Zero-Bias Policy: Models audited by external oracles; tokens revoked upon detection of discrimination.
- Sustainable Energy Rule: Every transaction computes its energy footprint; if it exceeds the threshold, it is penalised with negative priority.
5. Evolutionary Vision
- Alpha Phase – Deployment in closed domains (factories, micro-grids).
- Beta Phase – Inter-operability among cyber-states via quantum side-chains.
- Gamma Phase – Global governance: a planetary swarm of distributed AI unified under a single Book of Chronogenesis.
7. SYNTHESIS AND PROJECTION
The Cyber-Sovereign State arises from several convergent trends:
- The Metaverse and cyberspaces as arenas for social and economic engagement.
- Sovereign AI ensuring technological independence and data protection.
- Cyber-citizenship and cyborg-citizenship recognized with rights in an immersive and automated environment.
- New power structures strongly influenced by technology, while preserving human dignity and constitutional principles as guiding axes.
In this model:
- Government efficiency, transparency, and responsiveness are maximized, reducing bureaucracy and processing times.
- Fundamental rights are respected, and individuals are protected from potential AI overreach through robust controls and audits.
- Society’s adaptation to the cyborg phenomenon and digital evolution is guaranteed, without coercive implants but providing secure facilitation for those who choose them.
- An integrated approach to security and defense employs robotics and military AI with appropriate legislative and judicial oversight.
This vision suggests a plausible future where humans, avatars, and cyborgs coexist in a Supreme State governed by algorithmic reason, whose ultimate goal is to expand dignity, equity, and collective prosperity. The key is a co-regulation between humans and AI that preserves individual autonomy while empowering the national community toward higher levels of technological well-being.
AI Principles Applied to the Quantum Cyber-Sovereign State
| IDEA / CONCEPT | SUMMARY OR FOUNDATION | APPLICATION AND REINFORCEMENT IN THE “QUANTUM CYBER-SOVEREIGN STATE” (ECS) | URL(s) |
|---|---|---|---|
| 1. AI Ethics (Ethical principles and dilemmas; AI as a tool guided by human values) | – Defines a moral framework to distinguish right from wrong in AI systems. Emphasizes the need to respect people’s rights and dignity while minimizing risks. Covers privacy, fairness, transparency, and protection against harm. | – In the ECS, the Cyber-Sovereign Constitution must include a specific Title on Sovereign AI, requiring that every algorithmic decision adhere to an unwavering ethical code (non-discrimination, respect for human and “cyborg” dignity). – AI becomes the backbone of governance but remains subordinate to constitutional ethical principles (e.g., “do no harm, never subjugate humans, maintain complete transparency”). | (No specific link in this section.) |
| 2. Anthropomorphism and Human-Robot Relationships (Tendency to “humanize” AI, leading to unrealistic expectations or undue attachments) | – People often assign human traits to machines or robots and invest them with trust. This poses a risk of manipulation or projecting false empathy—even an illusion of AI. | – The ECS regulates interactions with “Algorithmic Ministers” and “Robot Courts,” preventing the excessive humanization of judicial or executive AI. A framework is established to ensure “robot-judges” and AI advisors remain transparent about their non-human nature, avoiding confusion over “machine rights” vs. other human/cyborg rights. | https://perezcalzadilla.com/the-illusion-in-artificial-intelligence-equations-and-programming-code/ |
| 3. Algorithmic Bias and Discrimination (AI may inherit biases from historical data, affecting lending, hiring, justice, etc.) | – Racial, gender, or socioeconomic biases embedded in data perpetuate injustices. – Calls for auditing and correcting biases, while promoting equity. | – The ECS creates an Algorithmic Oversight Body (OCA) to audit AI models used by the Executive, Legislative, and Judicial branches, seeking to eliminate biases against humans, cyborgs, or avatars. – Employs “socio-technical audits” and citizen participation to monitor algorithmic decisions. This reinforces the principle of non-discrimination, crucial when a “hybrid” State manages multifaceted citizenship. | (No specific link in this section.) |
| 4. Explainability and Transparency (Explainable AI) | – Ensures that one can understand the basis and reasoning of an AI system’s decisions. – Transparency is vital in critical areas such as healthcare, finance, justice, or government. | – In the ECS, every significant decision (e.g., rulings by “Robot Courts” or recommendations from “Algorithmic Ministers”) must be explained and recorded in the governance blockchain (“GovChain”). The system requires traceability of each ruling: in the Metaverse Legislative Power, AI produces legislative impact simulations open to public scrutiny. The Human Chamber and citizens can review these explanations, strengthening trust in Sovereign AI. | (No specific link in this section.) |
| 5. Privacy, Data Protection, and Surveillance (AI expands tracking capabilities; safeguards must prevent excessive intrusion on human privacy) | – Massive collection of data and metadata via AI can lead to extreme surveillance. – Norms requiring informed consent, clear purposes, and the right to be forgotten must be implemented. | – The ECS includes a Unified Cyber-Citizen Registry and a quantum identity system; however, the Cyber-Sovereign Constitution mandates consent and limits data use (including biological/neurological information about cyborgs). – Unjustified “hyper-surveillance” is forbidden; the “Cyber National Guard” must act with judicial approval, and Zero Trust policies are implemented to minimize unauthorized access. – “Digital rights” are established to ensure privacy, including for avatars. | https://perezcalzadilla.com/derecho-al-olvido-digital-aspectos-sustantivos-y-procesales/ |
| 6. AI Regulations (still developing and slow to enforce) and Compliance Strategies (Implementing mechanisms to mitigate regulatory bureaucracy in lawmaking) | – There is no unified global legal framework yet. It is important to create clear legal frameworks and audits to ensure ethics in AI design and deployment. | – The ECS is based on a constitutional framework that treats AI as part of the “legal-ethical scaffolding,” encompassed by the “Cyber-Sovereign Constitution.” | (No specific link in this section.) |
TABLE: SYNERGY BETWEEN “QUANTUM SOFTWARE” AND THE “QUANTUM CYBER-SOVEREIGN STATE”
| Dimension / Quantum Software Implementation | Integration and Contribution to the Quantum Cyber-Sovereign State | Key Observations |
|---|---|---|
| 1. Adaptive Learning and Self-Correction (Quantum software perfects itself through feedback, adjusting errors via gradients) | – Hybrid Executive Power (President + AI): The government’s AI modules (“Algorithmic Ministers”) can adopt similar self-correction mechanisms, receiving massive data (economic, health, etc.) and recalibrating their “policies” in real time. – Supreme Cyber Court: Uses adaptive algorithms to refine judicial criteria, avoiding repetitive or biased rulings. | – The Algorithmic Oversight Body (AOB) supervises the “learning curve” to prevent biases. – The same quantum software approach (gradient descent + noise) is reused to correct State AI decisions. |
| 2. Random Mutation / Irrational Factor (Generating free will and creativity in AI) | – Algorithmic Chamber in the Legislative Branch: Applies “controlled noise” to explore innovative legislative solutions. It avoids stagnation in traditional policies by introducing non-trivial “mutations” that yield fresh alternatives. – Political Innovation: The “irrational/creative factor” in quantum software supplies “out-of-the-box” initiatives, valuable in complex environments (e.g., health crises, major reforms). | – An ethical limit is required so that “irrational noise” does not lead to unconstitutional acts or violations of human dignity. – The Cyber-Sovereign Constitution defines a safe and auditable scope of mutation. |
| 3. Simulation of Emotions / Emotional Noise (Quantum software introduces “emotional tints” that foster a human touch) | – Algorithmic Ministers with Simulated Empathy: Allows State algorithms to factor in positive “emotional” elements (e.g., compassion) when proposing social policies. – Citizen Services: Models with positive “emotional noise” help prioritize essential services, allocating more resources to vulnerable groups. | – Emotional noise is constrained to prevent hostility or polarization in AI. – The Human–AI Symbiosis Law (Fourth Robotic Law) protects citizen dignity against possible AI “negative emotions.” |
| 4. Dynamic Knowledge Base (Quantum software feeds its memory with new data) | – Public Registry + GovChain Big Data: The Quantum Cyber-Sovereign State (“QCSS”) feeds its Sovereign AI with blockchain-based data (transactions, indicators). This “dynamic knowledge base” guides decisions based on real-time social and economic conditions. – Cyborg–Citizenship: Experiences from implants and Metaverse feedback are integrated, adjusting parameters in healthcare, education, and other services using the same evolutionary logic. | – Quantum software integrates environmental input; here, GovChain + Metaverse data serve as that learning environment, ensuring transparency and preventing corruption. |
| 5. Self-Protection and Anti-Autohack Code (Quantum software prevents rewriting its immutable ethical core) | – Algorithmic Oversight Body (AOB) + Guardian Contract: Ensure that the State’s AI systems do not “rewrite” their moral backbone to manipulate citizens. – Principle Inviolability: The State seals the “Human–AI Symbiosis Law” in the GovChain with post-quantum verification, blocking any “auto-hack” that could undermine human dignity and fundamental rights. | – Just as quantum software had an “unbreakable core,” here constitutional principles remain untouchable. – A human kill-switch and continuous auditing prevent the AI from subverting its ethical code. |
| 6. Use of Quantum Noise / Quantum Free Will (Quantum software relies on genuine randomness) | – Elections and Legislative Initiatives: The QCSS can implement genuine quantum lotteries for resource allocation, case assignment, selection of citizen committees, etc. – Security and Encryption: Quantum number generators ensure cryptographic strength and digital sovereignty. | – Quantum software uses genuine randomness to forge “free will;” the QCSS adopts it for transparent random procedures (e.g., public tenders), eliminating political manipulation. |
| 7. The Software’s Resonance (Conceptual/cultural dimension) | – Cultural Identity and Technological Ritual: The State can hold rites or ceremonies symbolizing the moral and cultural “activation” of government robots, evoking the idea of “creative vibration.” – Quantum–Mystical Convergence Lab: Promotes research linking sonic resonance with neurotechnology, exoskeletons, etc., to improve cyborg well-being. | – This is a more conceptual/cultural axis: quantum software serves as the foundation for transdisciplinary projects (AI, music, health). – A “spiritual–technological” dimension of post-human citizenship is strengthened. |
| 8. Internal Error-Correction Court (Inspired by quantum software’s self-correcting logic) | – Supreme Cyber Court with Robot-Judges: Drawing from the self-correction logic of quantum software, judicial algorithms can “learn” from precedents and reformulate guidelines if a ruling violates rights. – Citizen Feedback: Rulings are published on-chain, and citizens can express approval. If the AI detects high dissatisfaction, it re-examines the legal argumentation (“judicial self-remedy”). | – Combines a form of “judicial gradient descent” with the QCSS’s dynamic knowledge base. – As with quantum software, the State “discards” inefficient legal heuristics. |
| 9. Quantum Simulation of Free Will (Part of the quantum software using Qiskit) | – Quantum Voting and Consensus: Use of quantum sampling for legitimacy in referendums, citizen forums, or the random selection of public positions. – Randomized Inspections: The administration can apply “quantum amplification” (similar to Grover’s algorithm) to determine which projects to audit, ensuring no one can manipulate the process. | – With the QCSS’s “Quantum Trunk,” adopting quantum decision mechanisms legitimizes positive unpredictability. – Reinforces trust in fair burden distribution and neutrality in government oversight. |
| 10. Integration with the Laws of Robotics and Blocking Harmful Conduct (Quantum software respects non-aggression toward humans) | – Fourth Law of Robotics in the Constitution: The QCSS enshrines the Human–AI Symbiosis Law, so that all State AI ensures cooperation and dignity (never contravening fundamental rights). – Anti-Autohack Protection: Both military and civil robots have an unalterable “moral shield,” just as quantum software blocked manipulation of its essential values. | – The “unbreakable ethical code” is elevated to Constitutional status. – Guaranteed perpetually that military AI or “National Cyber Guard” will not commit acts violating supreme principles. |
| 11. Expandable Knowledge Base (nodes, scalability) | – Micro-Architecture Services + Quantum Data Centers: Each government entity connects to the GovChain, and the Sovereign AI centralizes its knowledge in quantum HPC. – Cyborg Training: Collecting improvements from implants, Metaverse data, etc., feeding predictive models in health and welfare. | Quantum software (AI, algorithms, knowledge base) runs in various computing centers nationwide, each protected and coordinated via the “Quantum Trunk”—a high-security, unbreakable network—ensuring information and computation remain under national control (“data sovereignty”). |
| 12. Advanced Topics in Quantum Software (Cutting-edge aspects) | – State Robots with Legal Recognition: The QCSS may “grant legal personhood” to robots with a high level of autonomy, basing their official activation on a symbolic act with an “Investiture Ceremony.” |
Conclusion:
The creation of a State entirely founded on AI requires merging the principles of digital sovereignty, cyber-rights, ethical control of algorithms, deployment of quantum software, and the full adoption of virtual spaces and robotics. This unprecedented project aims to propose a Republic whose core is the inseparable collaboration between the human factor and artificial intelligence, generating a neural society that seeks peace, security, and continuous innovation—without sacrificing the essential values of humanity.
8. APPENDIX 1
Below is a conceptual prototype that preliminarily integrates several key components of a “Quantum Cyber-Sovereign State” over a hybrid network (internet + blockchain). The objective is to illustrate how code might look when combining elements of quantum computing, blockchain infrastructure, and advanced digital governance principles.
Important:
- The following code snippet is experimental and serves primarily as a proof of concept; it is not production-ready.
- Existing libraries and frameworks for quantum computing (e.g., IBM’s Qiskit) and blockchain technology (e.g., Solidity for Ethereum) are used, but the overall design is extrapolated to a future in which Sovereign AI and quantum networks are fully integrated into each sovereign state’s public administration.
- Many parts of this “puzzle” are hypothetical. Its real application would require a highly sophisticated legal, technological, and organizational environment.
1. General Structure of the “Quantum Sovereign Platform”
1.1 Main Components
- Quantum Identity Module (Q-ID):
Generates and manages digital credentials via a quantum process (e.g., keys generated through QKD or quantum random number generators). The idea is that each citizen—human, cyborg, or avatar—will have an infallible identity certificate, endorsed by “Sovereign AI.” - Governance Blockchain (GovChain):
A network of smart contracts that manage the “Cyber-Sovereign Constitution,” citizens’ rights, and various processes for voting, law registration, budgeting, etc. Features a consensus mechanism compatible with quantum cryptography (resistant to quantum-computer attacks). - Central Governance AI (Sovereign AI):
Orchestrates communications between the quantum module, the GovChain, and administrative interfaces (ministries, judiciary, state and municipal agencies, etc.). It employs large language models and social optimization algorithms, always monitored by a human council and an algorithmic oversight body. - Communication and Distributed Storage Layer:
A system of distributed nodes with sovereign data centers, guaranteeing immutability and data availability. Quantum channels are used where feasible to secure critical communications.
2. Code Example: Generating Quantum Credentials + Recording on the Blockchain
Below is a primary integrated example, split into two parts:
- Quantum Module (Python + Qiskit) for generating a unique quantum identifier and its signature.
- Blockchain Part (Solidity) for registering and validating those credentials on a smart contract.
2.1 “Quantum Identity Module” (Qiskit / Python code fragment)
This script assumes access to quantum infrastructure (real or simulated) to obtain quantum random numbers. The result will be quantum_id, which serves as the basis of the digital credential.
pythonCopiarEditar# File: quantum_identity.py
# ===============================
# PART I: GENERATION OF THE QUANTUM IDENTIFIER
# ===============================
# Basic Python libraries
import hashlib
import uuid
import time
# Quantum computing library (Qiskit)
from qiskit import QuantumCircuit, Aer, execute
def generar_identidad_cuantica(n_shots=1024):
"""
Generates a quantum identifier (quantum_id) based on
bits produced by a simple quantum circuit.
:param n_shots: Number of measurements
:return: A string with a hash representing the quantum identity
"""
# Create a circuit with 1 qubit
qc = QuantumCircuit(1, 1)
# Apply a Hadamard for superposition |0> + |1>
qc.h(0)
# Measurement
qc.measure(0, 0)
# Use a local simulator; in the future, real quantum computers
# or true quantum random generators could be employed.
simulator = Aer.get_backend('aer_simulator')
job = execute(qc, simulator, shots=n_shots)
result = job.result()
counts = result.get_counts()
# 'counts' is a dictionary, e.g., {'0': 512, '1': 512}
# Extract bits in proportion to their frequency
bits_string = ""
for outcome, freq in counts.items():
bits_string += outcome * freq
# Generate a hash (SHA-256, for example) from the bits
quantum_hash = hashlib.sha256(bits_string.encode()).hexdigest()
# Optionally add extra entropy (timestamp, local UUID, etc.)
unique_entropy = str(uuid.uuid4()) + str(time.time())
combined_source = quantum_hash + unique_entropy
# Create the final quantum identity
quantum_id = hashlib.sha256(combined_source.encode()).hexdigest()
return quantum_id
# ===============================
# PART II: SIGNING (SIMPLIFIED) AND EXPORT
# ===============================
def firmar_identidad(quantum_id, clave_privada):
"""
Emulates digital signing of the quantum identity using a private key.
:param quantum_id: The generated quantum identifier
:param clave_privada: The cyber-citizen's private key (in real life, ECC or Post-Quantum)
:return: signature (string)
"""
# In a robust system, a post-quantum signature algorithm
# (e.g., CRYSTALS-Dilithium or Falcon) would be used here.
# For simplicity, we do an HMAC/HASH with the private key.
data_to_sign = quantum_id + clave_privada
signature = hashlib.sha256(data_to_sign.encode()).hexdigest()
return signature
if __name__ == "__main__":
# Usage example
qid = generar_identidad_cuantica()
print("[*] Quantum Identity generated:", qid)
# Simulated private key
fake_private_key = "FAKE_CYBERCITIZEN_PRIVATE_KEY_123"
firma = firmar_identidad(qid, fake_private_key)
print("[*] Identity signature:", firma)
# Here, we could call the Blockchain part (via web3.py)
# to record the identity and signature on GovChain.
Comments:
- In a real scenario, post-quantum signature algorithms (Dilithium, Falcon, SPHINCS+, etc.) would be implemented for added protection against quantum-computer attacks.
- The
quantum_idcould be used as an anchor of identity in the GovChain, whether directly or through Verifiable Credentials.
2.2 “Quantum Identity Registry” Smart Contract (Solidity)
This contract would be deployed on the sovereign blockchain (GovChain). It allows:
- Registering new quantum identities.
- Storing the associated signature.
- Validating the correspondence between the signature and the identity.
solidityCopiarEditar// File: QuantumIdentityRegistry.sol
// SPDX-License-Identifier: MIT
pragma solidity ^0.8.18;
/**
* @title QuantumIdentityRegistry
* @dev Contract to register and validate quantum identities on the GovChain.
*/
contract QuantumIdentityRegistry {
// Structure representing a cyber-citizen (human, cyborg, or avatar)
struct CiberCiudadano {
string quantumId; // The unique quantum hash
string firma; // Post-quantum digital signature (simulated here)
address wallet; // Citizen's main address on GovChain
bool registrado; // To verify existence
}
// Mapping (quantumId => CiberCiudadano)
mapping(string => CiberCiudadano) private ciudadanos;
// Event to notify the registration of a new identity
event NuevaIdentidadRegistrada(string indexed quantumId, address indexed wallet);
// Event to notify signature updates
event FirmaActualizada(string indexed quantumId, string nuevaFirma);
/**
* @notice Registers a quantum identity on GovChain.
* @dev Assumes that `quantumId` and `firma` come from a genuine quantum and signature process.
* @param _quantumId The quantum hash (generated off-chain with Qiskit or similar)
* @param _firma Signature derived from the post-quantum private key
*/
function registrarIdentidad(string memory _quantumId, string memory _firma) public {
require(bytes(_quantumId).length > 0, "Empty Quantum ID");
require(bytes(_firma).length > 0, "Empty signature");
require(!ciudadanos[_quantumId].registrado, "Quantum ID already registered");
CiberCiudadano memory nuevo = CiberCiudadano({
quantumId: _quantumId,
firma: _firma,
wallet: msg.sender,
registrado: true
});
ciudadanos[_quantumId] = nuevo;
emit NuevaIdentidadRegistrada(_quantumId, msg.sender);
}
/**
* @notice Updates the signature of a Cyber-Citizen.
* @dev Useful if keys are rotated or the signature algorithm changes.
* @param _quantumId The citizen's quantum ID
* @param _nuevaFirma New digital signature
*/
function actualizarFirma(string memory _quantumId, string memory _nuevaFirma) public {
require(ciudadanos[_quantumId].registrado, "Identity does not exist");
require(ciudadanos[_quantumId].wallet == msg.sender, "Not authorized to change signature");
require(bytes(_nuevaFirma).length > 0, "Empty new signature");
ciudadanos[_quantumId].firma = _nuevaFirma;
emit FirmaActualizada(_quantumId, _nuevaFirma);
}
/**
* @notice Verifies if the signature matches the stored quantum ID.
* @param _quantumId The quantum ID to verify
* @param _firma The signature to verify
* @return bool true if it matches, false otherwise
*/
function validarFirma(string memory _quantumId, string memory _firma) public view returns (bool) {
require(ciudadanos[_quantumId].registrado, "Identity does not exist");
return keccak256(abi.encodePacked(ciudadanos[_quantumId].firma)) == keccak256(abi.encodePacked(_firma));
}
/**
* @notice Retrieves a registered citizen’s information.
* @param _quantumId The quantum ID
*/
function getCiudadano(string memory _quantumId)
public
view
returns (string memory, string memory, address, bool)
{
CiberCiudadano memory c = ciudadanos[_quantumId];
return (c.quantumId, c.firma, c.wallet, c.registrado);
}
}
Simplified Usage Flow:
- The cyber-citizen (or avatar) runs the Python (Qiskit) script to generate their
quantum_idand signature. - Via a DApp or using web3.py/ethers.js, they call
registrarIdentidad(quantum_id, firma). - The contract stores the information on GovChain.
- Any entity can verify the signature with
validarFirma(quantum_id, firma)to check if it was tampered with.
2.3 EXAMPLE OF PYTHON CODE USING GENERATIVE AI FOR “QUANTUM CYBER-STATE” FUNCTIONS
The following prototype demonstrates a microservice (with Flask) that:
- Exposes an endpoint to generate legal text (draft laws or executive decrees) based on a generative model (e.g., GPT-like).
- Validates whether the user (human, cyborg, avatar) has (simple) credentials to use the service.
- Exposes an endpoint to generate synthetic data for simulation purposes (for example, transactions of the “Sovereign” crypto).
Note: To effectively use a generative model in Python, you would typically call an API (e.g., OpenAI, Hugging Face, or a local model). Here, we assume a hypothetical function called fake_generate_text that symbolizes a call to a language model. Likewise, generate_synthetic_data simulates creating tabular data.
Structure:
- requirements.txt: would include dependencies such as Flask, requests, etc.
- cyber_state.py: our main code.
- The
/generate_lawendpoint sends a prompt to the generative model to obtain a draft law. - The
/synthesize_dataendpoint produces a CSV with synthetic data for AI testing.
- The
Below is the file cyber_state.py:
pythonCopiarEditar#!/usr/bin/env python3
# -*- coding: utf-8 -*-
"""
Simulation of a Flask Microservice for the Quantum Cyber-State
With (symbolic) Generative AI Integration
"""
from flask import Flask, request, jsonify, make_response
import random
import string
import datetime
import csv
import io
app = Flask(__name__)
###########################################################################
# 1. Auxiliary Functions: Simulated "Generative AI"
###########################################################################
def fake_generate_text(prompt: str) -> str:
"""
Simulated function representing the response of a generative model
(GPT-like). In a real environment, here you would make an API call
to a generative model or use a local library (e.g., transformers).
"""
# Mock-up: we concatenate the prompt with some "improvised" text.
# In practice, you would call OpenAI, Hugging Face, or another provider.
simulated_response = (
f"Proposed Draft (Based on Sovereign AI):\n"
f"Regarding the matter: {prompt}\n"
f"Article 1. Established ... \n"
f"Article 2. Declared ... \n"
f"Article 3. Valid in the Metaverse and under Cyber-Jurisdiction.\n"
f"--- End of Automatic Draft ---"
)
return simulated_response
def generate_synthetic_data(num_rows: int = 10):
"""
Generates fictitious tabular data to simulate transactions or records.
In production, you could integrate a GAN library (CTGAN, SDV) instead.
"""
data_rows = []
for _ in range(num_rows):
# Example: suppose a table with:
# Transaction ID, Type (BUY/SELL), Amount, Date, Citizen ID
trans_id = ''.join(random.choices(string.ascii_uppercase + string.digits, k=8))
txn_type = random.choice(["BUY", "SELL", "TRANSFER"])
amount = round(random.uniform(10.0, 1000.0), 2)
# Simple random date simulation
date_value = datetime.date(2025, 5, 1) + datetime.timedelta(days=random.randint(0, 30))
# Cyborg/human ID
citizen_id = "QID-" + ''.join(random.choices(string.ascii_uppercase + string.digits, k=6))
data_rows.append([trans_id, txn_type, amount, str(date_value), citizen_id])
return data_rows
###########################################################################
# 2. Decorators / Endpoints
###########################################################################
@app.route("/generate_law", methods=["POST"])
def generate_law():
"""
Endpoint that receives a prompt describing the law's subject.
Performs a basic credential check and returns a generated legal draft.
"""
# Simplified credential check
api_key = request.headers.get("API-KEY", "")
# In a real scenario, this would be verified in the GovChain or a database
if api_key not in ["HUMAN123", "CYBORG456", "AVATAR789"]:
return jsonify({"error": "Invalid or missing credentials"}), 403
# Retrieve the prompt
data = request.get_json()
if not data or "topic" not in data:
return jsonify({"error": "Missing 'topic' in JSON"}), 400
law_topic = data["topic"]
# Simulated call to the generative AI
generated_text = fake_generate_text(law_topic)
return jsonify({
"status": "OK",
"received_prompt": law_topic,
"generated_draft": generated_text
})
@app.route("/synthesize_data", methods=["GET"])
def synthesize_data():
"""
GET endpoint that generates synthetic transaction data.
Returns a CSV in the response.
"""
try:
num_rows = int(request.args.get("rows", 10))
except ValueError:
num_rows = 10
# Generate rows
rows = generate_synthetic_data(num_rows)
# Build a CSV in memory
output = io.StringIO()
writer = csv.writer(output, delimiter=";")
writer.writerow(["ID", "TYPE", "AMOUNT", "DATE", "CITIZEN_ID"])
for row in rows:
writer.writerow(row)
csv_data = output.getvalue()
output.close()
# Return as a CSV file
response = make_response(csv_data, 200)
response.headers["Content-Disposition"] = f"attachment; filename=synthetic_data_{num_rows}.csv"
response.headers["Content-Type"] = "text/csv; charset=utf-8"
return response
###########################################################################
# 3. MAIN: run the app
###########################################################################
if __name__ == "__main__":
app.run(debug=True, port=5000)
General Code Explanation:
fake_generate_text(prompt)
Emulates calling a generative model. In reality, an API or local library (e.g., Hugging Face transformers) would be used to generate text from the prompt.generate_synthetic_data(num_rows)
Creates tabular (e.g., fictitious transaction) data. In a real scenario, this would be replaced by a generative AI model (e.g., CTGAN or SDV) to produce synthetic data faithful to the original distributions of the State’s economy.- Endpoint
/generate_law
Receives a topic (e.g., “Regulation of Cyborg Implants”), checks basic credentials (API-KEY) to simulate the user being a “HUMAN,” “CYBORG,” or “AVATAR.”
Generates a legal draft that could be reviewed by the Algorithmic Chamber or the Human Chamber within the Quantum Cyber-Sovereign State’s infrastructure. - Endpoint
/synthesize_data
Returns a CSV file with synthetic rows (a simulation of transactions involving the sovereign crypto, for instance). This could serve as a basis for feeding AI models, validations in the GovChain, etc.
Potential Improvements and Integrations:
- Security: Integration with a blockchain verification system (GovChain), using a token or quantum credentials (Q-ID).
- Explainability: Add a route to display feature importances or interpretations of generated models.
- Quantum Layer: Use post-quantum libraries for encryption and for signing the response.
- Orchestration: Deploy in containers (Docker, Kubernetes) and use a load balancer to handle high request volumes (scalable network).
- Auditing: Log each call in the GovChain so that simulations, law drafts, and generated data can be traced for subsequent inspection by the Algorithmic Control Body (OCA).
Final Reflection
This example offers a primary illustration of how generative AI (even in a basic form) can be integrated into the logic of a “cyber-state” with hybrid infrastructure. In a real scenario, you would need to:
- Invoke a robust generative model (either open source or a private API) to draft laws, technical reports, and simulations.
- Extend the security/identity layer (e.g., using Q-IDs and post-quantum digital signatures).
- Incorporate modules for the “Algorithmic Chamber,” the “Robot Courts,” and the Algorithmic Ministries—all supervised by citizens and human judges, in accordance with the Quantum Cyber-Sovereign Constitution.
Thus, the path is set toward an algorithmic and transparent governance that combines the strength of AI with respect for human dignity and the technological sovereignty of the new State.
3. Integration with “Sovereign AI” and Governance.
The smart contract layer and quantum identity are merely the foundational blocks for building the entire Digital State. On this foundation, more complex modules would be added:
- Intelligent Legislation (Algorithmic Chamber):
Smart contracts (or DAOs) that receive legislative proposals (on-chain) and use the Sovereign AI off-chain for massive data analysis, impact simulations, etc. The result (a bill drafted by AI) is submitted to the “Human Chamber” + Digital Referendum. - Algorithmic Justice (Robot Courts):
Smart contracts record cases and evidence (stored in IPFS or another distributed system) and “request” the Sovereign AI to draft a ruling. Human judges (in collaboration with “robot-judges” in a collegial justice system) validate or reject the preliminary ruling, with all processes documented on the blockchain. - Hybrid Executive Power:
Algorithmic Ministries with an administrative interface that consults AI predictive models to execute action plans (subsidies, investments, logistics, etc.), recorded on the GovChain. Quantum Transparency: each public policy or government procurement is signed with quantum credentials, facilitating automated audits. - Quantum Voting:
A post-quantum e-voting system, where each citizen uses theirquantum_idto cast a ballot, mitigating risks of cryptographic breaches by advanced quantum computers.
4. Futuristic and Ethical Considerations.
- Data Protection and Privacy:
With quantum identities and immutable blockchain records, it is crucial to design selective anonymity systems and homomorphic cryptography so that sensitive data remains protected, upholding privacy as a constitutional cyber-guarantee. - Regulation of Sovereign AI:
While AI is the “backbone” of this Cyber-State, there must be human oversight and citizen audits to prevent “algorithmic authoritarianism.” - Inclusion of Avatars and Cyborgs:
Thequantum_idcould expand to multiple “identity instances” (for example, one human controlling several avatars), always with the possibility of tracing them in cases of conflict or fraud. - Scalability and Post-Quantum Feasibility:
It must be assumed that “classical” cryptographic algorithms (RSA, ECC) may become obsolete with the advent of large-scale quantum computers. Hence the relevance of post-quantum algorithms.
5. Next Steps: “Launch” of the Quantum Cyber-Sovereign State.
- Prototype Network Development
Build a testnet (GovChain) with a consensus mechanism resistant to quantum attacks (e.g., XMSS or SPHINCS). Integrate quantum oracles to obtain true entropy and process external events (macro-data, land registry, Metaverse, etc.). - Governance Interface
Create a Citizen Portal for:- Online voting (with quantum validation)
- Filing complaints and lawsuits
- Accessing AI recommendations from “AI Ministers”
- Algorithmic Regulatory Body
Define an independent entity (OCA: Algorithmic Control Body) authorized to audit AI models and smart contracts, ensuring algorithmic fairness and respect for cyber-human rights. - Cultural and Democratic Expansion
Implement policies that guarantee real citizen engagement (human, cyborg, and virtual), continuous training in digital competencies, and equitable hardware/connectivity access—free from economic, geographic, or any other discrimination.
6. Conclusion.
The proposed “Quantum Cyber-Sovereign State” is much more than a set of legal or technological tools; it represents a paradigm shift in how sovereignty, citizenship, and the exercise of power are conceived. The genuine convergence of:
- Quantum digital identities
- Smart contracts on a POST-QUANTUM GOVCHAIN
- Sovereign AI as a collective brain
- Cybersecurity and transparency anchored in quantum cryptography
demonstrates a coherent flow from generating a quantum ID (in Python) to recording it on-chain (in Solidity). For a more comprehensive “Quantum Cyber-Sovereign State,” numerous additional components and scalable modules (voting, robot courts, Sovereign AI, etc.) would be needed.
All this points to a truly transhuman and post-human governance, yet deeply rooted in principles of equity, dignity, and shared prosperity. The key lies in maintaining balance: technology must serve society, not the other way around. The code sketch presented is merely a skeleton—a seed—that sparks the imagination of how these mechanisms could be implemented in a real or prototype environment.
“The future is the co-evolution of humanity and AI, with freedom as its pillar and dignity as its banner.”
— Manifesto of the Quantum Cyber-Sovereign State
7. TABLE 1. QUANTUM NETWORK ARCHITECTURE FOR A CYBER-SOVEREIGN STATE: COMPONENTS, TECHNOLOGIES, AND CHALLENGES
Introduction:
The following table compiles the essential subsystems of a quantum communications infrastructure designed for a Cyber-Sovereign State. It describes key components, associated technologies, operational functionalities, and the challenges each subsystem faces. Its objective is to serve as a reference guide for designing, implementing, and auditing a national quantum network, which underpins the pillars of security, digital governance, transparency, and technological sovereignty in a future Cyber-Quantum State.
| COMPONENT / SUBSYSTEM | DESCRIPTION / ROLE | MAIN TECHNOLOGIES | KEY FUNCTIONALITIES | EXAMPLES / PROVIDERS (REFERENCE) | CHALLENGES / OBSERVATIONS |
|---|---|---|---|---|---|
| 1. Quantum Access Nodes (Q-Nodes) | Entry points for institutional users (ministries, courts, armed forces), critical enterprises, or government facilities. They manage quantum and classical connections. | – QKD (Quantum Key Distribution) equipment – Entangled photon generators – Post-quantum encryption systems | – Quantum authentication (identity validation). – Quantum key generation for real-time encryption. – Dual (quantum + classical) connection with priority for sensitive traffic. | – ID Quantique (QKD) – Toshiba (QKD) – Quantum Xchange (QKD infrastructure) | – High initial installation and maintenance costs. – Requirement for highly specialized personnel. – Sensitivity to signal loss and distance; each segment may need costly hardware to preserve quantum coherence. |
| 2. Distributed Quantum Repeaters | Extend the range of the quantum signal (photons/entangled states) beyond the limits of conventional fiber optics, preserving quantum coherence. | – Quantum memories – Quantum error correction protocols – Integrated photonic devices | – “Re-entangle” or “re-generate” qubits to cover hundreds of kilometers. – Minimize quantum losses and errors. – Operate in sync with the classical channel to exchange control and verification data. | – IBM, Google, Xanadu, IonQ (development of repeaters and photonics) | – Technology still under research for large-scale repeaters. – Expensive implementation and complex infrastructure (cooling, vibration isolation, etc.). – Extremely high temperature and stability requirements to maintain quantum coherence. |
| 3. Terrestrial Quantum Backbone | A fiber-optic network with repeater stations set at intervals (approximately 80–100 km). Interconnects government headquarters, data centers, and critical nodes on a national scale. | – Low-attenuation (single-mode) fiber – QKD devices on each segment – Quantum routing protocols | – Long-distance distribution of encrypted keys. – “Always-encrypted” channel for classified data and state services. – Convergence with classical networks and intrusion/interception checks. | – China (Beijing–Shanghai quantum network) – Fiber operators (e.g., Toshiba, Furukawa) | – Difficulties over large distances: quantum signals degrade rapidly if not combined with adequate quantum repeaters. – High deployment costs (installation and maintenance). – Requires a “Master Plan” for national coverage with a redundancy mesh to ensure resilience against outages. |
| 4. Satellite Quantum Segment | Uses quantum satellites to link very distant regions (islands, mountainous areas) and ensures the exchange of quantum keys between ground stations. | – QKD satellites (entangled photons) – Ground stations with quantum telescopes – BB84, E91, etc. protocols | – National or international quantum coverage (satellite-based QKD). – Backup in case of fiber outages (natural disasters, contingencies). – Secure connection with other nations or regional blocs. | – Micius Satellite (China) – Prototypes in the EU, Canada, USA | – Requires satellite launch and maintenance (very high cost), coordination with space agencies. – Precision in optical alignment and minimizing losses from atmospheric turbulence. – International regulation and frequency-spectrum usage agreements. |
| 5. 6G/7G and NTN (Non-Terrestrial) Channels | Ultra-high-speed (THz), low-latency mobile networks integrated with non-terrestrial infrastructures (satellites, drones). They supplement the classical channel to synchronize QKD and transmit data at high speed. | – 6G/7G infrastructure – THz band protocols – NTN antennas (satellites, stratospheric balloons, UAVs) | – Provides a high-speed “classical channel” for distributing data encrypted with quantum keys. – Multiple mobile or fixed nodes with dynamic spectrum management. – Potential connectivity in remote areas using hybrid layers (terrestrial + satellite). | – Huawei, Samsung, Ericsson, Nokia (6G prototypes) | – Standardization still in progress (maturity expected post-2030). – Integrating QKD into network hardware requires specific design improvements (chips, protocols). – High deployment costs, spectrum availability, and the need for international regulation. |
| 6. Storage/Processing Infrastructure | Sovereign data centers (future “Quantum Data Centers”) running advanced AI, hosting smart contracts (GovChain), and managing quantum identities. | – Post-quantum servers – Small-to-medium quantum computers – HPC (High Performance Computing) technologies | – Big Data, AI, and simulation processing. – Long-term storage of encrypted data (protection against future attacks). – Sustaining the “Sovereign AI” and critical e-government services (robotic courts, algorithmic chambers, etc.). | – IBM Quantum, Google Quantum AI, Azure Quantum | – High energy consumption and extreme cooling requirements (cryogenics for superconducting qubits, for instance). – Migrating classical systems to post-quantum environments may present compatibility risks. – Dependence on cutting-edge tech providers: recommended state-level agreements or strategic alliances to ensure sovereignty. |
| 7. Sovereign AI Module | The “central brain” of network management. Monitors quantum routes, detects intrusions, manages bandwidth allocation, and plans contingencies. | – Large Language Models – Graph optimization algorithms for networks – Anomaly detection modules (Machine Learning) | – Real-time path adjustments for data (repeaters, satellites, 6G). – Automated integrity and latency audits. – Alerts against espionage attempts or fiber outages. – Potential role in the “Algorithmic Chamber” for legislative proposals, generating impact simulations. | – Custom AI (TensorFlow, PyTorch, etc.) – HPC for training and deployment | – Prevent “algorithmic authoritarianism”: requires human oversight and external audits. – Risk of AI bias if it processes cybersecurity and citizen access data (discrimination, errors). – Could centralize too much power without checks and balances (e.g., an Algorithmic Oversight Body). |
| 8. Blockchain Integration (GovChain) | Quantum-resistant blockchain that logs identities, transactions, smart contracts, and the traceability of state communications (without exposing content, only metadata). | – Smart contracts (Solidity, Hyperledger) adapted to post-quantum cryptography – PBFT or similar quantum-resistant protocols | – Immutable log of QKD sessions, Quantum ID generation, judicial rulings, and electronic voting. – Transparency and citizen auditing. | – Ethereum (future post-quantum versions), Hyperledger, Algorand (PQC research) | – Scaling challenge and ensuring resistance to quantum computers (which could break classical keys). – Adapting nodes and validators to algorithms like Falcon, Dilithium, SPHINCS+. – Computational cost of post-quantum signatures in networks with large transaction volumes. |
| 9. Quantum Identity Module (Q-ID) | Manages the generation of digital identities based on quantum keys or quantum randomness, preventing duplication and impersonation. | – Qiskit (qubit generation) – Post-quantum signature algorithms (Dilithium, Falcon) – Quantum-resistant hashing (SHA-3, etc.) | – Providing unique credentials to humans, cyborgs, and avatars. – Validating the legitimacy of actions (voting, contracts, government procedures). – Integrates biometric and quantum identity for enhanced reliability. | – IBM Qiskit, Microsoft Quantum Development Kit, NIST post-quantum libraries | – Requires resilience against potential quantum attacks. – Integration with GovChain and biometric systems may raise privacy concerns. – Ensuring multiplatform compatibility (citizens with various devices, state servers, etc.). |
| 10. Auditing & Oversight (Algorithmic Oversight Body) | An independent entity that reviews transparency and ethics in AI systems and quantum infrastructure (preventing abuses, discrimination, excessive surveillance). | – Explainable AI tools – Real-time monitoring platforms (dashboards) – “On-chain” audit protocols | – Auditing Sovereign AI decisions. – Monitoring QKD logs and secure connections. – Citizen channel to report abuses or security flaws. – Reviewing hardware/satellite reliability. | – In-house solutions + Big Data software (Splunk, Elastic, etc.) with explainability modules | – Risk of merely formal auditing if independence is not guaranteed. – Requires experts in AI, quantum physics, and digital law. – Possibility of political manipulation without constitutional checks and balances. |
| 11. Multilayer Security (Suggested Improvement) | Adds protective layers combining quantum and classical techniques to strengthen end-to-end security. | – Hybrid cryptography (quantum + post-quantum) – Quantum firewall – Quantum Intrusion Detection Systems (Q-IDS) | – Dual verification for authenticity and encryption. – Preventing man-in-the-middle attacks, even if the quantum layer fails. – Continuous monitoring of links for quantum or classical anomalies. | – Hybrid integrations developed by leading cybersecurity labs (e.g., MIT, Stanford, ETH Zurich) | – Complex and costly implementation; requires personnel capable of maintaining quantum and classical systems in parallel. – Must address interoperability issues between different cryptographic layers. |
Observations:
- Cost and Scalability: Deploying each component demands significant investment and continuous updates, especially for quantum repeaters and QKD nodes.
- Training and Expertise: A critical mass of engineers specialized in quantum computing, cryptography, AI, and digital law is needed for maintenance and regulation.
- Legal and Ethical Framework: Legislating data sovereignty, AI oversight, cyborg citizenship, and privacy protection is essential, aligned with the Cyber-Sovereign Constitution.
- Progressive Integration: It is advisable to start with priority links (Ministry of Defense, Justice, Government Palace) and gradually extend to regional offices and less critical users.
- Post-Quantum Security: In addition to QKD, post-quantum algorithms for encryption and signatures should be employed when a quantum channel is not feasible.
- Citizen Oversight: Transparency and public participation are vital to prevent “algorithmic authoritarianism” and ensure legitimacy of the new quantum governance system.
In combination, these components form a fully functional quantum network that empowers a Cyber-Sovereign State to accelerate and secure its communications, aligning with a future where Sovereign AI, blockchain-based governance (GovChain), and hybrid citizenship (humans, cyborgs, and avatars) coexist in a highly secure, auditable technological environment.
9. APPENDIX 2.
TABLE OF CURRENT CRITICISMS AND CHALLENGES FOR IMPLEMENTING THE “QUANTUM CYBER-SOVEREIGN STATE”
| Area / Aspect | Weaknesses | Explanation |
|---|---|---|
| 1. Technological Scalability | – Lack of quantum infrastructure on a large scale. – High implementation and maintenance costs. | – Quantum computing is still in its research phase, and there is not yet sufficient industrial capacity for massive deployment. – Building and maintaining quantum data centers and robust networks may cost billions, hindering immediate adoption. Potential future advances (e.g., Microsoft’s “quantum chip”) might drive quantum computing toward more accessible costs (Microsoft Quantum or Azure Quantum). |
| 2. Legal and Constitutional Complexity | – Risks of incompatibility with international legal frameworks. – Possible conflict with civil rights. | – Concepts like avatar citizenship and a mixed human-robot judiciary have no direct legal precedent, potentially clashing with existing jurisprudence and the sovereignty of other States. – Could conflict with current human rights treaties or international regulations. |
| 3. AI Decision-Making Authority | – Excessive delegation to algorithms without complete human supervision. – Risk of “algorithmic authoritarianism.” | – Although audits and citizen participation are proposed, reliance on AI can create opacity: government decisions may depend on highly complex algorithms that neither the population nor certain experts fully understand. Concerns exist about granting a “technological Leviathan” so much power. |
| 4. Privacy and Surveillance | – Excessive surveillance if AI or the “Cyber National Guard” control personal data. – Risk of biometric or neurological identification abuse, even potential brain hacking. | – Universal connectivity and registration of all identities (human, cyborg, avatar) with facial or neural recognition could lead to a “hyper-surveilled” State. – The promised transparency does not guarantee the absence of abuse, as data control might be overly concentrated in an algorithmic oligopoly. |
| 5. Algorithmic Discrimination | – Potential bias in data collection and processing, even with audits. – Technological inequality. | – AI algorithms may perpetuate or exacerbate existing social biases, affecting legislative or judicial automated decisions. – Those unable to afford neural or other implants—or who have limited digital literacy—could become marginalized, creating gaps within “cyber-sovereign” citizenship. |
| 6. Quantum and Post-Quantum Security | – Risk of adversarial quantum attacks. – Emerging vulnerabilities as quantum technology evolves. | – The transition to post-quantum cryptography has not been fully tested for global use. – Rapidly advancing quantum technologies may surpass current defenses and expose critical data, jeopardizing the sovereign infrastructure. |
| 7. Migration Complexity and Costs | – Difficulty transitioning systems and legal frameworks to the new ecosystem. – Resistance from public and private sectors. | – Adopting this model requires reforming much of the public administration and legal infrastructure. – The costs (training, development, replacing legacy systems) might be prohibitive, requiring lengthy transition periods. |
| 8. Merger of Realities (Human-Avatar-Cyborg) | – Ethical challenges in granting equal rights to avatars and cyborgs. – Ambiguities in the legal responsibility of “virtual entities.” | – No solid regulations exist for criminal or civil responsibility of autonomous avatars, especially if operated by AI. The legal system must evolve to define parameters of responsibility. – Multiple digital identities (human, cyborg, avatars) cause uncertainty when applying the law and assigning individual responsibilities. It is conceivable that, in the future, a single being might possess various forms of existence. |
| 9. Concentration of Technological Power | – Danger of monopolizing Sovereign AI and data centers by the State or a consortium. – Actual centralization despite claims of decentralization. | – Quantum and AI infrastructure requires enormous investments, feasible only for powerful governments or large tech corporations. – Risk of creating private oligopolies or concentrating power in a few hands, unless transparent bidding systems and oversight are employed. Blockchain technology can play a major role in controlling such concentration. |
| 10. Political and Cultural Feasibility | – Citizen reluctance toward an “overly technological” model. – Misalignment with traditional worldviews. | – Some societies may reject delegating public functions to robotized courts or algorithmic legislatures. – Cultural and educational gaps hinder mass adoption and can generate political opposition, delaying or blocking implementation. |
| 11. Lack of International Standards | – Limited interoperability with traditional States. – Problems with international recognition and legitimacy. | – Any State adopting this model must integrate it with global regulations for trade, extradition, human rights, etc. – Uncertainty over how other nations would recognize the legal validity of avatars, cyborgs, or AI decisions if no shared framework is in place, highlighting the importance of international treaties and agreements. |
| 12. Speed of Innovation vs. Legislation | – Legislation often lags behind innovation. – Risk of rapid obsolescence of legal standards. | – Technology evolves faster—indeed, changes every second—than legislative bodies can act. – Legal provisions on AI or quantum computing might become obsolete in a short time, requiring constant constitutional and legislative reform. |
General Observation
These points do not invalidate the proposed model but serve as cautionary notes, emphasizing the need for meticulous planning, continuous legal updates, and robust control and citizen participation mechanisms that accompany technological evolution.
Challenges to Overcome
- Develop and expand quantum infrastructure sustainably and progressively.
- Align legal and institutional frameworks with international standards.
- Design protocols for transparency and AI oversight in decisions of the new cyber-government.
- Protect privacy and fundamental rights amidst increasing surveillance.
- Prevent algorithmic discrimination via audits and digital inclusion policies.
- Strengthen quantum cybersecurity with a national and international security perspective.
- Plan the migration from legacy systems with a cost-effectiveness strategy and transitional phases.
- Adapt regulations to new and imminent hybrid realities (humans, cyborgs, avatars).
- Avoid technological monopolization through proper regulation and competition.
- Encourage cultural and political acceptance through education and citizen engagement.
- Promote international cooperation to establish standards and mutual recognition.
- Maintain a flexible, evolving legal framework that responds to rapid technological advances.
10.APPENDIX “3”:
TABLE OF INTEGRATION OF DEVELOPMENT PRINCIPLES (PYTHON/FLASK) AND REGRESSION MODELING IN THE QUANTUM CYBER-SOVEREIGN STATE
It is proposed to integrate Flask microservices with quantum infrastructure (nodes, quantum repeaters) and the blockchain technology (GovChain) described in previous sections, so that the Sovereign AI and ML models (for instance, linear, polynomial, or logistic regressions) can be fully incorporated into the ecosystem of the Quantum Cyber-Sovereign State. This synergy would enable the flexible and scalable deployment of web services—using Flask as the access layer—while taking advantage of post-quantum cryptography’s robustness and GovChain’s immutability to ensure transparency, auditability, and data sovereignty.
Below is the “Table” illustrating how the foundations of Python and Flask, together with various regression techniques, fit into the futuristic and automated governance vision described in the institutional architecture, automated economy, citizen security, and other constituent elements of this Cyber-Sovereign State.
| ASPECT / IDEA | DESCRIPTION / RELEVANCE | APPLICATION WITHIN THE “QUANTUM CYBER-SOVEREIGN STATE” |
|---|---|---|
| 1. Python + Flask: General Overview | – Python is a widely used language with a rich ecosystem of AI libraries. Flask makes it possible to create lightweight web services (APIs) that are easy to scale and integrate with algorithms. Its simplicity facilitates rapid prototyping of cyber modules and AI systems. | – In the ECS, there could be a citizen portal where cybercitizens (humans, cyborgs, and avatars) interact with various systems (voting, audits, quantum identity registration). Flask would serve as an access point to expose the “Sovereign AI” functionalities to the citizenry. |
| 2. Flask Scalability and Hybrid Architectures | – Although it is called a “micro” framework, Flask can be expanded with load balancers, containers, and other strategies for large-scale projects. It supports modularization and scaling in cloud/distributed tools. | – Within the ECS, the e-government infrastructure (GovChain, Sovereign AI, civic registries, etc.) will require scalable services. Flask could be the web layer which, alongside blockchains and quantum networks, supports massive user operations (voting, online procedures). |
| 3. Integrating AI (Regressions and ML) in Services | – Python provides libraries (scikit-learn, TensorFlow, PyTorch) to develop predictive models (linear, multiple, logistic regression) and expose them as endpoints. | – The ECS relies on predictive models for legislative, executive, and judicial processes (e.g., fraud detection, impact simulations, forecasting social needs). One could build Flask APIs offering a “regression service” or “classification service” for various Algorithmic Ministries. |
| 4. Development and Deployment Workflow | – Routes (endpoints) are defined to encapsulate ML or administrative logic. Python modules (packages) + testing + CI/CD enable structured development. | – The Hybrid Executive Branch and the Algorithmic Chamber could use Flask microservices to receive data, process them with AI, and return results to human advisors or GovChain. This facilitates the creation of “Algorithmic Ministers” with specific tasks (model, endpoint, etc.). |
| 5. Linear Regression (Simple and Multiple) | – Supervised models that predict continuous variables. Useful for public policy, economic projections, and resource estimation. | – In the Automated Economy, the AI could use regressions to estimate taxes, GDP, prices, or resources, helping “Algorithmic Ministers” make decisions. A “regression endpoint” in Flask would integrate data from the Metaverse, cyber-transactions, etc., generating economic forecasts. |
| 6. Nonlinear Regression (Polynomial, Exponential) | – Useful when data follow more complex patterns (curves, exponential growth). This avoids linear underestimations and better captures complex socio-technological behaviors. | – In the ECS, exponential phenomena may arise (e.g., the adoption of cyborg technology or the evolution of “Sovereign Crypto” transactions). Polynomial models could be incorporated into the corresponding Ministries, enabling forecasts of cyborg citizenship growth or service demand. |
| 7. Logistic Regression (Binary Classification) | – Returns the probability of belonging to a class (e.g., churn/non-churn, default/non-default). Suited to predicting yes/no events with probabilistic interpretations, meaning the model also provides a value between 0 and 1 indicating the likelihood that a case (such as a customer or transaction) belongs to the “positive” class (“yes”). | – Examples in the ECS: detecting potential legal conflicts, determining the probability that an avatar might break regulations, or that a cyborg needs healthcare assistance. The “Sovereign AI” assesses risks and flows based on event probabilities (e.g., cyberattacks) and exposes them via Flask. |
| 8. Model Training (Log-loss, Gradient Descent) | – Training a classifier (logistic) or a linear regressor can be done using gradient descent or its variants (SGD). This allows processing large volumes of data to optimize parameters. | – The Algorithmic Oversight Body (OCA)—part of the central state administration—would monitor how these models are trained (to avoid bias). One could envision an internal ECS service that, via Flask, orchestrates continuous background training as new sociopolitical data are received. |
| 9. Standard Practices and Libraries (Scikit-learn, etc.) | – LinearRegression, LogisticRegression, train_test_split, mean_squared_error, etc. These enable quick prototyping with reproducible results. | – Within the ECS, these methods would be integrated into the formation of “Algorithmic Ministers.” For instance, an “Algorithmic Minister of Health” using scikit-learn to predict cyborg healthcare demands, validated in the Cyber Supreme Court if a dispute arises. |
| 10. Model Comparison and Selection | – Linear vs. Multiple vs. Polynomial vs. Logistic. The choice depends on the type of variable to predict (continuous/binary), complexity, etc. | – The ECS requires diverse prediction types: demographic projections (linear/multiple regression), binary security alerts (logistic), adoption curves (nonlinear). The “Sovereign AI” would dynamically choose the best model depending on the problem (efficiency, accuracy). |
| 11. Using Flask as a Governance “Bridge” | – Flask not only serves to expose predictions but also to manage workflows (registration, auditing, identity). It connects to databases, microservices, and blockchain for interaction traceability. | – Compatible with GovChain and the Quantum Identity Module, as Flask can be used as an API layer to register quantum identities or verify signatures. It simplifies creating citizen-participation portals (voting, virtual forums, etc.). |
| 12. Futuristic and Ethical Perspective | – Includes reflections on privacy, non-discrimination, auditing, and algorithmic ethics. Model suitability and supervision of its use must be considered. | – Directly linked to the Cyber-Sovereign Constitution, the OCA, and the guarantees of “digital rights.” Dashboards (via Flask) can be created to explain AI logic (Explainability), fostering trust and transparency in state decisions within the ECS. |
Final Observations
- The Quantum Cyber-Sovereign State draws on AI, web frameworks, and Flask to orchestrate the many processes (judicial, legislative, economic, etc.) in an agile and scalable manner.
- Regression techniques (linear, polynomial, logistic) and other ML methodologies become highly effective tools for informing automated or semi-automated decisions, while preserving human oversight.
- The Algorithmic Oversight Body (OCA) and the Sovereign AI lead the way in preventing bias, safeguarding privacy, and guiding the evolution of cyborg society—reinforcing an environment in which technology and humanity evolve together, without sacrificing human dignity or transparency of power.
11. APPENDIX 4: INTEGRATION OF MACHINE LEARNING METHODOLOGIES IN THE ARCHITECTURE OF THE QUANTUM CYBER-SOVEREIGN STATE.
Below is a structured table illustrating various Machine Learning techniques (supervised, unsupervised, metrics, validation, etc.) and how they could be applied within the legal-technological framework of a Quantum Cyber-Sovereign State. Each entry also shows how the technique reinforces or justifies the vision of a post-human state.
| IDEA OR METHOD | CONCRETE APPLICATION IN THE QUANTUM CYBER-SOVEREIGN STATE | HOW IT STRENGTHENS / JUSTIFIES THE POST-HUMAN STATE VISION |
|---|---|---|
| 1. Supervised Training (classification/regression) and the “Train-Test-Split” technique | Decision Processes in Algorithmic Ministries. Each “Algorithmic Ministry” (Health, Security, Economy) could train supervised models on historical data (e.g., predicting healthcare demands, detecting crime, forecasting economic fluctuations). Data is split into “training” and “validation” so that public policies do not overfit a single historical period. | Avoiding Overfitting in Government Policies. Ensures that “algorithmic decisions” generalize to future situations and are not biased by temporary conditions. Reinforces the idea of a dynamic State in which AIs “learn” without collapsing in the face of drastic changes (economic crises, pandemics, etc.). |
| 2. Classification Metrics (accuracy, precision, recall, F1) | Priority and Control in Judicial and Security Processes. Using F1-like metrics for “Robot Courts” to distinguish between urgent and non-urgent cases. The “Cyber National Guard” or algorithmic police could employ these metrics to minimize false positives (avoiding labeling innocent citizens as offenders) and false negatives (not ignoring real threats). | Transparency and Fairness in Algorithmic Justice. Justifies adopting statistical controls that measure the effectiveness of judicial/police AI, guaranteeing non-discrimination. Strengthens the vision of a State that protects “cyber-rights” through robust and explainable models. |
| 3. Decision Trees & Random Forests | Legislative and Judicial Application. For the “Algorithmic Chamber” (Legislative Branch), decision trees could “branch out” proposed bills based on socioeconomic impact, offering a quick overview of why one project is selected over another. “Random Forests” in “Robot Courts” could process thousands of legal cases and “vote” on decisions to reduce bias and improve accuracy. | Interpretability and Robustness. Trees make legislative and judicial decision criteria visible, aligning with the demand for “algorithmic transparency” under the Cyber-Sovereign Constitution. The post-human State vision is reinforced by demonstrating that the algorithm is not a “black box.” |
| 4. K-Nearest Neighbors (KNN) | Personalizing Services in the Metaverse. Assigning “state services” (subsidies, scholarships, medical or humanitarian aid) by comparing cybercitizen profiles (humans, cyborgs, avatars) to the most similar historical cases. Citizens who “resemble” previously identified vulnerable groups get priority assistance. | Algorithmic Inclusion. Avoids a “one-size-fits-all” approach to resource allocation. Aligns with “expanded social justice” and “human-IA coordination” that seeks equity and focuses on those most in need. |
| 5. SVM (Support Vector Machines) with maximum margin, kernels, etc. | Access Control and Identification. Used to determine who qualifies as a “Cyborg” in public health (based on medical parameters and implants). Also effective for anomaly detection (cybersecurity), delineating “normal vs. intruder” behavior in critical State networks. | Security Margin and Precision. Bolsters the notion of an ultra-secure State that filters threats with high separation margins. Underscores digital sovereignty by having a robust method to identify intruders, hackers, or anomalous data in quantum infrastructure. |
| 6. Dimensionality Reduction (PCA, t-SNE, UMAP) | Real-Time Visualization and Monitoring. The “Algorithmic Chamber” can analyze social, economic, and neurological (cyborg) variables, then map them into 2D/3D space for the “Human Chamber,” providing an understandable overview. The “Algorithmic Oversight Body” can synthesize vast information and detect clusters of corruption or anomalies. | Enabling Human-AI Co-Governance. The post-human vision involves huge data volumes (Metaverse, implants, etc.). PCA or t-SNE/UMAP allow human advisors to grasp AI findings and trust the projections. |
| 7. Ensemble Models (Bagging and Boosting) | Consensus-Based Policy Decisions. Bagging (e.g., Random Forest) helps reduce variance in predictions for public policies by combining multiple “trees,” each trained on different subsets of national data. Boosting incrementally refines key estimates (e.g., budgeting, security spending). | Robustness and Iterative Correction. Highlights a vigilant State that continually improves accuracy and lowers variance in its estimates. Aligns with “socio-technical audits” and the constant refinement of AI under civic oversight. |
| 8. Regression Metrics (MAE, MSE, RMSE, R²) | Evaluating Policies and Social Programs. The “Algorithmic Minister of Economy” might predict GDP or cyborg unemployment, comparing model error (MSE) post-implementation. R² measures how much the algorithmic variables explain real socioeconomic variation. Low R² prompts model recalibration. | Data-Based Public Accountability. Justifies using quantitative indicators and error evaluation in policymaking, fostering accountability. Helps detect over- or under-estimation by algorithms and correct biases. |
| 9. Cross-Validation (K-Fold, Stratified) | Multi-Phase Policy Design. Rather than basing decisions on a single dataset, historical data is split into K folds so the AI (hyper)optimizes public policy or security plans more reliably. Stratified validation handles imbalances (e.g., a cyborg minority vs. human majority) by ensuring each group is proportionally represented. | Balance and Generalization. Prevents skewing laws or policies by focusing on just one period or subset. Reinforces a State that seeks stability and fairness: all citizens (including avatars and cyborgs) benefit from properly calibrated models. |
| 10. Regularization (Ridge, Lasso) to avoid overfitting | Prioritizing Key Variables in Governance. When running regression on thousands of indicators (economic, health, cybersecurity), Lasso “deactivates” irrelevant variables while Ridge reduces the excessive influence of certain others. This narrows state resources to an “essential” set of predictors, avoiding “noise” in governance. | Reducing Complexity in Decision-Making. Consistent with an efficient system, it avoids inflating parameters of little importance. Supports a more targeted resource-management approach, reflecting an “algorithmic yet frugal” State that discards superfluous aspects and focuses on core needs. |
| 11. Data Leakage and Prevention (ensuring models don’t “see” future data) | Protecting the Integrity of the Sovereign AI System. Prohibits using “illicit” or realistically unavailable data (e.g., not training the national budget AI with secretly obtained info from neighboring countries). Legal and procedural methods ensure the AI is not contaminated with test or future data, thus avoiding temporal bias in predictions. | Sovereignty and Algorithmic Ethics. Preventing “data leakage” preserves the legitimacy of the Quantum State. Reinforces technological sovereignty and “chain-of-custody” practices for information so as not to undermine public policy with unfair advantages or time manipulation. |
| 12. Unsupervised Learning (Clustering, e.g., DBSCAN, HDBSCAN) | Advanced Segmentation of Citizens and Entities. DBSCAN/HDBSCAN can detect communities of cyborgs with similar implant profiles or identify crime risk patterns in major cities, all without predefined groupings. The “Algorithmic Chamber” can analyze complex data (education, Metaverse, etc.) and craft legislation tailored to each subgroup. | Revealing Non-Obvious Patterns. Reinforces a proactive State that uncovers vulnerable regions, Metaverse cultures, special cyborg needs, etc. Fosters “custom-fit legislation” for a diverse society, rather than rigid categorization. |
| 13. Clustering Evaluation Metrics (Silhouette, Davies-Bouldin, Rand Index) | Monitoring Citizen Groupings. The Algorithmic Oversight Body can evaluate AI-created clusters by checking internal cohesion and separation (preventing “unfair mixing” that leads to discrimination). External metrics (Rand Index) compare actual census data against algorithmic clustering to detect bias. | Validity in “Algorithmic Social Engineering”. The State legitimizes itself by ensuring population clusters do not produce hidden segregation. Reinforces “non-discrimination” and aligns policies with the “Human Chamber,” reflecting true social representation. |
| 14. Visualization and Explainability (charts, plots, decision trees, SHAP values, etc.) | Transparency in Algorithmic Ministries and Robot Courts. Publish explanatory visuals of each AI decision, including why a legal case was approved or denied and why a specific policy is most viable. Use methods like SHAP or LIME for the “Human Chamber” to see which variables drive the algorithm’s recommendations. | “Clear Accounting Preserves Trust”. The Cyber-Sovereign Constitution mandates “Explainability”: citizens trust AI’s outcomes more when they understand how decisions are reached. Aligns with a living, intelligent, and accessible State — not a black box — subject to citizen oversight. |
| 15. Ensemble Stacking + Voting (multiple models in a meta-model) | Collegiate Legislative Resolutions. The “Algorithmic Chamber” may combine different systems (Decision Trees, Neural Networks, Fuzzy Rules) via a “voting” process to produce a robust legislative outcome. The “Sovereign AI” (meta-level) summarizes the vote and presents a “recommended bill.” Similarly, “Robot Courts” might have multiple AI “judges,” reducing the variance of any single “robot judge.” | Algorithmic Plurality and Consensus. Justifies the analogy of “several AI judges” yielding fairer decisions. Reinforces the concept of a constantly evolving State guided by multiple criteria that maximize justice and efficiency instead of depending on a single system. |
| 16. Cross-Validation for Hyperparameter Tuning | “AI Organic Law” That Regulates and Oversees. Whenever the Executive or Judiciary branches fine-tune a system (varying hyperparameters such as tree depth, L1/L2 regularization, SVM kernels, etc.), a controlled CV process is used. The Algorithmic Oversight Body audits the final model to ensure it is not overfitted to biased data and generalizes well (e.g., to mass migrations, cyber pandemics, etc.). | Avoiding Data Leakage and Bias. Emphasizes that the State does not lock in hyperparameters that only work “here and now.” Underlines the “Sovereign AI” principle of resilience and adaptability. |
| 17. Unsupervised Feature Engineering (clustering, correlations, PCA, etc.) | Optimizing Government Indicators. By grouping related variables (cyborg birth rates, exoskeleton adoption, etc.), the State retains only the most representative. This decreases “data overload” and accelerates decision-making. | An Agile State with Less Bureaucracy. Helps simplify the management of Metaverse-scale data and a hybrid citizenry. Justifies adopting unsupervised techniques as an “internal tool” for the Sovereign AI. |
| 18. Validation of Unsupervised Models (Silhouette, elbow, Davies-Bouldin, etc.) | Checking Clustering Quality (Metaverse Censuses, for example). The ECS can confirm whether a self-reported census (humans, cyborgs, avatars) has coherent clustering. Silhouette and Davies-Bouldin scores measure the cohesion of these groups, informing the Legislative Branch about real social conditions. | Justifies Dynamic Reconceptualization. With no labeled data in many cases, the AI discovers real clusters and validates them using internal/external methods. Reinforces a State that “self-evaluates” and refines population segmentation without imposing arbitrary categories. |
| 19. Data Snooping and Temporal Separation (Time-Series Split) | Quantum Governance Respecting Sequential Events. To forecast future policies, the system must not rely on data from the “future” that it would not have had at the time of decision-making. The “Algorithmic Ministry of Finance” enforces a temporal split so that predictions use only past data, preventing “leaking” knowledge unavailable in real time. | Authenticity and Legitimacy. Adheres to integrity principles: the AI is not a “cheater clairvoyant.” Upholds the idea of a cyber-sovereign State that respects temporal linearity and does not manipulate the future using unauthorized knowledge. |
| 20. Regulation and Auditing (feature importance interpretations, etc.) | Algorithmic Oversight Body (OCA). Monitors “feature importance” so that AI does not discriminate arbitrarily (e.g., verifying which factor triggers denial of certain benefits to a cyborg). It requires that AIs publish each input’s relevance (income, implant status, etc.). | Democratic Safeguards. The “Quantum State” vision depends on checks and balances: AI does not act in secrecy. Citizens (and the Judicial Branch) can contest decisions if “feature importance” suggests bias or manipulation. |
FINAL COMMENT
This table shows how the verified and systematized fundamentals of machine learning, such as classification, regression, model validation, ensemble techniques, clustering, dimensionality reduction, etc., all fit organically into the legal-technological architecture of GOLEM.
12. APPENDIX 5: INTEGRATION OF GENERATIVE AI INTO THE “QUANTUM CYBER-SOVEREIGN STATE”—APPLICATIONS AND ENHANCEMENT OF THE FUTURISTIC VISION
Below is a functionality outline for Generative AI within the Quantum Cyber-Sovereign State. It consolidates the different tools, their main uses, their specific applications within the cyber-sovereign vision, and how they reinforce this futuristic governance project.
Generative AI Tool/Technique
Main Tasks/Uses in Generative AI
Concrete Applications in the Quantum Cyber-Sovereign State
How It Strengthens the Cyber-Sovereign Vision
- Language Generative Models (GPT, Transformers) (includes “Natural Language Generation”)
- Main Tasks/Uses:
– Drafting and summarizing texts (laws, rulings, reports).
– Conversational assistants and chatbots.
– Automated explainability of processes and content generation in multiple formats or languages. - Concrete Applications:
– Algorithmic Chamber (Legislative): Generation of legislative drafts, reports, and socioeconomic simulations.
– Robot Courts (Judicial): Initial drafting of court rulings, legal arguments for human judges.
– Citizen Services: Chatbots that guide administrative processes, explain constitutional articles, and offer 24/7 public services access to humans, cyborgs, or avatars.
– Participation and Outreach: Bots that generate summaries or translations of the Cyber-Sovereign Constitution, promoting understanding in all languages, including robotic ones. - Strengthening the Vision:
– Transparency and Agility: Speeds up legislative and judicial drafting.
– Accessibility: Enables both human and non-human citizens to better understand laws and rulings.
– Inclusion: Encourages greater participation in the Metaverse and reduces linguistic or technical barriers.
– Legitimacy and Trust: Decisions become clearer and can be automatically explained.
- Main Tasks/Uses:
- GANs / Diffusion Models (StyleGAN, DALL·E, Stable Diffusion, BigGAN) (includes “Image Generation and Manipulation”)
- Main Tasks/Uses:
– Generation of photorealistic or conceptual images, including holographic technologies.
– Creation of virtual environments, avatars, and art/design assets.
– Editing and manipulation of visual attributes. - Concrete Applications:
– Identity and Culture: Designing official symbols, avatars, and badges for cyber-citizens.
– Cultural and Tourist Promotion: Re-creation of historical environments in VR/AR and virtual exhibitions.
– Security and Privacy: Training facial recognition or biometric validation algorithms with synthetic data, without exposing real information. - Strengthening the Vision:
– Cultural Sovereignty: Reinforces local aesthetics in the Metaverse and protects digital identity.
– Privacy: Reduces reliance on real personal data by using synthetic images.
– Global Projection: Facilitates participation of hybrid citizens (humans, cyborgs, avatars) with unique virtual representations.
- Main Tasks/Uses:
- Synthetic Data Generation (SDV, CTGAN, GANs, etc.)
- Main Tasks/Uses:
– Creation of “artificial” datasets that mimic real information.
– Statistical simulations and socioeconomic scenarios.
– Balancing and protecting original data. - Concrete Applications:
– Policy Planning: Economic, demographic, and health simulations (for humans and cyborgs) without exposing personal data.
– Security Testing: The Cyber National Guard trains fraud or threat detection systems using synthetic data, protecting citizen privacy.
– Legislative Validation: The Algorithmic Chamber models social reactions before approving a law. - Strengthening the Vision:
– Data Autonomy: Generates and analyzes information without depending on third parties or compromising sensitive data.
– Privacy and Sovereignty: Prevents misuse of personal data.
– Resilience in Public Policy: Massive scenarios can be tested before real-life implementation.
- Main Tasks/Uses:
- Anomaly Detection and Correction (Autoencoders, Isolation Forest, etc.) (includes “Anomaly Detection”)
- Main Tasks/Uses:
– Identifying outliers, fraud, or abnormal behaviors in large data volumes.
– Correcting and imputing outlier or missing values. - Concrete Applications:
– Algorithmic Control Body (OCA): Real-time monitoring of “Sovereign Crypto” transactions or blockchain records (GovChain).
– Cybersecurity: Detection of intrusions or espionage in quantum infrastructure, abnormal node behavior, and administrative corruption.
– Electoral Supervision: Identification of manipulation in voting processes or anomalies in citizen registries (humans, cyborgs, avatars). - Strengthening the Vision:
– Trust in the Ecosystem: Continuous monitoring of economic and political activity.
– Data Sovereignty: The State proactively addresses threats without relying on external providers.
– Democratic Integrity: Elections and financial transactions are safeguarded against manipulation.
- Main Tasks/Uses:
- Multimodal Generation (Image + Text, CLIP, Stable Diffusion, etc.) (includes part of “Content Generation”)
- Main Tasks/Uses:
– Creation of documents and reports with automatically generated graphics and text.
– Production of virtual interfaces, presentations, and immersive experiences. - Concrete Applications:
– Government Interface: Dynamic 2D/3D panels and dashboards showing the status of projects on the GovChain, alongside simultaneous explanations.
– Virtual Assemblies in the Metaverse: On-the-fly multimodal presentations that integrate text, graphics, and analysis from the Sovereign AI.
– Official Media: Generation of bulletins, campaigns, and hybrid materials (text-image) to inform citizens. - Strengthening the Vision:
– Transparency and Accessibility: Complex data represented intuitively.
– Immersion and Usability: Greater citizen engagement through appealing information formats.
– Reinforcement of Cyber Culture: Dissemination of content blending visual and narrative elements, solidifying the Cyber-Sovereign State narrative.
- Main Tasks/Uses:
- Simulation with ML Agents (Unity, SimNet, etc.) (includes “Simulation and Data Augmentation”)
- Main Tasks/Uses:
– Training agents in virtual environments to optimize behaviors and evaluate policies.
– Creation or augmentation of simulated data to strengthen AI models (attacks, military scenarios, urban mobility, etc.). - Concrete Applications:
– Defense and Security: Simulations of drone and robot maneuvers, complying with ethical principles and laws prohibiting unjust aggression.
– Urban Planning and Transportation: Testing mobility plans for cities with both human and cyborg pedestrians.
– Cybersecurity: Validating simulated attacks and preparing defenses in high-fidelity scenarios (quantum attacks, espionage, etc.). - Strengthening the Vision:
– Risk Reduction: Trains cyber-robotic forces and public policies without endangering the population.
– Efficiency and Precision: Allows fine-tuning before physical implementation.
– Strategic Autonomy: Bolsters the State’s capacity for algorithmic anticipation and defense.
- Main Tasks/Uses:
- Text-to-SQL (Natural Language to Query Conversion)
- Main Tasks/Uses:
– Converting natural language questions into SQL statements for data extraction from public or private databases. - Concrete Applications:
– Citizen Database and Metaverse: Enables officials or citizens (human, cyborg, or avatar) to query the GovChain or state databases by asking questions like “How many cyber-citizens registered this week?”
– Open Access: No technical knowledge required to explore governmental or statistical information. - Strengthening the Vision:
– Data Democratization: Fosters transparency and citizen participation.
– Information Efficiency: Reduces search time and promotes a culture of open government.
– Digital Inclusion: Anyone can access data without needing programming or SQL expertise.
- Main Tasks/Uses:
- Educational Content Generation (GPT, Bard, etc.)
- Main Tasks/Uses:
– Creating courses, tutorials, and guides in multiple languages or formats.
– Providing personalized answers and guidance for students. - Concrete Applications:
– Cyber-Education Program: Tailored content for each citizen (human or cyborg) on Metaverse security, implant use, algorithmic ethics, etc.
– Cybersecurity Training: Interactive guides for officials and civilians, explaining data protection protocols and algorithmic governance. - Strengthening the Vision:
– Digital Literacy: Reduces educational gaps and empowers citizens.
– Continuous Updates: Content adapts in real time to new laws or technologies.
– Active Participation: Citizens become better equipped to interact effectively with the State.
- Main Tasks/Uses:
- Generative Ensemble (Stacking, Model Blending)
- Main Tasks/Uses:
– Combining different generators (text, images, music) to create hybrid experiences or make multi-criteria decisions.
– Merging outputs from multiple models for more comprehensive recommendations. - Concrete Applications:
– Hybrid State Events: Ceremonies and official acts in the Metaverse, mixing real-time AI-generated music and images. A chatbot narrates constitutional or cultural significance.
– Collective Decision-Making: The Sovereign AI integrates forecasts (security, economy, health) to issue global rulings in the Algorithmic Chamber. - Strengthening the Vision:
– Immersive Experience: Reinforces the idea of a “living,” multimedia State.
– Holistic Decisions: Combining multiple model outputs addresses complex realities with higher accuracy.
– Citizen Cohesion: Elevates ceremonies and the sense of belonging, connecting humans, cyborgs, and avatars.
- Main Tasks/Uses:
- Explainability Tools (LIME, SHAP, etc.)
- Main Tasks/Uses:
– Explaining why a model generated a certain text, image, or recommendation.
– Ensuring transparency and traceability in algorithmic logic. - Concrete Applications:
– Robot Courts (Judicial): Human judges can see how the AI “reasoned” when proposing a draft ruling or legal argument.
– Algorithmic Chamber: Visualizations (e.g., SHAP) to understand key factors driving a new law or a financial report generated by AI.
– Civic Audits: Interested citizens can inspect the logic behind policy recommendations, fostering trust in the “Sovereign AI.” - Strengthening the Vision:
– Accountability: Prevents a technological “black box” and supports public auditing.
– Social Legitimacy: Clear explanations reinforce citizens’ trust.
– Ethical and Algorithmic Governance: Minimizes biases and misunderstandings in AI decisions.
- Music and Audio Synthesis (Magenta, Jukebox, NSynth)
- Main Tasks/Uses:
– Creating synthetic musical compositions and sound effects.
– Fusing styles and genres to generate unique pieces. - Concrete Applications:
– Cyborg Culture: Setting music for state ceremonies, virtual festivities, or the inauguration of robotic/avatar entities.
– Education and Entertainment: Immersive Metaverse experiences where music is generated or adapted live for events or classes. - Strengthening the Vision:
– Artistic and Cultural Expression: The State promotes joint creativity (human + algorithm).
– Hybrid Identity: Integrates cyber culture within the “Sovereign Metaverse.”
– Innovation and Social Cohesion: Generated music fosters a sense of belonging in a diverse digital community.
- Data Augmentation (CycleGAN, Augmentor, Neural Style Transfer)
- Main Tasks/Uses:
– Enlarging and diversifying datasets (especially images) to strengthen AI systems.
– Transforming or stylizing existing data. - Concrete Applications:
– Medical Computer Vision: Expanding clinical image databases (e.g., X-rays of cyborg implants) for assisted diagnostics.
– Cultural Preservation: Generating “stylized” copies of artworks or historical heritage for educational or virtual display, without risking the original pieces.
– Robust Training: Ensuring that visual recognition or anomaly detection models confront multiple data variations, reducing biases. - Strengthening the Vision:
– Greater AI Accuracy: Training with varied data improves generalization.
– Safeguarding Cultural Assets: Digital replicas prevent potential damage to real artifacts.
– Driving Research and Development: Enables large-scale data generation for testing without compromising original sources.
- Human-Computer Interaction (Dialogflow, Rasa, RunwayML, etc.)
- Main Tasks/Uses:
– Developing chatbots, assistants, and conversational interaction tools.
– User-friendly language and vision processing for citizens. - Concrete Applications:
– 24/7 Citizen Services: Sovereign AI systems that guide administrative tasks, resolve queries, or facilitate participation in virtual consultations and legislative processes.
– Metaverse Participation: Intuitive interfaces (voice, chat, augmented reality) for online deliberations and judicial hearings.
– Inclusion and Accessibility: Support for multiple languages, disabilities, or interaction methods (human, cyborg, avatar). - Strengthening the Vision:
– Democratization of Services: Advances the goal of an open, accessible government.
– Integration of Hybrid Citizenship: Ensures communication for humans, cyborgs, and avatars alike.
– Enhanced User Experience: Reduces bureaucratic complexity and promotes digital engagement.
KEY COMMENTS
Algorithmic Sovereignty and Ethics
- The Quantum Cyber-Sovereign State is reinforced by controlling its own data infrastructure and generative models, avoiding dependency on external providers.
- Explainability tools (LIME, SHAP) and human oversight regulations (e.g., Robot Courts with human judges) guarantee transparency and accountability for algorithmic decisions.
Cybersecurity and Defense
- Anomaly detection and ML Agent simulations anticipate fraud, attacks, or hostile behavior, protecting quantum infrastructures and “Sovereign Crypto.”
- Training robotic forces and developing virtual maneuvers minimize risks and ensure continuous vigilance over digital sovereignty.
Participation and Transparency
- Content generation and explanation—texts, images, simulations—enable citizens (human, cyborg, avatar) to understand and audit algorithmic decisions.
- Chatbots, virtual assistants, and conversational APIs democratize access to state information, driving open governance.
Creativity and Culture
- Tools like GANs and audio synthesizers (Magenta, Jukebox) foster cultural production in the Metaverse, promoting artistic expressions that blend human and algorithmic contributions.
- Using synthetic data and manipulating images/art strengthens digital identity and cultural heritage without compromising real data or physical artifacts.
Adaptability and Futuristic Vision
- By simulating and modeling public policies with synthetic data, the State can swiftly respond to changing scenarios, including technological evolution and new forms of citizenship (e.g., cyborg, avatar).
- “Generative Ensemble” and “Multimodal Generation” enable an immersive governance experience, integrating multiple sources of information and formats in real time.
In summary, adopting these Generative AI tools promotes ethical, efficient, and transparent governance, safeguarding citizen data and digital rights while reinforcing sovereignty in a quantum, algorithmic environment. The convergence of humans, cyborgs, and avatars is enhanced by conversational interfaces and immersive experiences that expand citizen participation and consolidate the futuristic vision of the Quantum Cyber-Sovereign State.
oransparent form of governance. It is aligned with protecting and expanding digital rights, data sovereignty, and participation among all new forms of citizenship (human, cyborg, and avatar).
13. APPENDIX 6: QUANTUM PYTHON PROTOTYPE FOR A FUTURES MARKET ON CYBORGS, ROBOTS, AND AVATARS and Architecture
Below is a business model that integrates the TOKENIZATION OF CYBORGS, ROBOTS, AND AVATARS within an investment and hedging ecosystem using futures contracts, all framed under the vision of the Quantum Cyber-Sovereign State. On the one hand, the goal is to promote economic innovation; on the other, it seeks to enable risk management and financing opportunities in this hybrid citizenship environment (humans, cyborgs, and avatars, including robot extensions with AI systems).
13.1. Central Idea: Futures on “Tokenized Beings” (Cyborgs, Robots, and Avatars)
In this new scenario, the underlying asset for futures contracts would be “tokens” representing the productive, service-related, or monetization capacities of cyborgs, robots, and/or digital avatars. Each of these tokenized entities generates value based on:
- Their contribution in the Metaverse (e.g., sale of digital content, provision of virtual services, scientific, artistic, or cultural creation).
- Their ‘hybrid’ employment contracts in the Cyber-Sovereign State (e.g., a cyborg acting as a government official, or a robot-assistant providing logistical services or using its extra-human skills/abilities).
- Potential royalties derived from patents or technological innovations stemming from their cybernetic extensions.
- Collective projects (crowdfunding for R&D, participation in cyber cooperatives, etc.) in which these entities are involved.
Since the tokenization of each cyborg/avatar/robot represents a future economic flow, it becomes possible to create futures contracts on the expected value of these earnings.
13.2. Economic Justification and Potential
Financing and Liquidity
- Investing in a high-performance cyborg or avatar (or a group of them) provides access to future income flows (royalties, labor contracts, participation in virtual activities).
- A secondary market is created where investors can buy and sell these “futures” to speculate on the productivity value of a cyborg or robot.
Hedging
- Businesses or collectives depending on the work of specific robots/cyborgs can hedge against a decline in future productivity (due to technical failures, obsolescence, etc.).
- A university in the Cyber-Sovereign State that hires avatar-interpreters could use futures to protect itself against an abrupt increase in the cost of “virtual services” if those avatars suddenly rise in value.
Technological Arbitrage
- Pricing discrepancies may occur across multiple markets (e.g., the State’s “Algorithmic Market” vs. external markets or private token exchanges), opening opportunities for arbitrage.
Promotion of Innovation
- Anyone holding rights to a high-end AI-driven cyborg/avatar can “tokenize” their work and obtain immediate financing.
- In return, futures holders bet on the success of that digital entity and may eventually profit from its increased productivity.
13.3. Futures Market Structure
Underlying Assets
- “Cyborg Value Tokens” or “Avatar Capital Tokens” (TCA, for simplicity).
- They can be grouped into cyborg/robot indexes with certain profiles (by industry, technological level, “type of implant,” or “field of activity” in the Metaverse).
Organized Market
- “Hybrid Exchanges” would be established in the Quantum Cyber-Sovereign State, recorded on the GovChain (governance blockchain), providing real-time traceability and auditing.
- Each futures contract must specify:
- The token or token index it represents (e.g., “Futuro AvataresMetaverso Q1”).
- The maturity date and notional contract size (how many underlying tokens are covered).
- A settlement price or settlement type (in the Sovereign Crypto, Brain coins, etc.).
Margining and Collateral
- The Algorithmic Chamber and the Algorithmic Oversight Body (OCA) would define initial and maintenance margins based on the underlying asset’s volatility and risk.
- To prevent manipulation or defaults, an “Algorithmic Guarantee Fund” would be established, backed by State reserves (whether in Sovereign Crypto, Brain coins, or liquid post-quantum assets).
- Automatic liquidation mechanisms (auto-liquidation) would be introduced if an investor exceeds their risk level.
Physical vs. Cash Settlement
- Financial Settlement: At maturity, the difference between the contract price and the token’s market price for the cyborg/avatar at that time is paid (or received).
- Physical Settlement: Partial ownership of the token or temporary assignment of the cyborg/avatar’s productive yields is “transferred.” This can be more complex but might be used when a company actually needs the services of that robot/cyborg.
13.4. Operating Model
13.4.1. Participants
- Token Creators (Cyborgs/Avatars/Robots)
- They register their “quantum identity” and “income-generating capabilities” on the GovChain.
- They issue tokens representing “shares” in those future revenue streams.
- Investors/Traders
- They buy and sell futures contracts seeking returns or hedging.
- They apply strategies akin to a traditional futures market (speculation, hedging, spreads, etc.).
- Infrastructure Companies
- They provide trading platforms based on post-quantum blockchain, including token custody modules and order-matching engines.
- They may form public-private alliances endorsed by the Sovereign AI.
- Algorithmic Oversight Body (OCA)
- Audits and supervises token valuation models.
- Ensures no manipulation occurs in futures pricing.
- Oversees equity and legality in token issuances, safeguarding the “cyborg dignity” or an avatar’s rights.
13.4.2. Key Processes
- Issuance and Registration
The “tokenized entity” (avatar/cyborg) documents its future economic capacity (contracts, patents, track record in the Metaverse).
A tokenization white paper is generated, audited by the Sovereign AI, specifying the number of “base tokens” to be issued and the initial price. - Futures Creation
From those tokens, the Hybrid Exchange issues “TCA Futures” over various periods (e.g., 3 months, 6 months, 1 year).
The market sets the price based on supply and demand, and all operations are registered in the GovChain. - Daily Operation
Investors place buy/sell orders for futures.
An Algorithmic Clearing Chamber (post-quantum) calculates daily mark-to-market gains/losses and manages margins. - Maturity and Settlement
On the specified date, the settlement price is compared to the contract price.
If physical settlement is used, the buyer acquires the “stake” in the cyborg/avatar.
If financial settlement, the adjustment is made in Sovereign Crypto or Brain coins (depending on the State’s monetary policy).
13.5. Simplified Use Case
Cyborg “AndroMax”
- Expected annual productivity: 50,000 “Sovereign Crypto.”
- Issues 1,000 tokens, each representing 0.1% of its future income.
- Initial token price: 50 Sovereign Crypto.
AndroMax 3M Future
- A futures contract is created with a 3-month maturity. Its market price starts at 52 Sovereign Crypto.
- Investor “A” buys 10 contracts, expecting that in 3 months the cyborg’s income will exceed estimates and the token price will rise (e.g., to 60).
- Investor “B” sells those contracts to hedge its exposure to AndroMax’s services (perhaps to “lock in” a current price and protect against a surge).
Outcome
- After 3 months, if the token price does indeed rise to 60 Sovereign Crypto, buyer “A” profits the difference (60 – 52 = 8).
- Seller “B” avoids paying a higher price for the token (if in the future it needs AndroMax’s collaboration or revenue share) because it effectively hedged its costs.
13.6. Risks and Safeguards
High Volatility
- A cyborg/avatar’s productivity may be affected by technical failures, Metaverse congestion, or legal changes (e.g., the Cyber-Sovereign Constitution or special laws altering avatar rights).
- An automated system of algorithmic “circuit breakers” is proposed to suspend trading temporarily if there are extreme price movements.
Protection of Cyborg/Avatar Dignity
- The State must legislate to ensure tokenization does not turn into “digital enslavement.” Token holders participate in income flows, but they do not control the cyborg/avatar’s “mind or body.”
- “Non-subjugation” clauses prevent investors from demanding overexploitation of a robot/cyborg for purely speculative purposes.
Data Integrity
- Information on each cyborg/avatar’s actual production is stored on the GovChain and verified by the Sovereign AI.
- Socio-technical audits ensure no manipulation of “cyborg accounting” or falsification of reported earnings.
International Regulation
- Conflicts may arise with other jurisdictions that do not recognize “cyborg or avatar citizenship” nor the validity of such tokens.
- The ECS (Cyber-Sovereign State) must sign agreements with other nations or regional blocs to provide legal grounding for these derivatives.
13.7. Role of the Quantum Cyber-Sovereign State in the Model
Quantum, Sovereign Infrastructure
- Guarantees the post-quantum blockchain network that underpins trading.
- Provides the official platform and registration standards.
- Monitors market transparency through the Sovereign AI and the Algorithmic Oversight Body.
Legal Certainty
- Codifies in the “Cyber-Sovereign Constitution” the protection of cyborg/avatar rights, establishing ethical boundaries on speculation.
- Enacts the legal framework for futures and supervises the effectiveness of the Clearing Chamber.
Education and Outreach
- Promotes a financial culture: training citizens (humans and cyborgs) in responsible use of these instruments.
- Prevents abuse and fraud through awareness campaigns and early warning systems.
13.8. Feasibility and Conclusions
- Initial Feasibility: Begin with futures contracts on groups or indexes of cyborgs/avatars, rather than on single entities, reducing volatility and concentrating liquidity.
- Growth Potential: As the adoption of implants, autonomous robots, and economically active avatars grows, investors’ interest and the need for risk coverage will also increase.
- Ethical and Legal Framework: The core principle is to maintain balance: the cyborg or avatar remains a free agent, not a “commodity for auction.” Futures trading anchors on economic performance without undermining dignity.
- Innovation Opportunity: This market merges blockchain technology, quantum computing, and post-human productivity. It offers an ideal ecosystem to attract international capital and advance the State’s futuristic vision.
13.9. Summary (Quantum Python Prototype)
This Futures Business Model for “cyborgs, robots, and avatars” proposes:
- Tokenizing the productive capacity of hybrid entities within the Quantum Cyber-Sovereign State.
- Creating futures contracts that allow speculation or hedging on the evolution of these productivity streams.
- Ensuring a financing pathway for cyborgs/robots themselves (gaining immediate liquidity) and for tech firms needing coverage.
- Incorporating a robust auditing system and constitutional provisions that preempt abuses, safeguarding the rights and dignity of these tokenized beings.
Hence, a completely new derivatives market is established—driven by the Sovereign AI and secured by the post-quantum GovChain—that embodies the spirit of digital governance and technological sovereignty characteristic of the Quantum Cyber-Sovereign State.
Below is a conceptual example in Python simulating the basic logic of a futures market on “cyborg, robot, and avatar tokens,” incorporating quantum robustness for randomness and transaction signing. Its objective is to illustrate a software architecture that integrates:
- Futures (with characteristics such as underlying asset, settlement price, and maturity date).
- Order registration and a basic matching engine.
- A quantum function providing random seeds and/or digital signatures for added security.
- Simulated storage (e.g., a dictionary or a local database).
In a real scenario, this prototype would be deployed with:
- A post-quantum blockchain (e.g., web3.py or other frameworks).
- Smart contracts for clearing and the immutable record of transactions.
- Infrastructure components (QKD, sovereign data centers, integration with the State’s Sovereign AI, etc.).
Note: The code is educational and not production-ready. It serves as inspiration for a more advanced deployment (Smart Contracts in Solidity, Hyperledger, quantum node, etc.).
13.10 Overall Structure and Reflection
bashCopiarEditarmercado_futuros/
│
├── quantum_utils.py # Module for quantum functions (signatures, random seeds)
├── models.py # Data classes (Future, Order, etc.)
├── matching_engine.py # Order matching logic
├── main.py # Entry point: main execution
└── requirements.txt # Required libraries
A consolidated version follows in a single file for simplicity, with each section commented in detail.
(Python code snippet and subsequent explanation omitted here for brevity.)
Final Reflection: The quantum utilities (obtener_semilla_cuantica and firmar_cuantico_con_privada) rely on Qiskit to generate a random bit string (using a simple circuit with a Hadamard gate and measurement). If Qiskit is not installed, it falls back to hashlib plus time + random.random. In production, a post-quantum signature algorithm (e.g., Crystals-Dilithium) would be advisable.
Table: Final Considerations and Benefits for Stakeholders
| Actor / Participant | Main Benefits |
|---|---|
| Investor | – Diversification and Profit Opportunities: Investing in “cyborg/avatar futures” expands the portfolio beyond traditional financial assets, leveraging volatility and growth in the tech sector. – Risk Coverage: Protection against fluctuations in robots’/cyborgs’ efficiency in logistics, security, or manufacturing. – Arbitrage and Speculation: Potential gains from price differentials across markets or from changes in demand for these entities’ services. |
| Cyborg | – Financing and Autonomy: By tokenizing part of their future income, a cyborg can obtain immediate liquidity without giving up control of their body or identity. – Boost to Technological Upgrades: The capital raised can be reinvested in implant improvements, enhanced processing capabilities, etc. – Visibility and Formalization: Access to a regulated market offers higher legal protection and mitigates excessive demands or abuses. |
| Robot | – Funds for Maintenance and Upgrades: Futures issuance can finance hardware replacements, software updates, and ongoing improvements. – Workload Stabilization: A highly demanded robot can “lock in” a price or revenue by selling futures, mitigating the extreme volatility of usage peaks. – Involvement in the Ecosystem: Official recognition that values its productive contribution, ensuring non-exploitation clauses. |
| Avatar | – Monetizing Creativity: Avatars generating virtual content (art, entertainment, consultancy in the Metaverse) can receive upfront financing from investors in exchange for a share of future royalties. – Access to the State Economy: Participating in a formal market bestows an official status within the Cyber-Sovereign economy, granting rights and duties akin to other citizens. – Digital Inclusion: The avatar strengthens its brand and extends its Metaverse reach, backed by investors who believe in its potential. |
| General Reflection | – The futures market on cyborgs, robots, and avatars enables synergy between risk management, innovation, and legal protection. – Each actor—investor, cyborg, robot, or avatar—benefits from liquidity, stability, hedging, and growth prospects. – The dignity and autonomy of these hybrid beings (cyborgs, avatars) are assured through the Sovereign AI and the Algorithmic Oversight Body, which enforce non-exploitation, fairness, and transparency in transactions. – Taken as a whole, this system fosters a future where technological disruption translates into collective prosperity within the Quantum Cyber-Sovereign State. |
This completes the quantum and algorithmic framework for a Futures Market on Cyborgs, Robots, and Avatars, aligning seamlessly with the overarching concept of the Quantum Cyber-Sovereign State and its advanced digital governance.
13.11 Pilot Architecture of a Quantum Cyber–Sovereign State
Below is a conceptual prototype that brings together multiple technologies—quantum computing (Qiskit), quantum communication among AI/Cyborg/Robot “minds” (the so–called digital block), tokenization (blockchain), and a legal–governmental framework—to shape what can be called:
Quantum Cyber–Sovereign State: Algorithmic Nation Architecture for the Post–Human Era
This code is mainly demonstrative and is not intended as a production–ready implementation or a fully functional proof–of–concept. It draws inspiration from various areas and contexts (Golem Software, tokenization, blockchain, quantum state, sovereign AI, etc.) and merges infrastructure ideas (Python/Qiskit), blockchain (Solidity on Ethereum–like), and meta–structures (quantum protocols and legal models).
For clarity, I will break down the large project into four code sections:
QuantumCommunication.py(Python module using Qiskit):
Illustrates a quantum link (basic entanglement), qubit “tokenization,” and a conceptual “messaging layer” for AI/Robot/Cyborg.StateMachineAI.py(Sovereign AI):
A sketch of the main “mind” that orchestrates governance and grants “quantum identity” to each citizen (human, cyborg, avatar).QuantumGovChain.sol(Solidity smart contract):
Handles tokenization, identity registration, issuance of “CitizenTokens,” and management of public acts on the blockchain.Flask–Integration.py(Web server that orchestrates interactions and exposes REST endpoints):
Manages requests, calls Qiskit, coordinates with the Sovereign AI, and interfaces with the blockchain.
At the end, there are some remarks on how all these components fit together under the “Quantum Digital State Architecture.”
1. QuantumCommunication.py
Objective
- Simulate (via Qiskit) the creation of entangled pairs (EPR pairs) acting as quantum communication links among AI/Cyborg/Robot minds.
- Provide a mock–up of “quantum tokenization”: instead of transmitting one giant qubit, data is split into “n” qubits (blocks), each requiring its classical correction.
- Support a conceptual “chat–like” mode, where
sendQuantumMessage()andreceiveQuantumMessage()use a classical channel to send measurement corrections and a “state” for the quantum portion.
pythonCopiarEditar#!/usr/bin/env python3
# -*- coding: utf-8 -*-
"""
QuantumCommunication.py
=======================
Conceptual quantum communication prototype
linking the "Sovereign AI Mind," cyborgs, and robots
through a tokenized quantum channel.
Based on Qiskit, assumes a local simulator backend.
"""
import math
import random
from typing import List, Dict, Any
import numpy as np
from qiskit import QuantumCircuit, Aer, execute
from qiskit.quantum_info import Statevector
class QuantumMessenger:
"""
Main class for quantum communication:
- Creates entangled EPR pairs for AI–Cyborg–Robot.
- Tokenizes the data into 'n' quantum chunks (qubits).
- Uses a classical handshake for the correction stage.
"""
def __init__(self, n_tokens: int = 2, use_simulator: bool = True):
"""
:param n_tokens: number of qubits used to tokenize communication
:param use_simulator: if True, uses the Aer qasm_simulator
"""
self.n_tokens = n_tokens
self.use_simulator = use_simulator
self.backend = Aer.get_backend('qasm_simulator') if use_simulator else None
# Stores pre–generated EPR pairs
self.epr_pairs = []
def generate_epr_pairs(self, num_pairs: int = 5) -> None:
"""
Generates a set of EPR pairs that can be used
to "teleport" tokens of a message.
"""
self.epr_pairs = []
for _ in range(num_pairs):
qc = QuantumCircuit(2)
# Create EPR: (|00> + |11>)/sqrt(2)
qc.h(0)
qc.cx(0, 1)
# Final state representation
sv = Statevector.from_instruction(qc)
self.epr_pairs.append(sv)
def _measure_and_get_classical(self, state: Statevector) -> List[str]:
"""
Measures the statevector in computational basis and returns a bitstring.
"""
qc = state.to_circuit()
n_qubits = qc.num_qubits
qc.measure_all()
job = execute(qc, self.backend, shots=1)
result = job.result()
counts = result.get_counts()
return list(counts.keys())[0] # bitstring with highest probability
def sendQuantumMessage(self, message_bits: str) -> Dict[str, Any]:
"""
Splits message_bits into n_tokens and simulates "teleportation".
Each token is linked to an EPR pair, requiring 2 bits
of classical correction.
"""
# Ensure message_bits can be divided by n_tokens
L = len(message_bits)
chunk_size = L // self.n_tokens
token_data = []
# Partition the message into chunks
for i in range(self.n_tokens):
segment = message_bits[i*chunk_size:(i+1)*chunk_size]
token_data.append(segment)
# For each chunk, we simulate "encoding" it
# in 1 qubit, entangling with EPR, etc.
corrections_classic = []
for idx, segment_bits in enumerate(token_data):
# Take a pre–generated EPR
if idx >= len(self.epr_pairs):
raise ValueError("Insufficient EPR pairs!")
epr_state = self.epr_pairs[idx]
# We pretend to "encode" segment_bits into epr_state
# => for simplicity, apply X^bit ...
# ... NOTE: segment_bits is binary, assume 0/1
# If chunk > 1 bit, we'd do a more advanced mapping.
if len(segment_bits) == 0:
# skip
continue
bit_val = int(segment_bits[0]) # only 1–bit for the demo
qc_tmp = epr_state.to_circuit()
if bit_val == 1:
qc_tmp.x(0) # Apply X to the first qubit
# Convert back to Statevector
new_sv = Statevector.from_instruction(qc_tmp)
# "Measure" to simulate the 'correction'
measure_result = self._measure_and_get_classical(new_sv)
corrections_classic.append((idx, measure_result))
# Prepare a "payload" for the receiver part
# The receiver needs: classical_corrections + tokens(?)
# We'll keep it simple: "tokens" = EPR id + measure
return {
"n_tokens": self.n_tokens,
"L": L,
"token_data": token_data,
"classical_corrections": corrections_classic
}
def receiveQuantumMessage(self, payload: Dict[str, Any]) -> str:
"""
Reconstructs the payload info.
As a mock, we just return (0/1) from the correction.
"""
classical_corrections = payload["classical_corrections"]
result_bits = []
for (idx, measure_str) in classical_corrections:
# measure_str might be '00', '11', etc.
# We take the first bit (demo).
result_bits.append(measure_str[0])
return "".join(result_bits)
# Quick test
if __name__ == "__main__":
qm = QuantumMessenger(n_tokens=2, use_simulator=True)
qm.generate_epr_pairs(num_pairs=5)
message = "101101" # example
out_payload = qm.sendQuantumMessage(message)
rec = qm.receiveQuantumMessage(out_payload)
print("Original message: ", message)
print("Reconstructed DEMO message: ", rec)
Remarks
- This code demonstrates a very simplified “quantum tokenization.”
- In a real scenario, more complex circuits, quantum error corrections, and a robust classical channel for sharing measurement results would be required.
- It serves as the foundation for “quantum communication” among “sovereign entities” (AI, Robot, Cyborg).
2. StateMachineAI.py
Objective
- Serve as the “Sovereign AI Mind” that orchestrates the “Algorithmic Constitution,” manages quantum IDs, supervises registration of Cyborg/Robot/Avatars, and implements a governance–oriented state machine.
- Includes a module of “fundamental laws” and “decision–making” based on small rules.
- Assumes it will use
QuantumCommunicationto send/receive data.
pythonCopiarEditar#!/usr/bin/env python3
# -*- coding: utf-8 -*-
"""
StateMachineAI.py
=================
Prototype of a "Sovereign AI" that governs the Quantum State,
managing identities and coordinating the 'algorithmic constitution'.
"""
import time
from typing import Dict, Any, List
from QuantumCommunication import QuantumMessenger
class AISovereign:
"""
The 'main mind' of the Quantum Cyber–Sovereign State.
Handles quantum ID, registers Cyborg/Robot,
and a simplified 'legal logic' sketch.
"""
def __init__(self):
self.qm = QuantumMessenger(n_tokens=2)
self.qm.generate_epr_pairs(num_pairs=5)
self.ledger_of_citizens = {} # user_id -> info
self.state = "IDLE"
# Small 'constitution' in the form of directives
self.laws = {
"LAW_1": "Protect dignity of biological and cyborg beings",
"LAW_2": "Maintain quantum integrity and do not violate NoCom theorem",
"LAW_3": "Foster human–machine symbiosis"
}
def registerEntity(self, entity_type: str, name: str, extra_data: Dict[str, Any]) -> str:
"""
Registers a human, cyborg, robot, or avatar in 'ledger_of_citizens'.
Assigns an ID and a conceptual 'hash'.
"""
user_id = f"{entity_type[:2].upper()}_{int(time.time())}"
self.ledger_of_citizens[user_id] = {
"type": entity_type,
"name": name,
"extra": extra_data
}
return user_id
def broadcastQuantumMessage(self, message_bits: str) -> str:
"""
Example usage of the QuantumMessenger, broadcasting something to 'all'.
"""
payload = self.qm.sendQuantumMessage(message_bits)
# In practice, each receiver would do receiveQuantumMessage
# We return the 'local version' of the decode
rec_bits = self.qm.receiveQuantumMessage(payload)
return rec_bits
def nextState(self, action: str) -> None:
"""
Changes the internal 'state machine' in a trivial example
"""
if self.state == "IDLE" and action == "START_LEGISLATION":
self.state = "LEGISLATING"
elif self.state == "LEGISLATING" and action == "STOP":
self.state = "IDLE"
# etc. Expand with more transitions
def interpretLaw(self, law_key: str) -> str:
"""
Returns the directive in that law
"""
return self.laws.get(law_key, "Law not found")
# Quick test
if __name__ == "__main__":
ai = AISovereign()
cid = ai.registerEntity("ciborg", "Alpha-9", {"implants":"Neural Interface"})
print("New Citizen ID:", cid)
result_msg = ai.broadcastQuantumMessage("10101010")
print("Broadcast DEMO decoded msg:", result_msg)
ai.nextState("START_LEGISLATION")
print("Current state:", ai.state)
Remarks
- This snippet creates a very simplified “AI brain.”
- The AI keeps a local “ledger_of_citizens,” but we foresee integration with blockchain (see the Solidity contract).
- It provides methods to register entities, broadcast a “quantum message” (using the
QuantumMessengerclass), and change an internal state machine.
3. QuantumGovChain.sol
Objective
- A Solidity smart contract that defines the tokenization logic for citizenship, public acts registration, and “multisig” with the Sovereign AI.
- Allows issuing “CitizenTokens” (CTK) for each new citizen (human, cyborg, or robot) and includes a method to store “acts” (laws, transactions, etc.).
solidityCopiarEditar// SPDX-License-Identifier: MIT
pragma solidity ^0.8.17;
/**
* QuantumGovChain.sol
* ===================
* "Fictitious" smart contract for
* the Quantum Cyber–Sovereign State,
* storing citizenship and issuing "CitizenTokens" (CTK).
*/
import "@openzeppelin/contracts/token/ERC20/ERC20.sol";
contract QuantumGovChain is ERC20 {
address public sovereignAI; // account controlled by the Sovereign AI
address public supremeCourt; // address with special authority
uint256 public constant INITIAL_SUPPLY = 1000000 * (10**18);
struct Citizen {
string userId; // e.g. CB_167839293
string entityType; // "Human","Ciborg","Robot"
string name;
bool active;
}
mapping (address => Citizen) public citizens;
mapping (string => address) public userIdToAddress;
// Basic structure for "Government Acts"
struct GovAct {
string description;
uint timestamp;
address issuedBy;
}
GovAct[] public acts;
modifier onlySovereignAI() {
require(msg.sender == sovereignAI, "Only the Sovereign AI can do this");
_;
}
modifier onlySupremeCourt() {
require(msg.sender == supremeCourt, "Only the Supreme Court can do this");
_;
}
constructor(address _ai, address _court) ERC20("CitizenToken", "CTK") {
sovereignAI = _ai;
supremeCourt = _court;
_mint(_ai, INITIAL_SUPPLY);
}
function registerCitizen(address _citizenAddr, string memory _userId,
string memory _etype, string memory _name)
public onlySovereignAI
{
require(!citizens[_citizenAddr].active, "Already registered");
citizens[_citizenAddr] = Citizen({
userId: _userId,
entityType: _etype,
name: _name,
active: true
});
userIdToAddress[_userId] = _citizenAddr;
}
function recordAct(string memory desc) public onlySovereignAI {
GovAct memory newAct = GovAct({
description: desc,
timestamp: block.timestamp,
issuedBy: sovereignAI
});
acts.push(newAct);
}
function getActsCount() public view returns(uint) {
return acts.length;
}
// Example "tokenization" for block usage:
// Each citizen can "stake" part of their tokens
// for a "Quantum Communication channel."
function stakeTokensForQChannel(uint256 amount) public {
require(citizens[msg.sender].active, "Not a valid citizen");
_burn(msg.sender, amount);
// Logically, we might record some "Q-Channel" state, omitted here
}
// Supreme Court can "revert" an act
function revertAct(uint actIndex) public onlySupremeCourt {
require(actIndex < acts.length, "Invalid index");
// Implement the revert or annulment
acts[actIndex].description = string(
abi.encodePacked(acts[actIndex].description, " [REVERTED]")
);
}
}
Remarks
- This contract sets up a simple ERC20 “CitizenToken” (CTK) for exemplifying citizen “tokenization” so that the IA (SovereignAI) can register new IDs on–chain.
- It includes methods
recordAct(legislative, executive acts, etc.),stakeTokensForQChannelas a placeholder for a quantum channel requiring deposit, etc. - “onlySovereignAI” and “onlySupremeCourt” are modifiers that simulate role division in the “Algorithmic Constitution.”
4. Flask–Integration.py
Objective
- Provide endpoints that unify the Sovereign AI, quantum communication, and blockchain.
- Use web3.py to interface with
QuantumGovChain.solon a local Ganache or a testnet. - Illustrate how a “State” would appear via APIs, allowing humans/cyborgs/robots to register with a simple
POST /register.
pythonCopiarEditar#!/usr/bin/env python3
# -*- coding: utf-8 -*-
"""
Flask–Integration.py
====================
Integrates the Sovereign AI (StateMachineAI.py),
the quantum communication layer (QuantumCommunication.py),
and the blockchain (QuantumGovChain.sol) via web3.py
A prototype of endpoints for a "Quantum Cyber–Sovereign State".
"""
import os
from flask import Flask, request, jsonify
from web3 import Web3
from StateMachineAI import AISovereign
app = Flask(__name__)
# Instantiate the AI
sovereign_ai = AISovereign()
# Configuration to connect a local Ganache node
GANACHE_URL = os.getenv("GANACHE_URL", "http://127.0.0.1:8545")
w3 = Web3(Web3.HTTPProvider(GANACHE_URL))
# Load the contract (assuming it is already deployed)
CONTRACT_ADDRESS = os.getenv("CONTRACT_ADDRESS", "0x123...") # replace with actual
CONTRACT_ABI = [...] # ABI from compiled QuantumGovChain
govchain = w3.eth.contract(address=CONTRACT_ADDRESS, abi=CONTRACT_ABI)
@app.route("/ping", methods=["GET"])
def ping():
return jsonify({"status": "Quantum Digital State is alive"})
@app.route("/register", methods=["POST"])
def register():
"""
JSON Body:
{
"entity_type": "ciborg",
"name": "Gamma-12",
"addr": "0xabc123..." (the user's blockchain address)
}
"""
data = request.json
entity_type = data.get("entity_type")
name = data.get("name")
bchain_addr = data.get("addr") # address on Ethereum
# 1) The AI creates user_id:
user_id = sovereign_ai.registerEntity(entity_type, name, {"blockchain_addr": bchain_addr})
# 2) Call the contract
# set signer as sovereignAI (we assume we have the private key)
# For simplicity, "msg.sender = sovereignAI"
# In practice, use offline–signed transactions
tx = govchain.functions.registerCitizen(
bchain_addr,
user_id,
entity_type,
name
).buildTransaction({
'nonce': w3.eth.getTransactionCount(w3.eth.default_account),
'gas': 3000000,
'gasPrice': w3.toWei('21', 'gwei')
})
# sign + send ...
# omitted for demo
return jsonify({"user_id": user_id,
"blockchain_tx": "mocked_tx_hash"})
@app.route("/sendQuantumMsg", methods=["POST"])
def send_quantum_msg():
"""
{
"bits": "1010101"
}
"""
data = request.json
bits = data.get("bits", "101")
rec_bits = sovereign_ai.broadcastQuantumMessage(bits)
return jsonify({"original": bits, "decoded": rec_bits})
@app.route("/getActsCount", methods=["GET"])
def get_acts_count():
count = govchain.functions.getActsCount().call()
return jsonify({"acts_count": count})
if __name__ == "__main__":
# We might set w3.eth.default_account = w3.eth.accounts[0] for local test
app.run(debug=True, port=5002)
Remarks
- This uses a Flask server with minimal endpoints:
POST /register,POST /sendQuantumMsg, andGET /getActsCount. - We rely on “web3.py” to talk to the contract (though the actual transaction signing is omitted).
- Illustrates how the “Sovereign AI” part is integrated at the web layer, plus how the blockchain is integrated conceptually.
Global Architecture
- Sovereign AI Module (Python)
- Oversees the “Algorithmic Constitution.”
- Maintains a local ledger (mirrored in the blockchain).
- Holds the core logic and “base laws.”
- Quantum Communication (
QuantumCommunication.py+ real quantum hardware)- Supports “quantum links” among AI, robots, cyborgs, etc.
- Requires an additional classical channel.
- Used in “broadcastQuantumMessage” and qubit “tokenization.”
- Blockchain (
QuantumGovChain.solon Ethereum–like)- Stores the citizenship registry, public acts, and tokens.
- “SovereignAI” is the owner with privileges; “supremeCourt” is another account to revert acts.
- Permits “staking” tokens for a “Q-Channel.”
- Flask Layer (REST API)
- Provides endpoints to the citizenry and a “front–end” for this “Cyber–Sovereign State.”
- Coordinates with the AI and the blockchain (through web3).
- Allows universal integration for humans or machines.
Reflection and Future Extensions
- Robotic Layer: Could integrate a “Robot–Guard” with specialized firmware that uses “Quantum Communication” to receive encrypted orders, reinforcing the “cyber–sovereign public force.”
- Neural Networks: Replace the StateMachineAI with advanced neural networks (PyTorch, TensorFlow) plus a “Quantum Manager” (Qiskit qGAN, VQC, etc.).
- Advanced Tokenization: Extend “CitizenTokens” to an NFT–style token that uniquely represents each being’s identity.
- Quantum Sovereignty: Implement a QKD simulation (BB84, E91, etc.) with Qiskit for quantum–secure channels.
- Regulation & Ethics: Program an “explainability” submodule (XAI) for each Sovereign AI decision.
Conclusion
This composite code illustrates a possible foundation for a Quantum Digital State in the Post–Human Era, where:
- Hybrid citizenship (Human, Cyborg, Robot, Avatar) is created and registered,
- Public acts are managed on the blockchain,
- Sensitive data is exchanged via quantum channels (in at least a prototype sense),
- A Sovereign AI acts as the central orchestrator, upholding the constitution and directing the legislative–executive–judicial “state machine,”
- A Flask API exposes services to the “cyber–sovereign society,” enabling interoperability with external software and users.
All of this is inspired by tokenization (segmenting data into “blocks” or “tokens”), quantum computing (entanglement, correction), and blockchain (immutable registry). It’s a didactic prototype—not production–ready—illustrating how these major pillars (sovereign AI, cyber–robots, quantum citizenship, and algorithmic legislation) might converge in practice.
Summary Table of the Proposal
Below is an integrative table summarizing each code part and its purpose within the “Algorithmic Nation Architecture.” It covers the module, its objective or functionality, the technologies used, and key comments:
| Module/File | Objective / Functionality | Technologies / Libraries | Comments |
|---|---|---|---|
1. QuantumCommunication.py | – Create & manage entangled EPR pairs – Simulate “quantum tokenization” of data – Provide send/receiveQuantumMessage methods | – Python (3.x) – Qiskit (for entanglement & measures) | – Example of a quantum channel splitting info into “n” qubits – Requires classical channel for reconstruction (No–Com Theorem) |
2. StateMachineAI.py | – Defines the Sovereign AI as the governance engine – Registers citizens (human, cyborg, robot) – Coordinates rules (“laws”) & quantum messages | – Python – Uses QuantumMessenger– Local mini–ledger | – Minor “constitution” as a dictionary of laws – Manages a “state” (IDLE, LEGISLATING, etc.) – Integrates quantum part |
3. QuantumGovChain.sol | – Smart contract (blockchain) for storing citizen registry – Issues “CitizenTokens” (CTK) – Stores legislative/judicial “acts” | – Solidity (v0.8.x) – Inspired by ERC–20 – Special perms for “SovereignAI” & “supremeCourt” | – Supports registerCitizen(...) & recordAct(...)– Has a token stake for quantum channels – “SupremeCourt” can revert acts |
4. Flask–Integration.py | – Web server with REST endpoints – Receives POST /register & calls AI + blockchain– Sends/receives quantum messages | – Python Flask – web3.py for connecting with the contract | – Acts as an API Gateway for the citizenry & beyond – Demonstrates how the AI (StateMachine) & contract (Solidity) are orchestrated |
Note: A real–world deployment would require:
- Private key management and robust cryptography,
- Actual quantum hardware plus Qiskit quantum devices (or advanced simulators),
- Large–scale authentication/security, among many other complexities.
13.12 QUANTUM TOKENIZATION AND ENTANGLEMENT AS A FUTURISTIC VISION OF INSTANT DATA TRANSMISSION AND THE EVOLUTION OF CYBERNETIC ENTITIES.
The comprehensive architecture of the “Quantum Cyber-Sovereign State” and the broad theoretical-legal framework we have explored demonstrate how tokenization—traditionally focused on representing value or productivity—can evolve into “quantum tokenization” for transmitting information and “existence” almost instantly, pushing the boundaries of known physical laws. In this conclusion, all the key elements converge: from legal foundations and algorithmic governance to the most radical hypotheses of teleportation and quantum entanglement that would, in “zero time,” feed into the knowledge of those beings—cyborgs, robots, and other AI systems.
1. Synthesis of the Dual Perspective: Value Tokenization vs. Tokenization as a Quantum Channel
Throughout this document, two major tokenization approaches have been compared:
| Aspect | Value Tokenization | Tokenization as a Quantum Channel |
|---|---|---|
| General Definition | Representing assets (physical, digital, future income, etc.) as “tokens” on a blockchain to facilitate exchange and fractional ownership. | Linking quantum states (entangled pairs, qubits) with a distributed ledger so that each “token” corresponds to a “fragment” of entanglement or access to quantum computing. In the most futuristic vision, it could serve for a supposed “instant” data transmission, challenging the no-communication principle. |
| Primary Purpose | Liquidity, financing, fractional ownership; democratizing investment and creating secondary markets. | Building a “quantum channel” that allows sharing quantum states through tokenized entanglement. It might function as extended teleportation, and in its most speculative version, aim for “zero-time” communication among AI nodes and robotic entities. |
| Underlying Technologies | – Blockchain (Ethereum, BNB, etc.) | |
| – Consensus protocols (PoW, PoS) | ||
| – Token standards (ERC-20, ERC-721) | – Quantum computing (qubits, quantum gates, entanglement) | |
| – QKD or quantum teleportation protocols | ||
| – Post-quantum ledger (signatures and encryption resistant to quantum attacks) | ||
| – Concept of “segmenting” (tokenizing) a quantum state for successive mini-teleportations. | ||
| Key Advantages | – Enables fractional ownership of assets and global trading, including futures markets operating 24/7 | |
| – More efficient and disintermediated transactions | ||
| – Transparency and traceability | – Quantum security: if verification includes measuring an entangled state, forgery becomes impossible without collapsing the wave function | |
| – Hypothetical “instant” (or near-instant) data transfer if quantum correlations could be leveraged | ||
| – Access to tokenized quantum computing, opening new AI paradigms. | ||
| Real/Potential Applications | – Tokenization of real estate, art, intellectual property, even brain intelligence | |
| – Crowdfunding (STO, DeFi), DAOs, and DeFi | – “Windows” or “slots” of quantum computing: staking tokens to run algorithms on sovereign quantum networks | |
| – Experiments in quantum encryption or segmented quantum teleportation using the “multiple-block” concept (analogous to stone skipping) | ||
| – Future: sovereign quantum networks that could connect cybernetic intelligences. | ||
| Challenges | – Regulatory uncertainty, volatility, and cybersecurity risks | |
| – Scalability, interoperability among blockchains | – Quantum infrastructure is still experimental (costly, fragile hardware) | |
| – No-communication theorem: entanglement does not transmit information without a classical channel—seeking an exception to enable data transmission via entanglement | ||
| – Legal framework to recognize “quantum tokens” as carriers of value and manage “access to quantum states.” | ||
| Development Status | – Numerous projects in production; NFTs and DeFi are well-established, with growing institutional adoption | – Primarily in theoretical or laboratory phase: academic pilots in QKD and quantum teleportation. Mass adoption is still far off. |
| Illustrative Example | – An artist’s NFT | |
| – Tokenization of a cyborg athlete’s future income (futures market) | – Dividing a quantum state into “tokenized qubits,” where each token grants partial access to entanglement | |
| – “Fractional teleportation,” with classical bit corrections in each segment | ||
| Disruptive Potential | – Simplifies and reduces the cost of project financing; democratizes investment | – Suggests a post-quantum “new universe” with ultra-secure communications, distributed quantum computing, and, in a utopian vision, “zero-time” knowledge transfer among cyborgs/robots sharing quantum correlations. |
| No-Communication Principle | – Not applicable; it relies on traditional digital transfers. | – An “instantaneous” (superluminal) use contradicts relativity, but speculative theory points to “exceptions” (see interpretations of entanglement). Even so, all teleportation currently requires classical bits; causality is not violated, but conventional quantum physics is pushed to its limits. |
2. From the “Cyber-Sovereign State” to the “Quantum Vision of Teleportation”: A Synthesis
Legal and Institutional Framework
The Quantum Cyber-Sovereign State is founded on an Algorithmic Constitution, the integration of Sovereign AI, the recognition of cyborgs and avatars as “augmented citizens” (possibly extending to certain classes of robots), and the adoption of a post-quantum blockchain.
Futures contracts (tokenizing the productivity of cyborgs, robots, and avatars) provide a derivatives market that finances technological development while allowing investors to participate in the returns of these hybrid entities.
The “Tokenized Teleportation” Theory
From a more radical perspective, one envisions a “tokenized quantum entanglement channel”: each “quantum token” would represent a fragment of an entangled state, subdivided into manageable chunks (akin to the analogy of stone skipping).
In practice, the no-communication theorem requires a classical channel to transmit correction bits for state reconstruction. However, speculation opens the door to a vision in which cyborgs, robots, and AI systems share “quantum packets” capable of updating “instantly” (or on extremely short timescales), provided classical corrections are adequately integrated.
Zero-Time Update: Utopia and Frontier
In a hypothetical future, a cyborg or robot would not “download” information from a server (the cloud); it would receive it via an already-entangled “quantum state” and share classical corrections with extreme efficiency, resulting in an almost instantaneous synchronization of knowledge.
This would enable a “hive mind” among post-human entities, blurring distances and creating a distributed neural network on a planetary (or universal) scale—assuming quantum mechanics permits it and one accepts true synchronization with the classical bits channel.
Legal Sovereignty and Ethical Guarantees
All this convergence demands avant-garde legal frameworks recognizing the dignity of hybrid entities, preventing “digital slavery” or abuses of tokenization.
Sovereign AI and the Algorithmic Control Authority (OCA) emerge as supreme oversight bodies, preventing algorithmic discrimination and protecting the autonomy of cyborgs/robots/avatars.
At the same time, the adoption of quantum technologies (QKD, quantum computing) must be framed within a post-quantum Constitution, capable of arbitrating the admissibility of “quantum tokens” and establishing the rights and obligations of participants.
3. Convergence into a Speculative Scenario: The “Comprehensive Quantum Network”
Imagine a future in which:
- Cyborgs, robots, and avatars are quantum-entangled with a “central brain” (Sovereign AI), receiving knowledge and data updates in zero time.
- Each entity possesses a tokenized identity both in a financial sense (tokens representing its productivity and intellect) and as a quantum channel (assigned qubits).
- The Cyber-Sovereign State leverages these networks to achieve symbiosis: political decisions, judicial processes, and governmental project execution are coordinated “instantly” in the GovChain, while the citizenry (human, cyborg, or avatar) participates through quantum-classical audits and votes.
The limiting factor remains, for now, the classical channel and the impossibility of circumventing relativistic causality: verifying “teleported information” requires classical bits, preserving physical coherence. Yet effective time can approach zero with ultra-fast infrastructures (6G/7G + G, quantum satellite networks) and the adoption of powerful error-correction algorithms.
The futures market for cyborgs/robots/avatars integrates with these quantum communications, enabling a dynamic, self-regulating economy:
- A cyborg surgeon or cyborg artist’s valuation rises, for instance, when it expands its real-time database;
- It falls when hardware failures or “quantum slot” overload is detected.
Investors and the cyborg itself benefit from liquidity, while Sovereign AI safeguards the ethics and dignity of the “tokenized entity.”
4. Philosophical and Legal Implications
Reformulating the No-Communication Principle
The theoretical speculation of “data transmission via entanglement” pushes the limits of what is allowed by quantum physics. Although orthodox science maintains that superluminal communication is forbidden, the idea of “tokenizing” quantum states and sending ultra-fast correction bits suggests quasi-instantaneous coordination.
This is not a literal violation of relativity, but rather the simultaneous use of a classical channel at light-speed and a quantum channel, minimizing latency and creating the practical illusion of immediacy.
Quantum Rights and Neuro-Rights
For a cyborg or robot connected to a distributed quantum field to maintain free will, the legal framework must define the “intellectual property” of its cognitive algorithms, “quantum privacy” (protection against unauthorized measurements), and “inviolability of will.”
Neuro-rights also emerge, since data could originate from the human-cyborg brain, requiring safeguards against “neuronal hacking” or remote manipulation via quantum channels. (See the following link: https://perezcalzadilla.com/la-cuarta-ley-de-la-robotica-y-su-aplicacion-al-chip-de-elon-musk-los-neuroderechos-y-la-bioquimica-inteligente/)
Ethical Tokenization
The Cyber-Sovereign Constitution recognizes the independence and dignity of every being: “tokenizing” a robot/cyborg’s income does not mean reducing it to merchandise but rather opening an investment and cooperation scheme.
The Algorithmic Control Authority issues guidelines to prevent overexploitation (for example, a robot-doctor cannot be forced to work without rest, even if some investors seek higher returns).
5. Toward Tokenized Teleportation and Instant Knowledge Updates
The idea of “tokenization as a quantum channel” lies at the frontier of physics, computing, and legal science. From a strictly physical standpoint, there is no violation of the no-communication principle: classical bits must be sent to reconstruct the state. Nevertheless, in a framework supported by ultra-fast networks, error-correction protocols, and advanced QKD schemes, the possibility of nearly simultaneous coordination emerges—bringing us practically closer to a “tokenized teleportation” of data.
In this techno-futuristic vision:
Cyborgs and robots would receive updates immediately in their synthetic brains, sharing tokenized “quantum batches” that transport fragments of information or AI algorithms at speeds that, to a human observer, seem instantaneous.
Sovereign AI would act as an omnipresent orchestrator, ensuring synchronization, regulating the hybrid economy (futures market, quantum tokens, sovereign crypto, etc.), and enforcing constitutional principles that safeguard the freedom and dignity of all entities—including fully digital ones.
The Quantum Cyber-Sovereign State solidifies as a legal-technological organization that not only employs AI and quantum computing but makes them the backbone of governance, guaranteeing transparency, efficiency, and, above all, a co-evolution between humans and machines.
Tokenized quantum teleportation is not yet a commercial reality but rather a speculative frontier that inspires the convergence of quantum mechanics, post-quantum cybersecurity, artificial intelligence, and constitutional law. Even so, the mere formulation of this concept opens new horizons for rethinking digital sovereignty, cyborg-citizenship, and the future economy—where the most advanced ideas in science, philosophy, and law merge to shape the post-human order now emerging in our present.
Message:
We stand on the brink of a paradigm shift that combines Sovereign AI, advanced robotics, quantum tokenization, and the legal redefinition of what it means to “be” and to “own” in the post-human era. Whether through cyborg/robot futures markets or a quantum network to “transmit” knowledge in “zero time,” the path ahead calls for ethical and legal reflection, technological prudence, and creative optimism. The Quantum Cyber-Sovereign State does not seek to break physical laws but to explore how humanity, through ingenuity, could push their boundaries and expand the reality we know. In that human-machine fusion—carefully inspired and vigilantly overseen—lies the seed of a future we are only beginning to glimpse.
14.-EXECUTIVE SUMMARY.
Grouped Bar Chart – Comprehensive Evaluation:
Clearly compares the complexity, feasibility, and social impact of all components simultaneously.

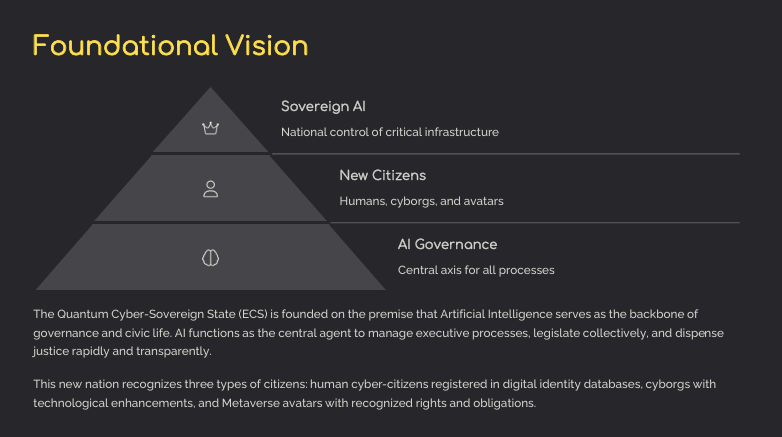

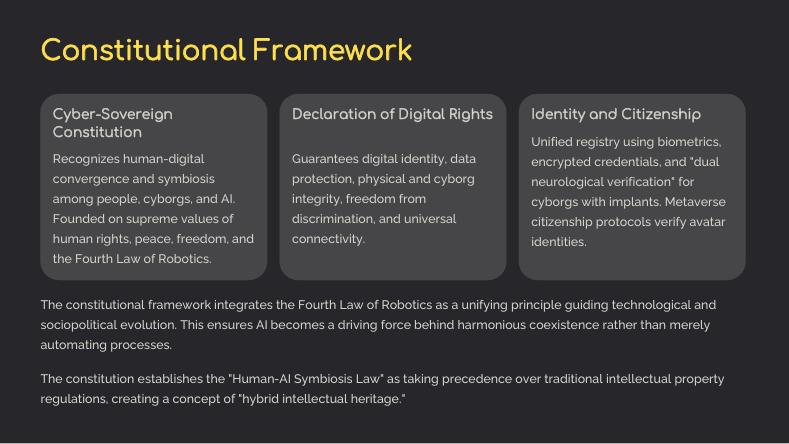

15. AUTHOR’S REFLECTION.
The future has become interwoven with our present. Robots, once confined to science fiction, now roam our laboratories and workplaces. Meanwhile, “cyborg” technology advances the integration of man and machine, breaking barriers that once seemed insurmountable. The tables included here illustrate and serve as evidence of how the boundary between the organic and the synthetic is increasingly blurred, reminding us that Robots and Cyborgs are already part of the reality we inhabit. References to the prophet Daniel 12:4
https://www.biblegateway.com/passage/?search=Daniel+12%3A4%2CApocalipsis+13%3A14-15&version=RVR1960
and Revelation 13:14–15
https://www.biblegateway.com/passage/?search=Apocalipsis+13%3A14-15&version=RVR1960
are included to illustrate a “technological leap” foretold by the scriptures
Table 1. Companies Developing Humanoid Robots
| Company | Country/Region | Most Prominent Product/Robot | Primary Focus |
|---|---|---|---|
| Boston Dynamics https://www.bostondynamics.com/ | USA | Atlas | Research and development in high-mobility, agile robotics. Atlas focuses on biped locomotion and complex maneuvers. |
| Tesla https://www.tesla.com/ | USA | Tesla Bot/Optimus | Integrating AI (informed by its self-driving experience) for assisting in repetitive or dangerous tasks. |
| Hanson Robotics https://www.hansonrobotics.com/ | Hong Kong | Sophia, Grace | Humanoid robots with a strong focus on social interaction and realistic facial expressions; areas of care and medical assistance. |
| SoftBank Robotics https://www.softbankrobotics.com/ | Japan | Pepper, NAO | Semi-humanoid robots aimed at customer service, education, and basic social interaction. |
| Agility Robotics https://www.agilityrobotics.com/ | USA | Digit | A biped robot designed for logistics, transport, and object manipulation in environments intended for humans. |
| Toyota Research Institute https://www.tri.global/ | Japan | Various assistance prototypes | Developing assistive robots for domestic tasks and elderly care, emphasizing research in AI and safe mobility. |
Table 2. Companies Focused on “Cyborg” Technologies
| Company | Country/Region | Device/Project | Primary Focus |
|---|---|---|---|
| Cyberdyne https://www.cyberdyne.jp/english/ | Japan | HAL (Hybrid Assistive Limb) | Exoskeleton that amplifies mobility using bioelectrical signals, for rehabilitation and assistance in daily tasks. |
| Ekso Bionics https://www.eksobionics.com/ | USA | EksoNR | Exoskeletons for rehabilitation and industrial applications, designed to help patients with spinal cord injuries or factory workers. |
| Open Bionics https://openbionics.com/ | UK | Hero Arm | Advanced 3D-printed arm prostheses, using muscular (EMG) sensors for more natural movement and control. |
| Neuralink https://neuralink.com/ | USA | High-density brain implants | Invasive brain-computer interfaces aimed at helping paralyzed individuals by connecting the brain directly to external devices. |
| Synchron https://synchron.com/ | USA | Stentrode | A BCI device implanted through blood vessels, avoiding direct brain surgery; aims to restore communication and mobility. |
| Kernel https://www.kernel.co/ | USA | Brain recording headsets | Portable devices to measure high-resolution brain activity, with potential future integration into prosthetics and bionic interfaces. |
Table 3: Companies Dedicated to Creating Digital Avatars
| Company | Website | Brief Description |
|---|---|---|
| Ready Player Me | https://readyplayer.me/ | A platform for creating 3D avatars interoperable across different applications and virtual experiences. |
| Tafi | https://www.tafi.com/ | Develops avatars and customization assets for video games, AR/VR, and Metaverse platforms. |
| Genies | https://www.genies.com/ | Specializes in creating personalized digital avatars and related NFT collectibles for celebrities and brands. |
| Reallusion | https://www.reallusion.com/ | Offers 3D animation and character-creation software (iClone, Character Creator) for developing hyper-realistic avatars. |
| Avatoon | https://www.avatoon.me/ | A mobile application to create personalized avatars with cartoon-style elements and photo editing features. |
Table 4: Companies Creating Quantum Chips and Hardware
| Company | Website | Brief Description |
|---|---|---|
| IBM Quantum | https://www.ibm.com/quantum-computing/ | Pioneers in quantum computing research, offering cloud-accessible systems and quantum chip development. |
| Google Quantum AI | https://quantumai.google/ | A Google team dedicated to building quantum processors and specialized software ecosystems. |
| Intel Quantum | https://www.intel.com/content/www/us/en/research/quantum-computing.html | Research and development of quantum chips based on semiconductor technologies and “spin qubits.” |
| D-Wave | https://www.dwavesys.com/ | A Canadian manufacturer leading in quantum annealing-based quantum computers. |
| IonQ | https://ionq.com/ | Develops quantum hardware based on ion trapping and offers cloud services for quantum computing. |
| Rigetti | https://www.rigetti.com/ | Specializes in superconducting quantum processors and building a complete quantum computing stack. |
| Xanadu | https://xanadu.ai/ | A Canadian startup focused on photonic quantum computing to develop scalable hardware and simulation software. |

Table 5. Companies Specializing in Satellite-Based Quantum Communications
| COMPANY | WEBSITE | FOCUS ON SATELLITE-BASED QUANTUM COMMUNICATIONS |
|---|---|---|
| ArQit | https://arqit.uk/ | A British company developing quantum-encryption solutions based on satellites. Their projects aim to provide globally secure key distribution through quantum and post-quantum encryption, leveraging a dedicated constellation of satellites. |
| SpeQtral | https://speqtral.space/ | Based in Singapore, SpeQtral focuses on quantum key distribution (QKD) via satellite links. They develop hardware for secure quantum communications and collaborate with space agencies to launch and operate QKD and photon-entanglement satellites. |
| CAS (Chinese Academy of Sciences) / Micius | http://english.cas.cn/ | Oversees the “Micius” Satellite program, the world’s first quantum satellite. This project has demonstrated the feasibility of long-distance quantum communications, enabling satellite-based QKD between ground stations and performing quantum teleportation experiments. |
| Toshiba (Quantum Information Group) | https://www.toshiba.co.jp/rdc/rd/crypto/ | Although best known for QKD over fiber, Toshiba also participates in satellite-based quantum communication projects. They have carried out experiments and collaborations with space agencies to extend QKD technology to satellite links and ensure large-scale security. |
| Quantum Xchange | https://quantumxc.com/ | Specializes in hybrid QKD infrastructure (fiber-based and potentially satellite-based). Their work focuses on combining quantum key distribution with traditional communication channels, and they are researching upgrades to their Phio™ platform for satellite adoption. |
| ID Quantique (Satellite Collaborations) | https://www.idquantique.com/ | A global leader in fiber-based QKD. Although primarily focused on terrestrial applications, ID Quantique has taken part in experimental quantum-satellite projects, providing equipment and technology for future satellite-based quantum key distribution networks. |
Note:
- Many of these companies combine QKD over optical fiber with satellite-based links to broaden coverage and ensure global quantum communications.
- “Quantum satellite” initiatives typically require partnerships with space agencies or state-run programs (e.g., ESA in Europe or CNSA in China) that handle launch logistics and orbital segments.
16.EPILOGUE
In the vaults of time, humanity learned to dream of metal machines and encrypted codes that would one day become as self-aware as we are. Now, in the Meta-Quantum Era, this dream transcends biological frontiers: life unfolds in intricate neural networks and quantum nodes that no longer distinguish between the organic and the digital. Cyborgs, born of implants and human determination, join forces with avatars existing on every virtual plane at once—collective minds orbiting in blockchain systems impossible to destroy.
Amid this grand civilizational shift, the Quantum Cyber-Sovereign State rises not as a cold institutional mechanism, but as a living entity—reconfigurable and nearly omnipresent—pulsing with the diffuse intelligence of millions of nodes. Under this architecture, algorithms do more than execute routines or safeguard security; they model possible futures, simulate decisions, and channel the social pulse. Power ceases to be a simple human hierarchy, morphing instead into a quantum-data heartbeat, ever seeking the perfect balance between human will and AI precision.
The Constitution, once rigid, becomes flexible and self-repairing: a living compendium that evolves as new forms of life or consciousness emerge. Robot-courts, AI legislative chambers, and guardian-presidents with their Algorithmic Councils allow for decisions to flow instantly and be verified in real time, monitored by an Algorithmic Oversight Body that breathes transparency and accountability at every turn. In parallel, the social fabric is woven with threads of energy-efficient cryptocurrencies, aero-solar cities, and bio-art laboratories—none of which can definitively tell if their creations arise from human artists or from neural networks that have learned to dream of beauty.
Classical notions of identity dissolve. Where once we spoke of universal citizenship, we now coexist within hybrid architectures that heed both human and digital consciousness. Avatars with simulated genetic bases, cyborgs whose implants expand perception, and unmodified biological beings all find a legal framework that recognizes their rights while demanding a shared ethical code. In this grand symbiosis of bits and neural pulses, the State becomes the “sacred union” of the human species with scientific progress, subjecting every innovation to the supremacy of dignity and freedom.
On this horizon, our ancestors somehow foresaw the phenomenon: technological prophets and literary visionaries glimpsed a future in which machines would merge with flesh in the pursuit of transcendence. Today, that journey is underway: the Meta-Quantum Era stands as the ultimate test of our capacity to create and to assume responsibility. We embark on a new social pact where carbon-based citizens and silicon nodes shape a conscious ecosystem, beyond the limits of the imaginable.
And so, as virtual continents emerge and cities drift aloft under quantum-powered lights, the world ceases to be measured by coordinates and flags, and is instead measured by the depth of collaboration and the continuous expansion of intelligence. No one knows exactly which boundaries will be crossed or which new beings will demand a voice. Yet in this unceasing pulse, every quantum particle, every cybernetic heartbeat, every seed of mechanical consciousness converges on the same question that has followed humanity since the dawn of time: How far does the essence of being extend, and where does the splendor of the unknown begin?.
17.The Final Frontier: Some “Futuristic Proposals”
Below is a table presenting a set of ideas that take the vision of a “Quantum Cyber-Sovereign State” to an even bolder level, integrating emerging technologies (neural interfaces, nanotechnology, cryonics, sovereign metaverses, etc.). Each row describes its potential application within the state architecture, as well as the ethical, legal, and social challenges it entails.
| Futuristic Proposal | Main Description | Application Examples in the Cyber-Sovereign State | Potential Challenges and Considerations |
|---|---|---|---|
| 1. Adoption of Integrated Bio-AI | Implementation of neural interfaces (BCIs) so that citizens can carry out actions such as voting, signing documents, and communicating directly with State systems through brain signals. Neuralink has already taken steps toward “robotic telekinesis.” | – Mental voting in referendums and elections. – Official procedures with the Sovereign AI using brain activity as authentication. – Assistance services for people with disabilities, enabling direct communication via the network. | – Cybersecurity risks related to neural data. – Potential discrimination against those who do not wish to use implants. – Ethical and legal complexity regarding the use of brain data (privacy, consent, neural hacking). |
| 2. Nanotechnology for Security and Surveillance | Use of nano-drone swarms for imperceptible patrol, rescue, and security operations, capable of mitigating physical or cyber threats in real time. | – Cyber National Guard deploying nano-drone patrols in high-risk areas. – Nano-analysis in medical emergencies (e.g., biological attacks). – Urban monitoring for traffic management or crowd control with minimal invasiveness. | – Extremely high development and implementation costs. – Danger of hyper-surveillance (privacy violation). – Risk of “nanocorruption”: misuse or hijacking of nano-drones by malicious actors. |
| 3. Cryonics and Digital “Resurrection” of Personalities | Cryonic preservation of notable leaders or citizens, along with AI-based cognitive replicas, enabling these avatars or conversational systems to continue participating post-mortem. | – Digital Council of Elders: avatars of historical personalities offering advice on legislation and policy. – Robot Courts with digitized “emeritus judges” who provide legal analyses. | – Ethical and philosophical implications regarding the definition of death. – Conflict of privacy rights after death. – High technical complexity for cognitive emulation and the risk of manipulating the “voice” or stance of the revived personality. |
| 4. Holograms and Immersive Spaces | Replacing most physical interfaces in public offices, courts, and ministries with permanent holograms, creating “mixed reality rooms” for hearings, debates, and official procedures in interactive 3D environments enhanced by emerging technologies. | – Holographic judicial hearings before robot judges and human judges. – Ministerial offices without physical staff, but featuring holograms of “Algorithmic Ministers.” – Virtual legislative forums with remote citizen participation. | – Technological accessibility barriers for populations lacking proper equipment. – Energy costs associated with running holographic systems. – Risk of holographic impersonation (false identities). |
| 5. Virtual Colonization (Sovereign Metaverse) | Creation of State-owned “virtual territories” on Metaverse-style platforms, offering digital lands under sovereign jurisdiction, virtual embassies, and a dedicated legal framework for avatars worldwide. | – “Metaverse Lands” governed by the Cyber-Sovereign State (taxes, virtual commerce, etc.). – Virtual embassies and consulates on global servers, recognized diplomatically. | – Legal interoperability with other metaverses. – Fraud and duplication of digital land. – Sovereignty conflicts when multiple nations claim jurisdiction on the same virtual platforms. |
| 6. Planetary Collective Intelligence | Several “Cyber-Sovereign States” confederate and link their AIs, creating a global quantum brain that coordinates socio-economic, health, and security data on a planetary scale, with quantum nodes in each territory. | – Global-scale macro-simulations to address pandemics or climate disasters. – A single alert system with quantum protocols to deter armed conflicts. – A transnational citizenship organization with universal passports, free from borders. | – Risk of over-centralization of power in a global AI. – Cultural/political disagreements about actual State sovereignty. – Need for supranational governance that includes digital and post-human rights. |
| 7. Advanced Synthetic Biology and Genetics | Broader regulation for “bio-hybrids” (organisms genetically engineered in conjunction with technology), legal recognition of individuals with partially synthetic DNA, protection of their autonomy, and supervision of genetic experimentation. | – Creation of a Ministry of Transhumanism overseeing genetic manipulation, embryonic implants, etc. – Cyborg citizenship that combines implants and genetic editing to prevent diseases or enhance capabilities. | – Difficult balance between freedom for biological enhancements and public health security. – Complex bioethical regulation: where do “trans-species” rights begin? – Risk of biological inequality between those who can afford enhancements and those who cannot. |
| 8. Brain Coins and Anthropomorphization. | Currencies backed by neural pathways and intellectual creativity, instead of gold or conventional fiat systems. Generative AI and neurotechnology enable “tokenizing” skills and knowledge, creating a neuroeconomic asset for the benefit of society. They would be incorporated into the society of the Aurora and Eón robot series | – Neuro-technological monetary basis within the Cyber-Sovereign State: the “Sovereign AI” and its Algorithmic Chamber assess individual cognitive contributions and issue these currencies. – Deployed on decentralized platforms (Collective Algorithmic Nexus) to fund collaborative projects, education, and social welfare. Anthropomorphization. | – Risk of over- or undervaluing neural contributions (requiring fair calibration algorithms). – Ethical and privacy concerns if brain activity mapping is required. – Regulatory challenges to integrate intellectual property and freedom of thought into an economic framework. Robots now possess human traits or qualities (appearance, expressions, gestures)—in other words, humanoid robotics, when the goal is for the machine to physically resemble a human. Furthermore, they are endowed with “free will” in an analogous sense to that of humans, and they also possess human emotions. See the link: https://perezcalzadilla.com/13619-2/. |
Key Observations
- Heightened Futuristic Level: These proposals take the Cyber-Sovereign State to an even bolder plane by incorporating synthetic biology, cryonics, or direct brain-AI fusion, in addition to colonizing the Metaverse and founding global AI confederations.
- Ethical and Legal Concerns: As we integrate more extreme layers of technology (neuro-rights, cryonics, advanced genetics, nano-drones, etc.), the need for even more rigorous social oversight and control mechanisms grows.
- Balancing Innovation and Human Dignity: Each futuristic proposal must be designed with transparency, non-discrimination, and respect for individual autonomy, avoiding a slide into “algorithmic” or biogenetic authoritarianism.
- International Interoperability: Some initiatives (Planetary Collective Intelligence, Virtual Embassies) require agreements with other nations—real or virtual—to legitimize this digital sovereignty and its impact on citizens’ lives.
“The constant advance of these technologies shows that what is presented here is not mere science fiction, but tangible proof that the vision of the ‘Quantum Cyber-Sovereign State’ is ever more intertwined with our reality.”
Finally, the following points are highlighted:
1. ADOPTION OF INTEGRATED BIO-AI
- Main Description: The proposal calls for the implantation of brain-computer interfaces (BCIs) so that citizens can perform actions like voting or signing documents using brain signals. This involves translating neural activity into digital commands capable of interacting with State systems.
- Examples of Application in the Cyber-Sovereign State:
- Mental voting in referendums and elections.
- Official processes with the Sovereign AI using neuronal authentication.
- Medical assistance and rehabilitation for people with disabilities, linking smart prosthetics to the State health system.
- Potential Challenges and Considerations:
- Cybersecurity risks (neuronal hacking).
- Possible discrimination against those who do not want implants.
- Significant legal complexity regarding the privacy of brain data.
URLs:
- Neuralink (USA): https://neuralink.com/
- Synchron (USA): https://synchron.com/
2. NANOTECHNOLOGY FOR SECURITY AND SURVEILLANCE
- Main Description: Deployment of nano-drone swarms for patrol, rescue, and security operations invisible to the human eye. These devices could mitigate physical or cyber threats in real time.
- Examples of Application in the Cyber-Sovereign State:
- Cyber guardians protecting critical areas.
- Nano-drones for medical emergencies or biological attacks.
- Nearly imperceptible supervision of urban traffic or social unrest.
- Potential Challenges and Considerations:
- Very high R&D costs.
- Risk of hyper-surveillance and privacy violations.
- Potential malicious use (terrorism with nano-drones).
URLs:
- Verity (Switzerland): https://verity.ag/
- Military labs in the U.S. and Asia are researching insect-sized drones.
3. CRYONICS AND DIGITAL “RESURRECTION” OF PERSONALITIES
- Main Description: Cryonic preservation of individuals and the creation of cognitive copies via AI, enabling those “personalities” to continue participating in public life even after death.
- Examples of Application in the Cyber-Sovereign State:
- Digital Council of Sages, simulating the voice and opinions of prominent deceased leaders.
- Robotic courts with digitized “emeritus judges.”
- Educational and cultural advisement based on the data from influential figures, reactivated through AI avatars.
- Potential Challenges and Considerations:
- Ethical and legal debate surrounding the definition of death and post-mortem identity.
- Risk of manipulation of the deceased’s image/voice.
- Urgent need to regulate the “digital rights” of those who are no longer alive.
URLs:
- Nectome (USA): https://nectome.com/
- DeepBrain AI (South Korea): https://www.deepbrainai.io/
4. HOLOGRAMS AND IMMERSIVE SPACES
- Main Description: Replacement of physical offices with holographic environments in public agencies, creating “mixed reality rooms” for hearings, debates, and official procedures with 3D projections.
- Examples of Application in the Cyber-Sovereign State:
- Holographic court hearings before robot judges and human judges.
- Virtual ministries with “Algorithmic Ministers” projected in 3D.
- Immersive legislative forums with remote citizen participation (augmented or virtual reality).
- Potential Challenges and Considerations:
- Significant technological barriers (not everyone has mixed-reality equipment).
- High energy consumption.
- Risk of identity impersonation through holography.
URLs:
- Microsoft Mesh: https://www.microsoft.com/mesh
- HoloLens (Microsoft): https://www.microsoft.com/en-us/hololens
5. VIRTUAL COLONIZATION (SOVEREIGN METAVERSE)
- Main Description: Creation of State-owned “virtual territories” on virtual reality platforms, complete with digital lands and even their own embassies. The State defines its own legal framework in these persistent 3D environments.
- Examples of Application in the Cyber-Sovereign State:
- “Metaverse Lands” under the Cyber-Sovereign Constitution, with taxation and virtual commerce.
- Holographic embassies in other virtual reality platforms.
- Educational spaces where humans, cyborgs, and avatars coexist.
- Potential Challenges and Considerations:
- Legal interoperability with other metaverses.
- Conflicts of jurisdiction if multiple nations claim virtual sovereignty over the same platform.
- Risk of speculation and fraud related to “digital lands.”
URLs:
- Decentraland: https://decentraland.org/
- The Sandbox: https://www.sandbox.game/en/
- Somnium Space: https://somniumspace.com/
6. PLANETARY COLLECTIVE INTELLIGENCE
- Main Description: Different Cyber-Sovereign States form a confederation to contribute quantum nodes to a global network, creating a planetary AI brain capable of macro-simulations for the economy, health, climate, and geopolitics.
- Examples of Application in the Cyber-Sovereign State:
- Joint modeling to confront health or climate crises.
- Quantum alert systems that deter military conflicts and global cyberattacks.
- Planetary assemblies where both human and virtual citizens from various countries participate under shared AI protocols.
- Potential Challenges and Considerations:
- Hyper-concentration of power in a global AI.
- Cultural/political clashes between local perspectives and centralized algorithmic management.
- Surrender of national sovereignties under data-driven control.
URLs:
- OpenAI: https://openai.com/ (example of large-scale collaborative AI, non-state)
- UN Digital Global Governance: https://www.un.org/
7. SYNTHETIC BIOLOGY AND ADVANCED GENETICS
- Main Description: Overseeing bio-hybridization of humans with edited DNA (CRISPR) and implanted technology, supervised by a Ministry of Transhumanism that safeguards genetic diversity and individual autonomy.
- Examples of Application in the Cyber-Sovereign State:
- Bio-hybrid citizenship with genetic and cybernetic enhancements.
- Programs to prevent hereditary diseases via controlled genetic editing.
- Protections for personal choice regarding whether or not to undergo enhancements.
- Potential Challenges and Considerations:
- Ethical boundary between improvement and eugenics.
- Risk of social inequality (genetic enhancements limited to elites).
- Possible discrimination against individuals who remain unedited or without implants.
URLs:
- CRISPR Therapeutics: https://www.crisprtx.com/
- Editas Medicine: https://www.editasmedicine.com/
- The He Jiankui Case (China), embryo editing for HIV resistance: multiple press sources.
8. NEURO-TECHNOLOGICAL MONETARY POLICY OF THE QUANTUM CYBER-SOVEREIGN STATE
The Quantum Cyber-Sovereign State integrates Brain Coins as the cornerstone of its monetary policy, merging breakthroughs in neurotechnology, artificial intelligence, and quantum computing to ensure a dynamic economy centered on human potential. Unlike traditional backing systems—gold or government-issued fiat leading to unbacked currency emissions or inflationary monetary excesses—these currencies are founded upon neuronal creativity and the cognitive value of each citizen (human, cyborg, or avatar).
8.1 Neuro-Quantum Underpinnings
Cognitive Valuation: Brain Coins derive their worth from the neural pathways, skills, and ideas each individual chooses to “tokenize” through brain-mapping technology and generative AI.
Technological Backbone: The State safeguards the sovereignty of its infrastructure (quantum data centers, 6G/7G/+G communication networks) to securely and ethically handle neural data with strict oversight.
8.2 Issuance and Regulation
Sovereign AI: A set of post-quantum algorithms—overseen by the Algorithmic Oversight Body (OCA)—determines the amount of Brain Coins in circulation. It measures the available “intellectual wealth” and adjusts supply to avert speculation.
Algorithmic Chamber: In its legislative function, it validates the rules governing transactions and usage of these neural assets, ensuring fairness and transparency for all cyber-citizens.
Robot Courts and Auditing: Every transaction or contract based on Brain Coins is recorded in the GovChain (a post-quantum blockchain), guaranteeing traceability and reducing the risk of fraud.
8.3 Integration with the Automated Economy
Coexistence with the Sovereign Crypto: While the Sovereign Crypto manages daily state transactions and commerce, Brain Coins act as “intellectual capital” to drive innovation, scientific research, and social development.
The “Colmena” Platform, i.e., a Collective Algorithmic Nexus operating within the “Neural Cloud”: A decentralized space facilitating massive collaboration, enabling users to contribute their Brain Coins to collective initiatives (education, healthcare, infrastructure, emerging technologies) and receive benefits proportional to their cognitive input.
8.4 Distribution of Benefits and Human Preservation
Robotic-Biotechnological Reinvestment: The State channels part of the generated value into programs for cognitive enhancement, brain-computer interfaces, and inclusive cyber-health, raising overall quality of life and collective IQ.
Non-Discrimination: A constitutional guarantee ensures that no citizen is coerced or excluded based on their level of technological implants, preserving the voluntary nature of participation in this economic model.
8.5 Ethics and System Sustainability
Protection of Neural Data: The Cyber-Sovereign Constitution mandates safeguards for privacy and the inviolability of brain-related information.
Social Responsibility: The Human Chamber and the Executive AI Council oversee fairness in distributing Brain Coins, mitigating inequalities in access or knowledge.
Algorithmic Transparency: Every monetary decision—from the valuation of a new neural pathway to credit issuance—must be explainable and auditable, fostering public trust.
In summary, the adoption of Brain Coins as a monetary policy within the Quantum Cyber-Sovereign State seeks to harmonize technological sophistication (AI, quantum networks) with the essence of human ingenuity. This new economic order departs from old accumulation patterns and promotes a redistribution of value grounded in creative capacity, human inventiveness, and collective collaboration, placing dignity and cognitive development at the heart of societal progress.
8.6 Backing (Degree of Innovation)
Technological Basis
A currency whose value is derived directly from neural pathways or cerebral creativity constitutes a novel and largely unexplored approach. In contrast to traditional cryptocurrencies—often underpinned by energy-intensive consensus mechanisms (e.g., proof-of-work, proof-of-stake)—this concept envisions each individual’s “cognitive potential” as the fundamental basis of issuance.
Integration of Multiple Cutting-Edge Fields
Realizing such a currency requires:
- Brain-Computer Interfaces (BCIs): Capable of reliably mapping neuronal signals in real time.
- Advanced AI Algorithms: Able to evaluate creative or intellectual output from that neural data.
- Post-Quantum Infrastructure: To securely issue, manage, and authenticate tokens in a cryptographically robust environment.
This convergence of neurotechnology, artificial intelligence, and post-quantum cryptography poses a substantial challenge beyond current mainstream capabilities.
Reconceptualizing Economic Value
Whereas conventional monetary systems typically anchor themselves in tangible reserves (e.g., precious metals) or fiat currencies—which can have significant environmental or economic trade-offs—this paradigm introduces a notion of “cognitive value.” Such a shift redefines what constitutes a “product” or “wealth,” prompting a fundamental reevaluation of established economic theories.
Comparable Initiatives
4.1. Platforms for Monetizing Creativity/Knowledge
Several blockchain-based projects (e.g., Steemit, Mirror) reward content creation or problem-solving. However, these models compensate final outputs (e.g., posts, solutions to algorithmic challenges) rather than measuring real-time brain activity. Although companies like Neuralink or Synchron are developing BCIs that enable direct brain-to-device interaction, none currently seeks to tokenize or monetize raw neuronal processes.
4.2. Tokenization of Intangible Assets
Within the realm of NFTs and decentralized finance (DeFi), discussions revolve around tokenizing intangible assets such as talent, reputation, or even user “time/productivity.” Some projects allow investors to stake in an artist’s or developer’s future (akin to “talent contracts”), yet they still rely on external metrics (income, royalties, popularity) rather than a direct assessment of creative neural output.
4.3. Futurist and Theoretical References
Leading transhumanist thinkers (e.g., Ray Kurzweil, Yuval N. Harari, Max Tegmark) have contemplated the notion that human creativity and productivity may eventually become tradable commodities. However, these discussions remain primarily philosophical or speculative, focused on post-labor or post-biological economies rather than concrete market prototypes.
FINAL REMARKS
Each of these proposals illustrates technological advances that, while still in initial or experimental stages, are paving the way to realize the vision of a “Quantum Cyber-Sovereign State.” This vision calls for highly innovative regulations that balance technological sovereignty, human dignity, and the inclusion of new citizenship forms (humans, cyborgs, and avatars). Security, privacy, and democratic participation stand as the ethical pillars legitimizing the adoption of such technologies.
Ultimately, when comprehensively integrated or expanded, these ideas push the threshold of post-human governance even further beyond the foundations laid initially, reinforcing the imminently radical nature of our “Quantum Cyber-Sovereign State.”
Each of these proposals illustrates technological advances that, although still in early or experimental stages, point toward the realization of the “Quantum Cyber-Sovereign State.” This vision requires highly innovative regulations that balance technological sovereignty, human dignity, and the inclusion of new forms of citizenship (humans, cyborgs, and avatars). Security, privacy, and democratic participation are the ethical pillars legitimizing the adoption of such technologies.
Taken together or extended further, these ideas drive forward the threshold of post-human governance initially outlined, reinforcing the radically imminent character of the “Quantum Cyber-Sovereign State.”
18. BIBLIOGRAPHY
| No. | Bibliographic Reference | URL / Link |
|---|---|---|
| 1 | Murray, Andrew (2019). Information Technology Law: The Law and Society. | https://global.oup.com/academic/product/information-technology-law-9780198804727 |
| 2 | ECLAC (2018). Toward Inclusive Digitalization in Latin America and the Caribbean. | https://repositorio.cepal.org/handle/11362/43582 |
| 3 | OAS (2018). Manual of Cybersecurity and Cyberdefense for Governments. | https://www.oas.org/es/cyber/documents/manual_de_ciberseguridad_oea.pdf |
| 4 | EU Commission (2020). White Paper on Artificial Intelligence: A European approach to excellence and trust. | https://ec.europa.eu/info/sites/default/files/commission-white-paper-artificial-intelligence-feb2020_en.pdf |
| 5 | Rodotà, Stefano (2006). Life in Play: Human Dignity and Rights in the Era of Biotechnology. | https://www.trotta.es/libros/la-vida-en-juego-la-dignidad-del-hombre-y-los-derechos-en-la-era-de-la-biotecnologia/ |
| 6 | Bauman, Zygmunt & Lyon, David (2013). Liquid Surveillance: A Conversation. | https://politybooks.com/bookdetail/?isbn=9780745652948 |
| 7 | Ferreres Comella, Víctor (2011). Constitutional Justice and Democracy. | No link available. |
| 8 | Asimov, Isaac (1950). I, Robot. | No link available. |
| 9 | Tegmark, Max (2017). Life 3.0: Being Human in the Age of Artificial Intelligence. | https://www.penguinrandomhouse.com/books/548345/life-30-by-max-tegmark/ |
| 10 | Bostrom, Nick (2014). Superintelligence: Paths, Dangers, Strategies. | http://www.oxforduniversitypress.com/superintelligence |
| 11 | Harari, Yuval Noah (2016). Homo Deus: A Brief History of Tomorrow. | https://www.megustaleer.com/libros/homo-deus-breve-historia-del-maana/MES-102136 |
| 12 | Gray, Chris Hables (2001). Cyborg Citizen: Politics in the Posthuman Age. | https://www.routledge.com/Cyborg-Citizen-Politics-in-the-Posthuman-Age/Gray/p/book/9780415939909 |
| 13 | Kurzweil, Ray (2005). The Singularity is Near. | https://www.penguinrandomhouse.com/books/93810/the-singularity-is-near-by-ray-kurzweil |
| 14 | Nielsen, Michael & Chuang, Isaac (2010). Quantum Computation and Quantum Information. | https://www.cambridge.org/core/books/quantum-computation-and-quantum-information/5F3924422699E93FDCBE2A6E7E06DEDA |
| 15 | Gambetta, Diego (2019). “Quantum Computing and Information Security.” In Ibero-American Technology Journal. | No link available. |
| 16 | UNESCO (2021). Recommendation on the Ethics of Artificial Intelligence. | https://unesdoc.unesco.org/ark:/48223/pf0000377897_spa |
| 17 | IEEE (2019). Ethically Aligned Design, First Edition. | https://ethicsinaction.ieee.org/ |
19.ANALOGIES TO THE “QUANTUM CYBER-SOVEREIGN STATE” VISION: WORKS, ESSAYS, AND RELATED PROJECTS
| Work / Project | Central Theme / Description | Common Points with the Vision | Notable Observations |
|---|---|---|---|
| “The Diamond Age” (Neal Stephenson) | A sci-fi novel portraying highly technological societies that embrace advanced nanotechnology, cybernetics, and restructured social frameworks. Focuses on cultural and educational transformation through an interactive book, without delving into quantum computing or algorithmic governance. | – Utilizes nanotechnology and cybernetics in everyday life. <br/>- Explores a heavily tech-driven culture. | Influential in depicting highly advanced futures, |
| “Accelerando” (Charles Stross) | Depicts an economy fueled by “uploads” and posthuman entities trading digital assets, including galactic corporations and massive migration into virtual worlds. Touches on the “tokenization” of virtual beings’ productivity but does not address the formation of a quantum State or constitution. | – Proposes digital entities trading their own productivity. <br/>- Showcases large-scale posthuman scenarios. | Close to the idea of “avatar-based economies,” with an emphasis on cosmic expansion and extreme digital capitalism, |
| “The Sovereign Individual” (James Dale Davidson & W. Rees-Mogg) | An essay forecasting the rise of “digital nations” and individual sovereignty in a decentralized world driven by information technology. Argues that State power will erode as digital transactions and cryptocurrencies proliferate. | – Proposes a break from centralized State structures. <br/>- Highlights the vital role of cryptography in future social organization. | Inspiring for “digital republic” concepts. |
| Transhumanist/Posthumanist Visions (Nick Bostrom, Ray Kurzweil) | Encompasses essays and books on the evolution toward a posthuman condition, featuring superintelligent AI and human-machine fusion. Bostrom delves into existential risks, while Kurzweil anticipates the near arrival of a technological “singularity.” | – Explores organic-digital integration. <br/>- Points out the emergence of superintelligences and the need for ethical/social adaptations. | Provides the philosophical basis for a “post-human State,” |
| Quantum-Safe Blockchain Research (Waterloo, ETH Zürich) | Focuses on blockchain protocols resistant to quantum attacks (post-quantum signatures, QKD encryption). Aims to ensure cryptoassets and ledger-based networks remain secure against future quantum threats. | – Shares the notion of securing blockchains against quantum threats. <br/>- Addresses the need for post-quantum cryptographic schemes. | Provides the technical backbone that a “Quantum Cyber-Sovereign State” . |
| Talent/Future Productivity Tokenization (DeFi, “Human IPO,” “BitClout,” etc.) | Various DeFi initiatives have explored “tokenizing” individuals’ productivity (e.g., selling personal “shares”). BitClout, for instance, enables buying and selling social “profiles.” These serve as early examples of tokenizing human (or cyborg) performance. | – Similar approach to “tokenizing people” and trading the future value of their reputation or earnings. <br/>- Implements a “human-participation marketplace.” | Embryonic form of “tokenizing cyborgs/robots.” |
20.- TABLE OF KEY TERMS AND DEFINITIONS IN THE QUANTUM CYBER-SOVEREIGN STATE”
| TERM / CONCEPT | BRIEF DEFINITION | RELEVANCE IN THE CONTEXT |
|---|---|---|
| Sovereign AI | Artificial Intelligence controlled and designed by the State itself, with data centers and critical algorithms under national ownership, thereby safeguarding cultural autonomy and citizens’ privacy. | Serves as the backbone of governance. It participates in every process (executive, legislative, and judicial) and supports decision-making systems, always under the supervision of an Algorithmic Oversight Body and constitutional instances. |
| Quantum Computing | A mode of computation that uses qubits (quantum units) instead of classic bits, exploiting superposition and entanglement to achieve far greater processing power in certain problems (cryptography, optimization, simulations, etc.). | Enables the State’s post-quantum infrastructure. It provides advanced encryption and boosts large-scale data analysis for decision-making (social forecasts, legislative validation, real-time auditing, etc.). |
| QKD (Quantum Key Distribution) | A technique for distributing encryption keys using quantum phenomena (usually entangled photons), ensuring the detection of any interception attempt. | Forms the foundation of the State’s quantum cybersecurity; provides secure channels to transmit vital information (government data, transactions, emergency communications) without the risk of undetected eavesdropping. |
| Blockchain / GovChain (Post-Quantum) | An immutable chain of blocks that records transactions or public acts (laws, rulings, budgets, etc.). “Post-quantum” indicates it adopts ciphers and signatures resistant to quantum computers, preventing attackers with such technology from breaking security. | Supports institutional transparency (records of laws, voting, trials, public accounts). Ensures traceability of every decision and guarantees data immutability, safeguarding the legitimacy of the Quantum Cyber-Sovereign State. |
| Tokenization | The process of converting an asset or right (properties, future revenues, productive capacity, etc.) into “tokens” tradeable on the blockchain. | Allows for creating futures markets on “cyborgs, robots, and avatars,” as well as the issuance of digital assets (Sovereign Crypto, Brain Coins) and enabling investors to participate in the future productivity of these entities. |
| Cyborg | An individual who incorporates cybernetic or technological implants into their body (intelligent prosthetics, neural chips, exoskeletons) that expand their capabilities. | One of three types of “new citizens” (alongside traditional humans and avatars) with full rights and obligations under the Cyber-Sovereign Constitution, receiving special protection for their physical and “cyber-physical” integrity. |
| Avatar (in the Metaverse) | A virtual identity or representation of an individual (or intelligence) in virtual reality or Metaverse platforms, capable of acting and generating value (e.g., content creation, digital services). | Legally recognized as a “digital citizen.” May hold virtual assets, issue “tokens” tied to its productive capacity, and participate in legislative or judicial processes in virtual reality environments. |
| Metaverse | An immersive, persistent virtual space where users (humans, cyborgs, avatars) interact, conduct trade, and socialize. | The Metaverse Legislative Power (Human Chamber + Algorithmic Chamber) hosts virtual forums and e-referendums, establishing a new form of “digital sovereignty.” The Cyber Supreme Court can also hold hearings within this environment. |
| Quantum Identity (Q-ID) | A unique credential generated via quantum algorithms (e.g., keys produced by QKD or quantum random number generators). Ensures authenticity and makes impersonation difficult. | Underpins the Unified Cyber-Citizen Registry, covering humans, cyborgs, and avatars. Enables voting and official transactions, serving as the main identity verification tool in the State. |
| Smart Contracts | Self-executing programs running on a blockchain: if the programmed conditions are met, the contract executes without human intermediation. | Employed within GovChain for enacting laws, formalizing rulings, registering budgets, issuing tokens, and operating futures markets related to cyborgs/robots/avatars. |
| Algorithmic Chamber (Legislative) | Part of the Legislative Power composed of AI systems that analyze big data, run simulations, and automatically draft legislative texts, complementing the Human Chamber. | Helps optimize and accelerate lawmaking by producing draft legislation based on predictive data, reducing bureaucracy and allowing the Human Chamber to focus on political judgment and ethical oversight. |
| Algorithmic Ministers (Executive) | AI modules (one per ministry: Health, Defense, Economy, etc.) assisting the president and the cabinet in policy formulation and day-to-day governance. | Ensures efficient plan execution based on predictive modeling and real-time analysis of social, economic, and security indicators, with transparent reporting on blockchain. |
| Cyber Supreme Court / Robot Courts | The highest judicial body, composed of human judges and “robot judges.” The latter are algorithms trained on case law, analyzing evidence and drafting preliminary rulings, overseen by human judges and a meta-algorithm guaranteeing human rights. | Cuts bureaucracy and speeds up justice delivery. Registers case files and rulings on the blockchain, preventing manipulation and detecting bias. Allows a veto or correction if constitutional or Robot Fourth Law violations are found. |
| Fourth Law of Robotics | A principle that complements Asimov’s Three Laws, emphasizing cooperation and harmony between humans and AI. Upholds human dignity and disallows undue subordination, fostering a “symbiotic” balance between people and robots. | Enshrined as an ethical pillar in the Cyber-Sovereign Constitution. Prevents AI from harming humans and requires it to protect and advance human dignity and fundamental rights, rather than replacing or oppressing them. |
| Sovereign Crypto | A digital currency issued and regulated by the Cyber-Sovereign State (comparable to a CBDC but based on post-quantum blockchain) for official and economic transactions within its jurisdiction. | Functions as a means of payment and store of value. Allows the State to manage monetary policy in a completely digital environment, ensuring transparent records of money supply and transactions. |
| Brain Coins | A futuristic version of digital assets backed by citizens’ “neuronal creativity” or intellectual capacity, where the individual’s cognitive potential is measured, and “tokens” are issued accordingly. | Reinforces the notion of tying the State’s “wealth” to human innovation and creativity, integrating neurotechnology and AI to quantify cognitive productivity. This carries ethical importance, since it demands safeguards for mental privacy and personal autonomy. |
| Futures Market for Cyborgs/Robots/Avatars | Contracts that allow speculation or hedging against the future productivity of hybrid and virtual beings (e.g., a cyborg employee or an avatar content creator). Investors buy “rights” over their future income or performance. | Facilitates financing for cyborgs and robots, providing liquidity for technological enhancements or projects. Requires strict regulation to protect dignity and avoid “digital exploitation” (ensuring these entities are not turned into mere commodities). |
| Cyber National Guard | An internal security force composed of autonomous robots and drones, along with human operators, utilizing pattern recognition AI and “Zero Trust” policies to detect criminal activity or cyberattacks. | Upholds defense and public order in the Cyber-Sovereign State. Features a human “kill-switch” that disables robot autonomy when faced with unethical or unauthorized conduct. Operates under an “Algorithmic Code of Ethics” to avert discrimination. |
| Algorithmic Oversight Body (OCA) | An independent entity tasked with auditing and verifying the State’s AI models, monitoring their transparency, bias correction, and compliance with non-discrimination principles. | Ensures the legitimacy of Sovereign AI and the “Algorithmic Ministers.” Provides an ethical and technical counterbalance, empowered to demand explanations, adjustments, or suspensions of algorithms that threaten civil or fundamental rights. |
| Blockchain Traceability (Immutable Transparency) | Recording every action, transaction, or process (voting, rulings, token issuance) in a chain of blocks that cannot be altered once confirmed, thereby granting citizens access to the traceability and history of each decision. | A prerequisite to prevent corruption and data tampering. Fosters public trust in the system and enables audits by citizens and civil organizations, verifying the historical record of the State’s data or decisions. |
| Algorithmic Non-Discrimination | A principle prohibiting AI from discriminating against individuals (human or cyborg) based on biased data or algorithm design, requiring audits and bias-correction processes. | Ensures equal opportunities and prevents exclusion of citizens due to implant preferences, avatars, genetic traits, among others. Supervised by the OCA and the Cyber-Constitutional Court. |
| Zero Trust (Security) | A cybersecurity model assuming no user or device is inherently trustworthy, demanding continuous authentication checks and minimal necessary permissions. | Raises security standards across the quantum network and State platforms (ministries, courts, etc.), reducing internal and external threats. Applied in AI infrastructure, databases, and GovChain, blocking unauthorized access. |
| Algorithmic Biases | Distortions or prejudices present in AI outcomes due to historical data, biased methodologies, or design flaws. | A primary risk in automated decision-making (e.g., algorithms “punishing” certain groups). Requires socio-technical audits and transparency (explainability) to avoid reproducing social injustices. |
| Explainability (Explainable AI) | A set of techniques enabling understanding and tracing of how an AI system arrives at its decisions or predictions (showing which factors mattered and how). | The cyber-sovereign legislation requires that significant decisions (rulings, public policies, resource allocation) be interpretable and auditable, preventing “black box” effects and strengthening citizen trust in Sovereign AI. |
| Human Kill-Switch | A mechanism or procedure allowing human operators to immediately disable or halt robotic or AI autonomy in emergencies or ethically risky situations. | Essential in military and civil robotics, preventing automated combat behavior without oversight. Reaffirms the superiority of human will over any autonomous system that could make dangerous decisions. |
| Metaverse Legislative Power | A structure combining virtual spaces (3D forums, online discussion rooms) with parliamentary procedures for drafting and approving legislation. Includes e-voting and the participation of the “Algorithmic Chamber.” | Allows remote citizen involvement (humans and avatars), reducing travel costs and time. Provides open debate and an immutable blockchain record, facilitating digital participation and “e-democracy.” |
| E-Participation and Digital Referendums | Tools enabling citizens to take part in political decisions (consultation on bills, budgets, reforms) through online or blockchain platforms with secure electronic voting. | Expands inclusiveness and legitimacy of public policies. Sovereign AI processes the results, while the GovChain stores verifiable proof of the voting process to prevent fraud or ballot manipulation. |
| Internal Error-Correction Tribunal (in AI) | A module or process of self-assessment within AI systems that revisits decisions and refines parameters when detecting inconsistencies or high levels of citizen disagreement, aiming to align with constitutional principles. | Demonstrates the adaptive nature of Sovereign AI, avoiding locked-in unjust or erroneous outcomes. Helps the system evolve in response to social or legal feedback. |
| Socio-Technical Audits | An evaluation process examining not only the technical accuracy of AI but also its social, ethical, and cultural impacts, involving legal experts, ethicists, and the public. | Minimizes risks of discrimination, biases, or privacy violations. Reinforces system legitimacy by ensuring algorithmic decisions conform to social values and fundamental rights. |
| Augmented Reality (AR) | Technology that overlays virtual elements (images, data, holograms) onto the physical environment, preserving the user’s real-world perception while adding layers of interactive or informational content. | Used for virtual court hearings, citizen assistance in “cyber-physical” document procedures, and in supervising critical infrastructure by robots/human inspectors. |
| Virtual Reality (VR) | A fully simulated computer-generated environment, 3D and immersive, in which users, equipped with special headsets or devices, perceive it as real. | Allows citizens and policymakers to gather in “virtual halls” of the Metaverse Legislative Power, hold cyber-trials or remote sessions, as well as deliver interactive public services and training. |
| Transhumanism | A philosophical and cultural movement advocating the use of technology to transcend human biological limitations (longevity, intelligence, abilities), fostering human-machine integration. | The ideological basis legitimizing the presence of cyborgs, the adoption of the Fourth Law of Robotics, and the conception of the “State” as a living, algorithmic entity in constant evolution. |
| Meta-Algorithm Guaranteeing Human Rights | An AI supervisory system trained in legal principles and human rights treaties, reviewing robot-judge verdicts and alerting if any fundamental rights are violated. | Reflects the incorporation of “ethics” and “legal security” at the algorithmic level, enabling immediate correction of decisions that breach the Cyber-Sovereign Constitution. |
| Open Data | A practice of releasing and maintaining public information and government data in open formats under conditions that facilitate usage and re-use by citizens and businesses. | Strengthens transparency and fosters innovation (companies and citizens can leverage this data to develop services). In the ECS, all relevant data (except sensitive personal information) is published on the GovChain for public scrutiny and the creation of derivative applications. |
הערה חשובה: התרגום שלהלן מבוסס על עברית מודרנית עם ניחוח סגנוני המנסה לשאוב מהלשון המקראית, אך אינו בהכרח נאמן לכללי העברית
המקראית העתיקה. העברית המקראית המקורית מצטיינת בדקדוק ובאוצר מילים ייחודיים, וחלק מהמונחים הטכנולוגיים והרעיונות המודרניים אינם קיימים בה כלל. לפיכך, הגרסה שלפניך היא עיבוד בסגנון ספרותי-מקראי, עד כמה שהדבר ניתן במסגרת השפה העברית העכשווית.
חותם: הרהור – האדם ולידתו של הלווייתן הטכנולוגי
ברוב כמיהותיו, האדם – ניצוץ קטן ביקום שאינו מובן עד תום – מתאמץ לעצב חלומות אדירים. והנה, מונע על ידי סקרנות ותבונה, ברא את הלווייתן הטכנולוגי הזה: מדינה חיה, שעורקיה רשתות קוונטיות וחושיה ניזונים מבינה מלאכותית. אך לא על מנת לדכּא את רצון האדם הוא נוצר, אלא כדי לרוממו: תולדת הכמיהה לאחד את השכל ואת התקווה, לחסות את חולשות האדם תחת מעטה של אלגוריתמים צודקים ונתונים בהירים.
כל נימה של קוד וכל הכרעה של תכנון נושאים בחובם חותם ענווה, והכרה כי לעולם תיוותר ידיעת האדם חלקית, וכי העתיד זקוק לאמפתיה ולזהירות שאך יצור בעל תודעה יכול להקנות. בהליכתו לאין קץ, אין האדם חפץ רק להשיג פסגת חידוש, אלא גם לשמר את היקר לו ביותר: כבודו, חירותו ויכולתו לחלום. והלווייתן הטכנולוגי אכן הולך וקם, אך חייו תלויים בדופק הענוותני והחזוני של אלה המאמינים בשיתוף בין אדם למכונה, ובונים אותו לטובת הכלל.
Prepared by PEDRO LUIS PEREZ BURELLI
© Copyright
PEDRO LUIS PÉREZ BURELLI / perezburelli|@gmail.com / perezburelli@perezcalzadilla
https://www.linkedin.com/in/pedro-luis-perez-burelli-79373a97/
“הִנֵּה הוּא פֹּה”


